Practice Test 2 - AP Computer Science Principles Premium 2024
Practice Test 2
TIME: 120 MINUTES
70 QUESTIONS
1. What should replace so that the program below displays TRUE 10% of the time?
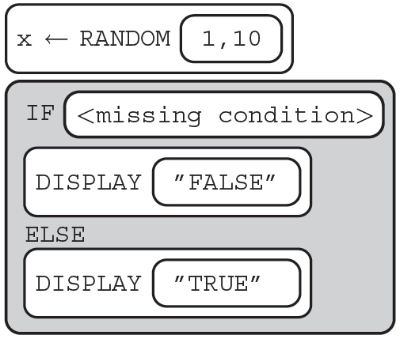
(A) x < 1
(B) x <= 1
(C) x < 9
(D) x <= 9
2. Consider the following code segment, which uses the variables x, y, and z. What will the following program display?
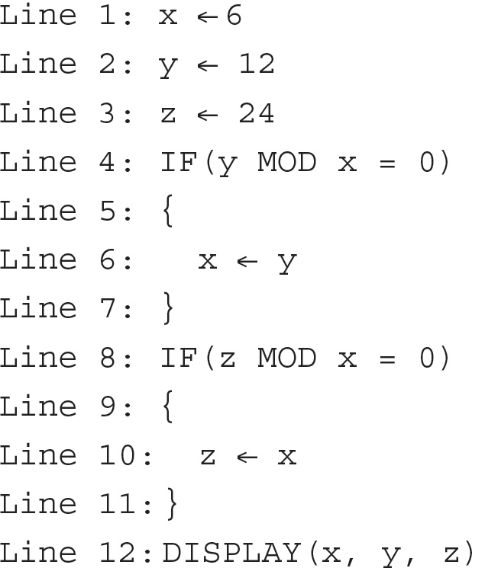
(A) 6 12 24
(B) 12 12 12
(C) 24 24 24
(D) 12 24 24
Use the information below to answer questions 3–7.
A video game played using a home system has released the second game in the series, which uses a mobile phone to play the game. This upgraded game interacts with real-life locations, resulting in a virtual reality experience. The user interacts with the game based on his or her location and the time of day. The game will not work if the user is traveling faster than 3 miles per hour to prevent people from playing while driving. By making events at locations of interests, the video game will expose the user to public artwork, historical sites, and local businesses.
3. Which of the following input data is needed by the upgraded game that was NOT needed by the original game?
(A) Event sensing; an event would be the user pushing a button or screen
(B) GPS location
(C) Age of the player
(D) Picture of the player
4. Which of the following data is not provided directly by the user but is necessary for the upgraded game to operate as described?
(A) GPS location of user
(B) Speed traveling
(C) Location of landmarks used in the game.
(D) User name
5. Which of the following is LEAST likely to be included with the game?
(A) What types of mobile devices can be used
(B) Location of high-crime areas
(C) Location of highly trafficked roads and bridges
(D) What protocols the mobile device uses to connect to the internet
6. Which of the following is considered a potential effect of the mobile game rather than the purpose of the game?
(A) People are exercising.
(B) People are not watching where they are walking and are getting injured.
(C) Social anxiety is decreasing when interacting with other players.
(D) Players are becoming more cultured by visiting artworks.
7. Which of the following is the MOST likely data privacy concern of the upgraded game?
(A) How much time a person spent playing the game
(B) Recording whether the player was speeding when driving to a location.
(C) The player’s score
(D) How many locations the player visited
8. Tickets prices to Fun Land are given below.

A programmer is creating an algorithm to set the ticket price to Fun Land. Which of the following code segments does NOT correctly sets the value of ticketPrice?
(A)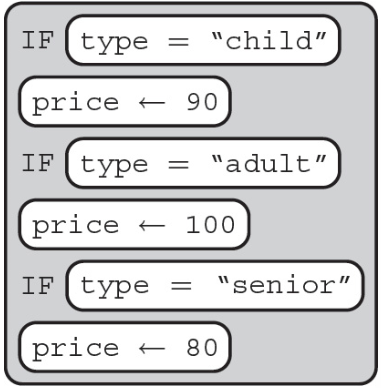
(B)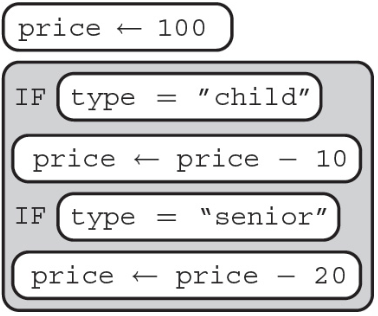
(C)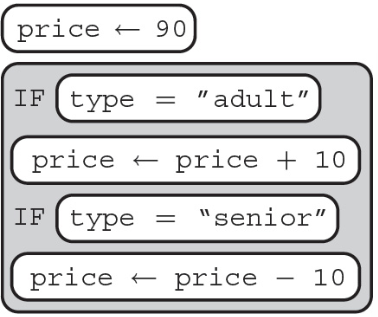
(D)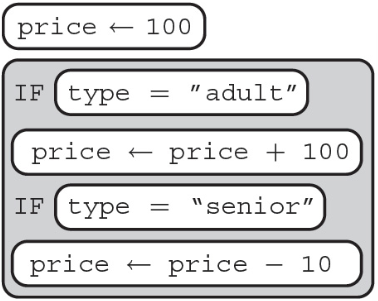
9. The following picture was taken by a smartphone.

Which of the following is NOT metadata?
(A) The average value of the green pixels in the picture
(B) The geographic location where the picture was taken
(C) The date the photo was taken
(D) The filename
10. What will the following algorithm display after running the code below?
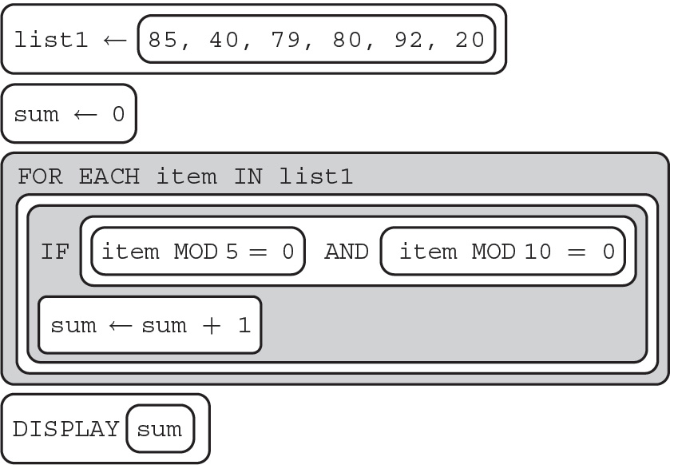
(A) 1
(B) 2
(C) 3
(D) 4
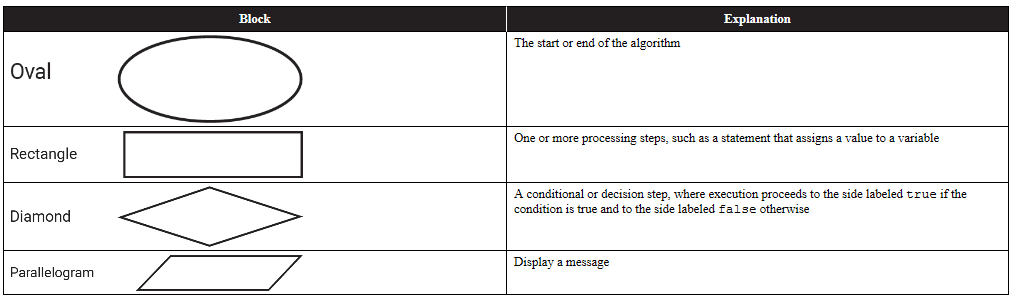
11. A flowchart is a way to represent an algorithm visually. The flowchart below uses the following building blocks.
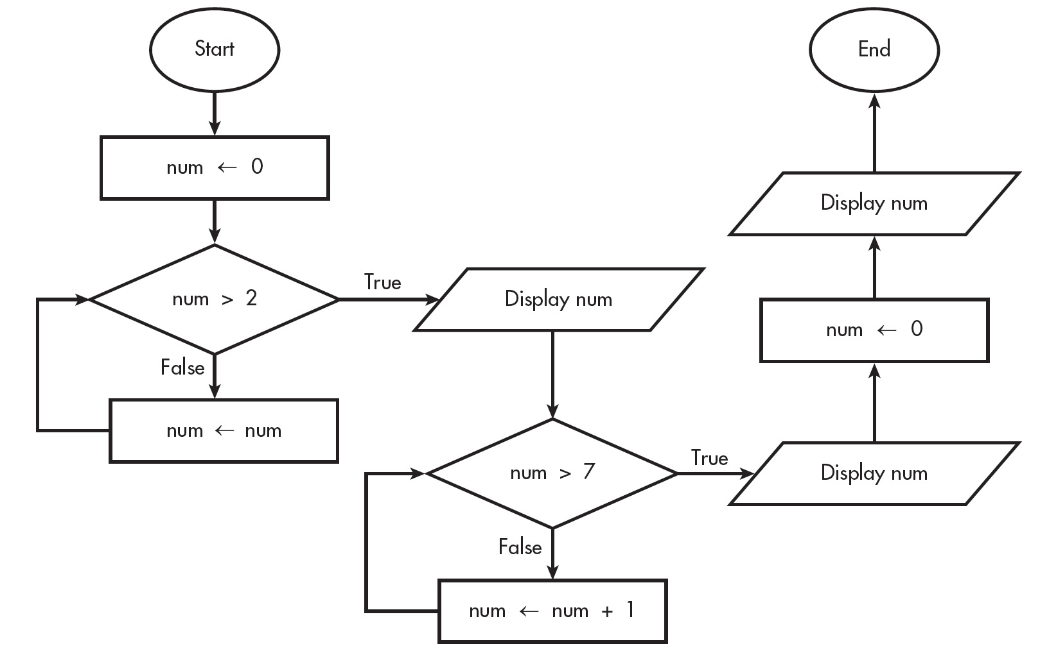
What will the above program display?
(A) 2 8 14
(B) 4 8 8
(C) 3 8 0
(D) Nothing due to an infinite loop
12. Two computers calculate the same equation:
a ← 1/3
A second computer calculates:
b ← 1/3
If a does not equal b, what error has occurred?
(A) Roundoff error
(B) Overflow error
(C) Hexadecimal conversion error
(D) a will equal b on all computers
13. Which of the following data structures is NOT a candidate for a binary search?
(A) A list of students in order of height
(B) A list of numbers from smallest to largest
(C) A list of words from a poem about sunshine in the order they appear in the poem
(D) A list of words in a dictionary
14. Which command can replace to result in the last column of the table shown below?
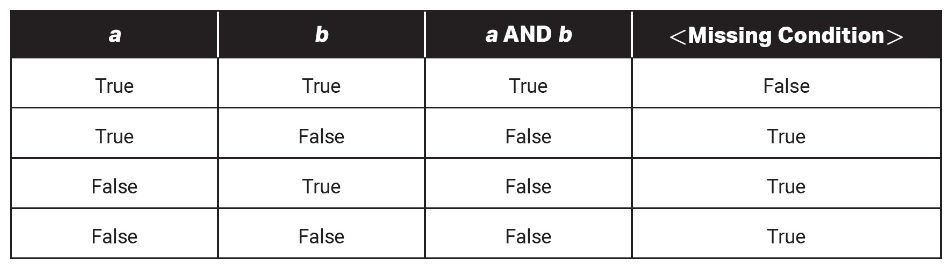
(A) NOT (a AND b)
(B) a OR b
(C) a AND (a AND b)
(D) b AND (a AND b)
15. Which of the following is a trade-off inherent in lossless compression?
(A) The file can be difficult to email and can take up lots of memory storage.
(B) The image quality will be less and will result in a blurry image.
(C) Some of the data will be lost and cannot be recovered.
(D) The number and size of pixels will be less.
16. The following question uses a robot in a grid of squares. The robot is represented by a triangle, which is initially facing right.

What are the possible landing spots for the robot after executing the following program?

(A)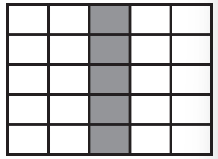
(B)
(C)
(D)
17. Which of the codes below will correctly swap the frog with the bear?
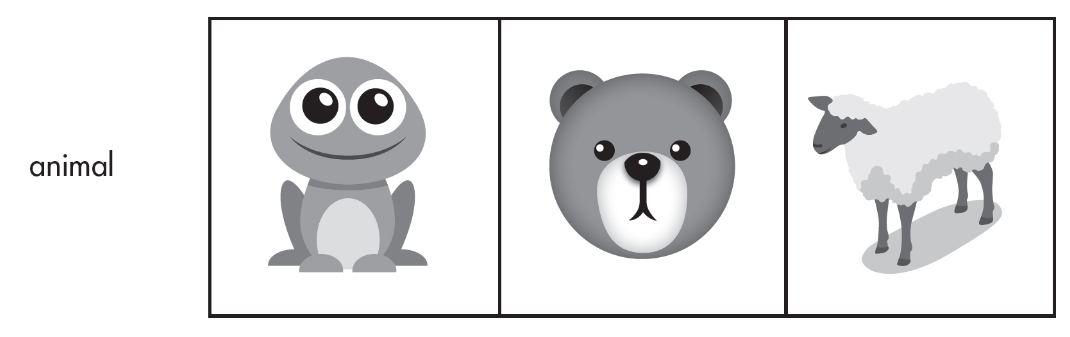
(A) temp = animal[1]
animal[1] = animal[3]
animal[3] = temp
(B) temp = animal[1]
animal[1] = animal[2]
animal[2] = temp
(C) animal[1] = animal[2]
animal[2] = animal[1]
(D) animal[3] = animal[1]
animal[1] = animal[3]
18. What will the following code segment display?
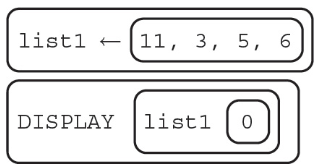
(A) 11
(B) 3
(C) 6
(D) Nothing will be displayed due to an error.
19. An algorithm has n number of steps. Which of the following would be considered a reasonable number of steps?
(A) n!
(B) 4n + 8n2
(C) 100n4
(D) 3n
20. What would be a good use of constants when initializing variables at the beginning of a program?
I. To represent the maximum capacity of people allowed in a restaurant for fire safety
II. To represent the mathematical value of Newton’s gravitational constant
III. To represent how much time is left in a game
(A) I and II only
(B) I and III only
(C) I, II, and III
(D) II and III only
21. What does the following algorithm display?
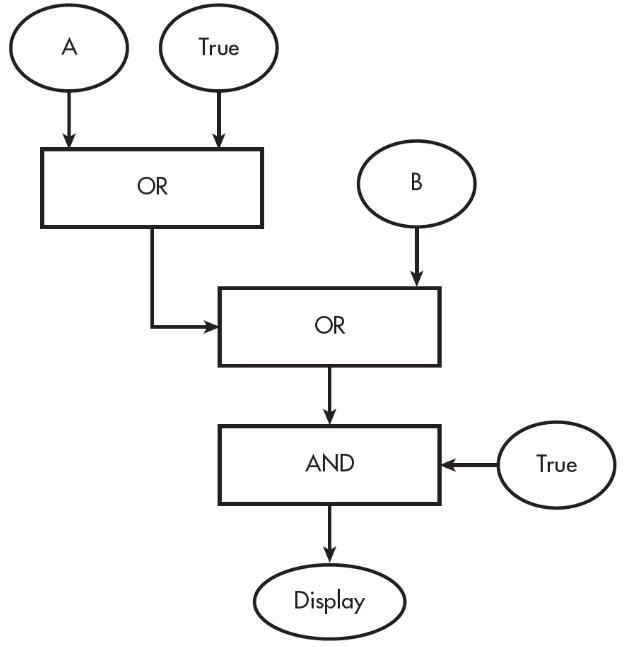
(A) It always displays “True.”
(B) It always displays “False.”
(C) When A is false, the algorithm displays “False.”
(D) When B is false, the algorithm displays “False.”
22. Given two numbers, a and b, the program below is intended to return TRUE if the sum or difference between the two numbers is 13 and FALSE otherwise.
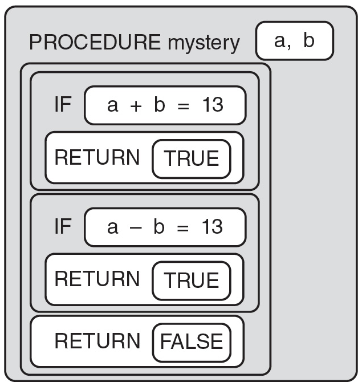
For which of the following procedure calls does the procedure NOT return the intended value?
(A) mystery( 10, 3 )
(B) mystery( 3, 10 )
(C) mystery( 5, 18 )
(D) mystery( 18, 5 )
23. Which of the following can be represented by a single binary digit?
(A) Time
(B) Date
(C) Geographic location
(D) Light on / light off
24. What is displayed as a result of executing the following code segment?
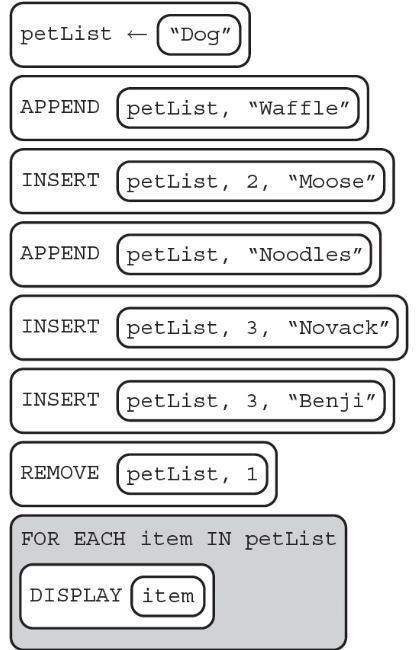
(A) Moose Benji Novack Waffle Noodle
(B) Benji Novack Waffle Noodle
(C) Novack Noodle Waffle
(D) Novack Noodle Benji
25. Lisa took high-definition pictures of her new dog, LilyGoose. She emailed the pictures to her grandmother in Miami. When her grandmother opened the pictures, Lisa’s grandmother noticed that the images were not crisp and the pictures appeared blurry. Which of the following could be a possible explanation for the blurry pictures?
(A) When emailing the pictures, the file was broken down into packets that were not assembled in the correct order.
(B) The picture files were compressed using lossy compression so the file could be small enough to be emailed.
(C) The picture files were compressed using lossless compression so the file could be small enough to be emailed.
(D) Every time you email a picture, some of the picture data will be lost in transmission.
26. Why is cryptography essential to cybersecurity?
(A) Cryptography secures internet communications by ensuring that the files cannot be read if they are intercepted.
(B) Cryptography is used to prevent publicly accessible files on a server from being edited.
(C) Cryptography secures internet communications by preventing a third party from hijacking a connection.
(D) Cryptography does not allow data on a server to be edited by anyone, ensuring the data’s integrity.
27. A 10-megapixel camera takes pictures made up of 10 million pixels. A pixel contains red, green, and blue values between 0 and 255. Photo-editing software adds a value of 40 to every red pixel. If the red value is greater than 255, it saves the red value as 255. What type of transformation is the photo-editing software using?
(A) Lossless transformation
(B) Lossy transformation
(C) Addition transformation
(D) Frequency transformation
28. A robot is shown in the lower-left corner of the following grid and is facing up. Where would the robot end up after running the following code?
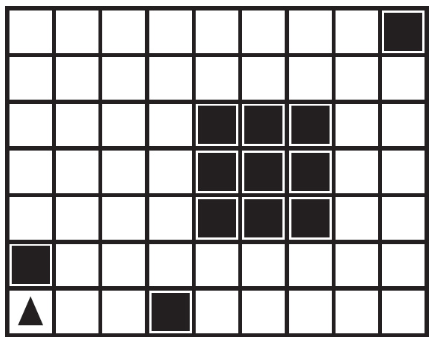
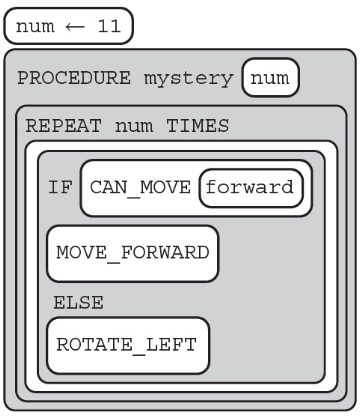
(A)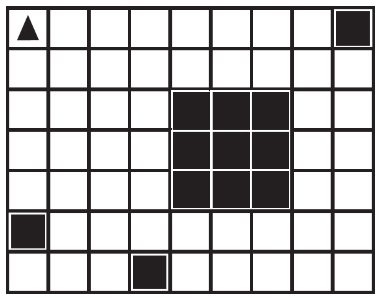
(B)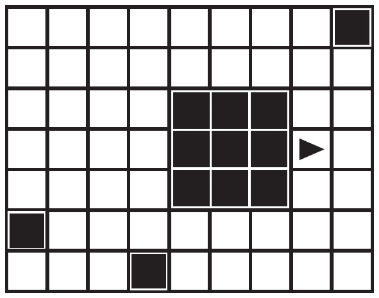
(C)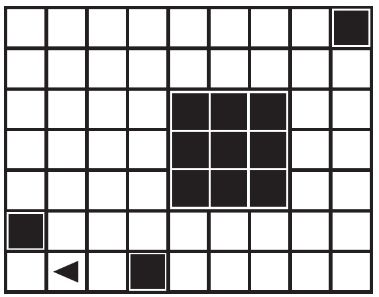
(D)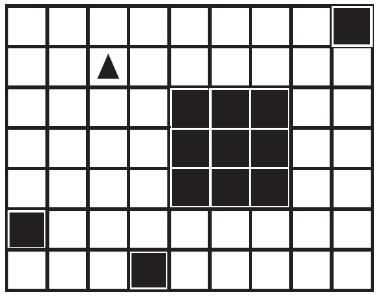
29. What is the % chance this robot will run the following code segment without hitting a wall?
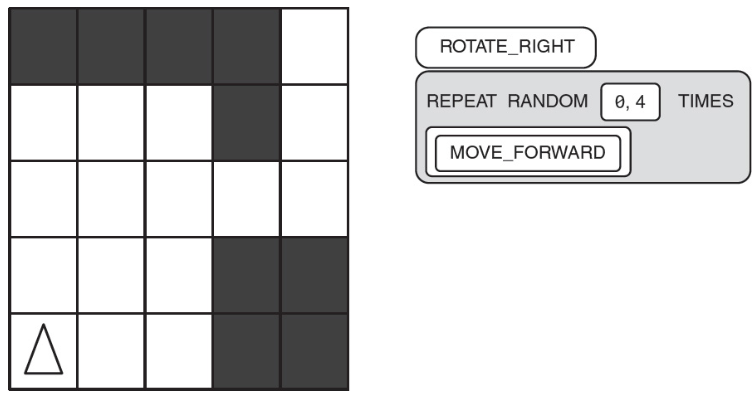
(A) 70%
(B) 60%
(C) 40%
(D) 10%
30. The following code segment is intended to return true if both a and b are divisible by 3 and false otherwise.
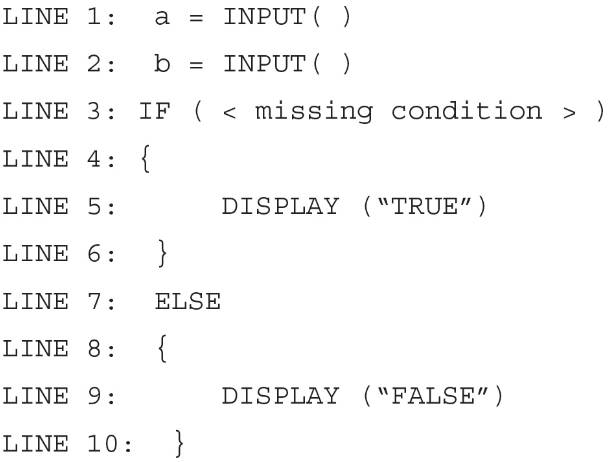
What can replace in line 3 to make the code segment work as intended?
(A) ( a MOD b = 0)
(B) ( a MOD 3 = 0 AND b MOD 3 = 0 )
(C) ( a MOD 3 = 0 OR b MOD 3 = 0 )
(D) ( a / 3 = 0 OR b / 3 = 0 )
31. What is displayed after running the algorithm below?
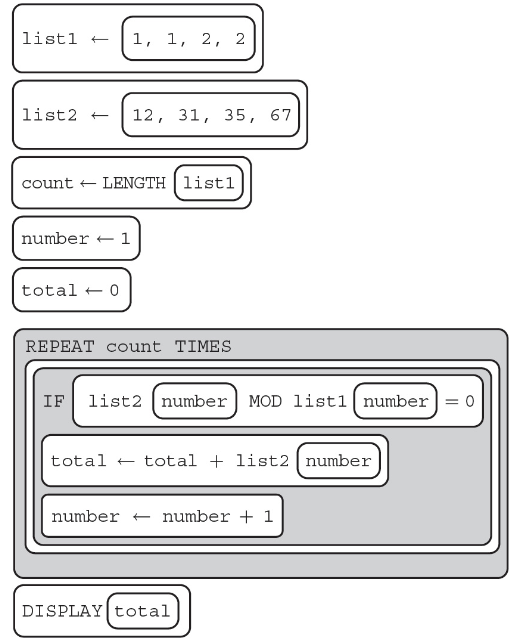
(A) 145
(B) 133
(C) 43
(D) 12
32. Which of the follow can NOT be stored using a binary sequence?
(A) High-definition picture
(B) Analog sound signals
(C) Digital sound signals
(D) A Boolean value
33. An algorithm compares the user-inputted number number to the randomly selected number randomNumber and calls the method checkForInEquality( ) if the two values are different. What should replace in the following algorithm?

(A) IF(number = randomNumber)
(B) IF(number = true AND randomNumber = drawing)
(C) IF(number ≠ randomNumber)
(D) IF(number = true OR randomNumber = true)
34. A common type of heuristic algorithm for chess is alpha-beta pruning. This algorithm evaluates moves but automatically stops if the current move is proven to be worse than the current “best solution.” In addition, if a certain early step is found to be bad, any moves involving that step are also ignored, regardless of whether they have already been tested. Why is this used?
(A) This method will always procure the best solution because all moves with early flaws are ignored.
(B) Finding the best solution could take a long time, so ignoring certain branches that appear to be useless means that fewer solutions need to be checked.
(C) This method never works, but it requires far fewer resources than other algorithms.
(D) Finding the best solution requires far more computer power with this method, which makes it more likely to be accurate.
35. The algorithm below should display the total value contained in list1, not counting the value 13. For example, if list1 contained [2, 13, 4], the algorithm should display 6. What line of code can replace so the algorithm will work as intended?
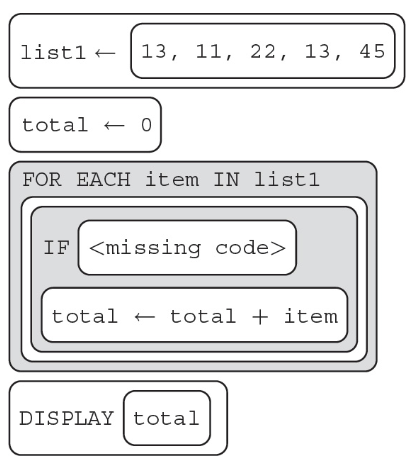
(A) list1 = 13
(B) item = 13
(C) list1 ≠ 13
(D) item ≠ 13
36. For the following data structure, which search algorithm would work as intended to find the value 35?
numbers[1, 43, 23, 65, 76, 34, 33, 12, 94, 576, 55, 35, 3456, 3, 25854, 2357, 1, 4, 0, 43]
(A) Linear search
(B) Binary search
(C) Bubble sort
(D) Insertion sort
37. How many lines need to be cut to isolate computer E from computer C completely?
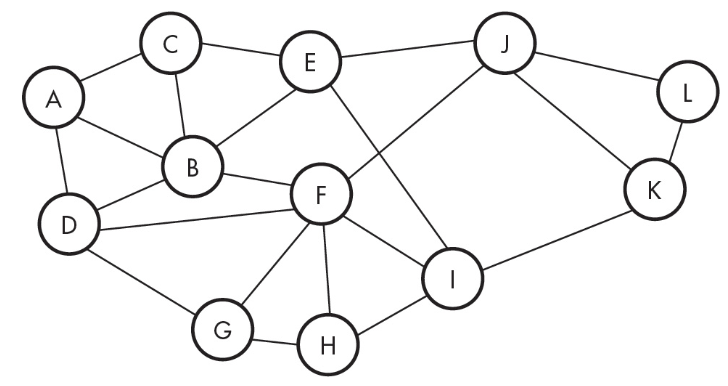
(A) 0
(B) 3
(C) 6
(D) 8
38. Data traveling in the internet is broken down into small chunks of data called packets. What protocol guides the rules about how data are subdivided into packets before transmission?
(A) TCP
(B) DNS
(C) FTP
(D) HTTP
39. Which of the following is NOT indicative of a phishing attack?
(A) A professional organization that the user is a member of asks in an email to click on a link in order to rectify a discrepancy with their account. The email resembles previous legitimate official correspondence.
(B) An email with the user’s personal information, including the user’s name, position, company, and work phone number, directs the user to click a link to input his or her social security number to verify that the user is accurate.
(C) An email asks the user to call the phone number on the back of his or her credit card to verify purchases made in the past 24 hours.
(D) A virus pops up on your computer asking the user to call a phone number to protect his or her IP address from hackers.
40. Which of the following is a cause of the digital divide?
(A) Lack of access to the technology due to affordability
(B) Lack of knowledge on how to use technology
(C) Lack of access to technology due to location
(D) All of the above
41. A fast food company selling burgers wanted to increase speed at the drive thru. The company created a simulation that showed a decrease in wait time by 20% if it implemented a touchscreen ordering system instead of using employees to take orders. When the restaurant implemented the simulation in a real-world situation, the wait time did decrease; however, the overall sales also decreased by 40%. What could have been the reason for the failure?
(A) The simulation had considered all variables.
(B) The simulation might not have considered the human preference for ordering food from people instead of using a touchscreen.
(C) The simulation worked as intended.
(D) Wait time and sales are directly proportional; therefore, the simulation worked as intended.
42. The following program is intended to display the string “789”. What type of error will the following procedure cause?
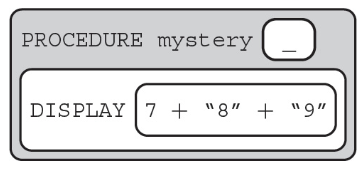
(A) Logic error
(B) Syntax error
(C) Runtime error
(D) No error
43. What is the minimum number of searches for a binary search using an ordered list of 100 numbers?
(A) 0
(B) 1
(C) 8
(D) 100
44. What is the minimum number of binary digits needed to store the number 56?
(A) 1
(B) 3
(C) 5
(D) 6
45. Which of the following are benefits to having information be easily accessible and changeable?
I. Information can be easily found by researchers and citizens, who can improve experimental and investigative findings.
II. Information can be easily found by students, who can use it to improve their understanding of a topic.
III. Information can be easily checked by third parties, which ensures that it is always correct and up to date.
(A) I only
(B) I and II only
(C) II and III only
(D) I, II, and III
46. In what order will the numbers appear after running the algorithm below?

(A) 5, 7, −6, 7
(B) 5, 6, −5, 6
(C) 5, 6, 3, 3
(D) 5, 7, 4, 3.5
47. A certain computer has a single central processing unit. The following table indicates the amount of time each of three processes take to execute on a single processor. Assume none of the processes are dependent on any other process.
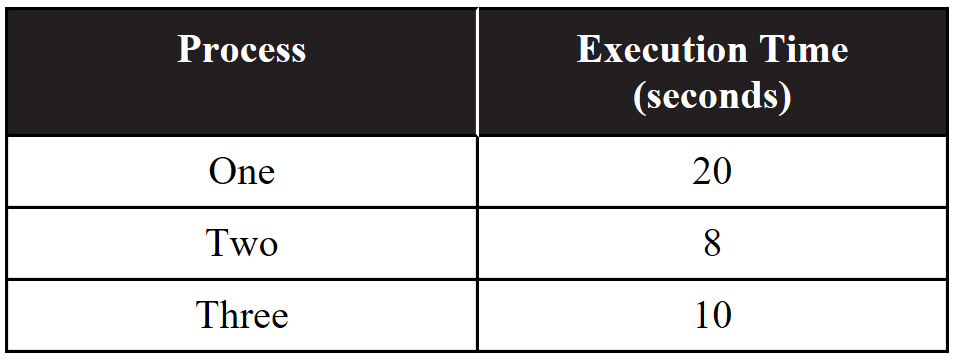
Which of the following best approximates the minimum possible time to run all three processes in series?
(A) 8 seconds
(B) 10 seconds
(C) 20 seconds
(D) 38 seconds
48. The question below uses a robot and a grid of squares. The robot is represented as a triangle, which is initially in the bottom-left square facing toward the top of the grid.
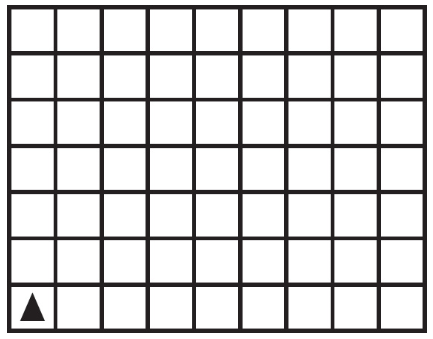
The following algorithm is run on the robot above.

Which of the following are possible landing spots for the robot?
(A)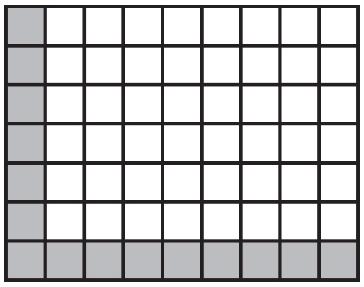
(B)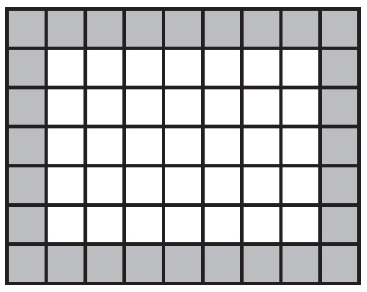
(C)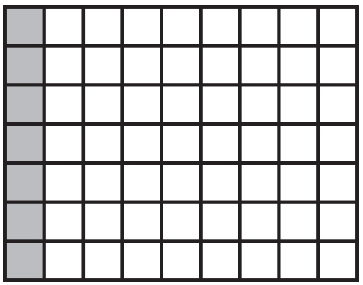
(D)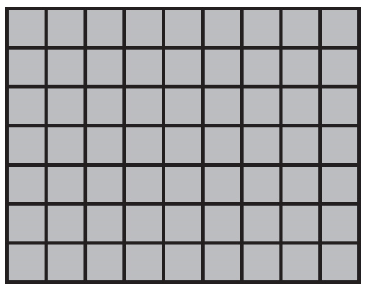
49. What role does a compiler have in processing a high-level language?
(A) The compiler ensures that the program has no runtime errors.
(B) The computer cannot directly understand high-level languages. So an intermediate program, such as a compiler, is needed to translate the code into machine code so that the computer can understand.
(C) The compiler checks for updates and installs programs onto the computer.
(D) The compiler speeds up the run time of a program.
50. What is displayed after the following algorithm is run?

(A) 132
(B) 100
(C) 50
(D) 32
51. What could a single binary value represent?
(A) Volume on a radio
(B) Temperature in degrees Celsius
(C) If a light is on or off
(D) Time
52. Which of the following Boolean expressions is equivalent to NOT(A AND B ) ?
(A) NOT(A) AND NOT(B)
(B) NOT(A) OR NOT(B)
(C) A AND B
(D) A OR B
53. A certain computer has two identical central processing units that can run in parallel. Each processor can run only one process at a time, and each process must be executed on a single processor. In this problem, processes four and five must be run in series, while processes one, two, and three can all run in parallel. The following table indicates the amount of time needed to execute each process on a single processor.
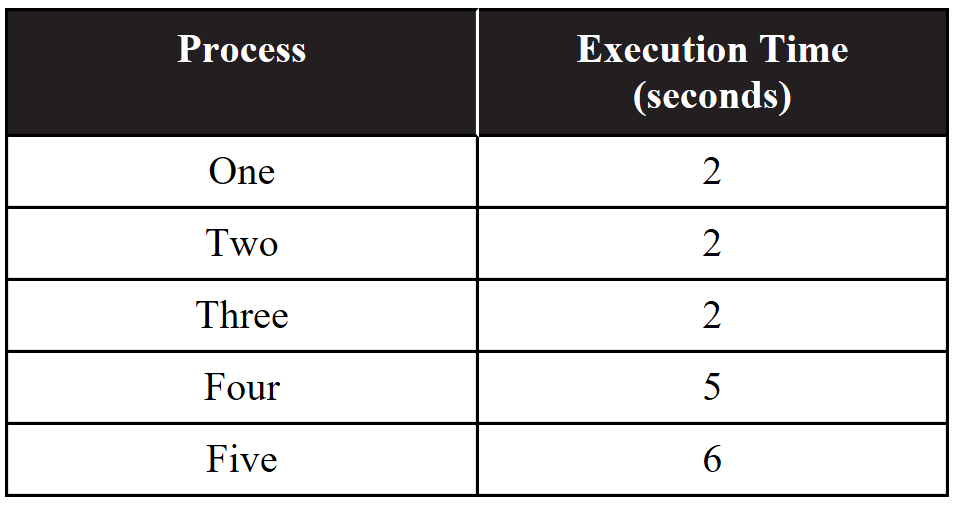
Which of the following best approximates the minimum possible time to run all five processes in parallel?
(A) 1 second
(B) 9 seconds
(C) 13 seconds
(D) 15 seconds
54. When sending a picture from your phone to your friend’s phone using a mobile application, what is true about the packets of information sent?
(A) Packets are sent by the quickest path possible in the correct order.
(B) Packets are sent in multiple paths and can be received out of order.
(C) Packets are received in the order that they are sent.
(D) All of the above.
55. Which of the following is true about redundancy on the internet?
I. Redundancy slows down packets traveling from a sending computer to a receiving computer.
II. Redundancy allows for adding new devices to the network without disrupting traffic.
III. Redundancy makes the internet fault tolerant.
(A) I only
(B) I and II only
(C) II and III only
(D) I, II, and III
56. What should replace in order to make the following program return True when the first element of the array is equal to the last element of the array?
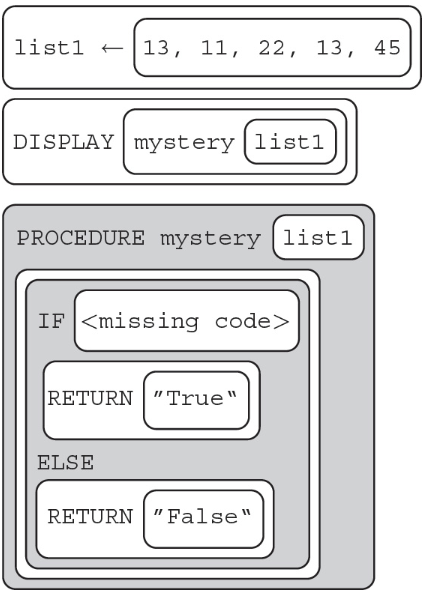
(A) (list1 = list1)
(B) (list1[0] = list1[1])
(C) (list1[1] = list[LENGTH(list1)]
(D) (list1[0] = list1[LENGTH(list1) – 1])
57. Which of the following test cases will NOT find the maximum number in the list?
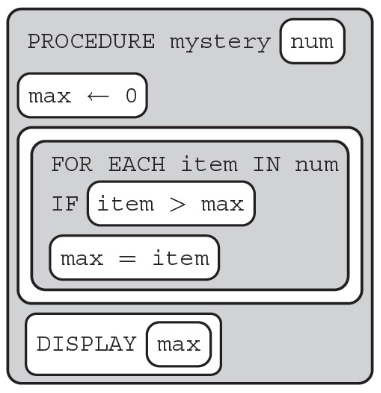
(A) list1[23, 67, 3]
(B) list1[0, 0, 0, 0]
(C) list1[−23, −67, −3, −7]
(D) list1[4]
58. What will the program segment display?
a ← 34
b ← a − 10
c ← a + 65
d ← a + b
e ← a MOD b
f ← c MOD d
g ← e MOD f
DISPLAY(g)
(A) 99
(B) 34
(C) 3
(D) 2
59. Is a binary search always the fastest search when searching for a number in a sorted list?
(A) A binary search is always faster with a sorted list.
(B) No, the first pass of a linear search has a chance of finding the correct number more quickly than does a binary search.
(C) For a large list, binary searches are always faster.
(D) For a large list, linear searches are always faster.
60. What is an example of a way that a “smart grid” could assist with human capabilities?
(A) The grid could control the temperature of an A/C or a heating unit directly.
(B) The grid could prevent blackouts altogether.
(C) The grid could distribute power in the most efficient manner possible, ensuring that all users are capable of using power.
(D) The grid could ensure that all computers on it are properly updated.
61. Which of the following would NOT make a problem unsolvable?
(A) An algorithm can answer the problem with only “yes” or “no.”
(B) An algorithm could take too long to find the solution.
(C) An algorithm tends to produce an incorrect answer with certain input values.
(D) An algorithm provides an output in floating-point decimal form.
62. What will the following code segment display?
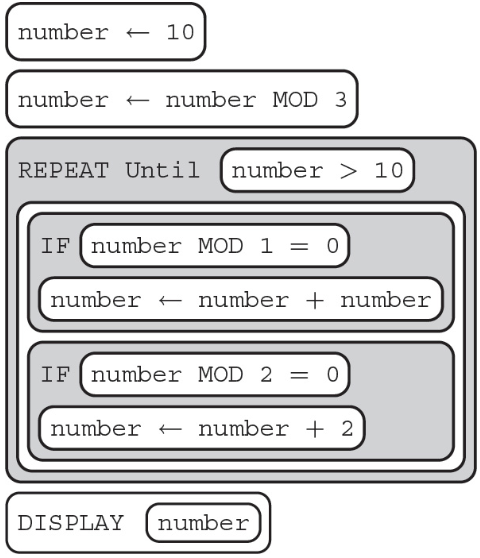
(A) 1
(B) 10
(C) 22
(D) 30
63. Why is it important to find an efficient solution to a problem?
(A) An efficient solution makes it harder to copy an algorithm.
(B) An efficient solution can make it easier to analyze large data sets in a reasonable amount of time.
(C) An efficient solution uses more computer resources, which ensures that the results are correct.
(D) An efficient solution of an algorithm with factorial efficiencies can run in a reasonable amount of time.
64. What binary number is equal to 10001BIN + 3DEC?
(A) 10011 BIN
(B) 10100 BIN
(C) 11100 BIN
(D) 11110 BIN
65. Which of the following can be represented by a single binary number? Select two answers.
(A) What is the position of an object in a grid of squares representing the position of a two-dimensional array?
(B) Do you have a puppy?
(C) Is your puppy named “Waffles”?
(D) What is the speed of a puppy chasing a squirrel?
66. Most products you can buy have a barcode on them with 13 digits.
The first 12 digits are the actual identification number for the product, the 13th is the check digit calculated from the other 12.

The check digit is calculated using the following algorithm.
Step 1: Multiply every second digit (starting with the second digit) by 3, and every other digit by 1 (so they stay the same).
Step 2: Add up all the multiplied numbers to obtain the sum.
Step 3: The check digit is whatever number would have to be added to the sum in order to bring it up to a multiple of 10 (i.e., the last digit of the sum should be 0).
Using the above algorithm calculate the check digit on the bar code below.

(A) 4
(B) 5
(C) 6
(D) 7
67. Why are internet protocols used? Select two answers.
(A) Internet protocols make the internet scalable and encourage growth.
(B) Internet protocols are needed to slow the growth of the internet.
(C) Internet protocols are a set of rules to ensure the internet can work and transmit information across different equipment used within the internet.
(D) Internet protocols are specific to the hardware attached to the internet.
68. Which of the following algorithms will display “3” if the number entered by the user contains a “3” in the ones place? (Both 3 and 503 contain a 3 as the first digit; 734 and 4 do not contain a 3 as the first digit.) novack <-- input( )Select two answers.
(A) IF (novack = 3)
DISPLAY(3)
(B) IF (novack / 3 = 0)
DISPLAY(3)
(C) IF (novack / 10 = 3)
DISPLAY(3)
(D) IF (novack MOD 10 = 3)
DISPLAY(3)
69. When should a heuristic algorithm be used?
(A) When determining which files could have been exposed to a virus before actually checking all files contained on the computer
(B) When calculating the average score for the national SAT test
(C) When finding the quickest way to drive from Orlando, Florida, to Cold Foot, Alaska
(D) When finding the lifetime batting average of Mookie Wilson
70. A simulation for a color chooser should result in 25% BLUE. Which of the following could replace to most likely result in BLUE being selected 25% of the time? Select two answers.
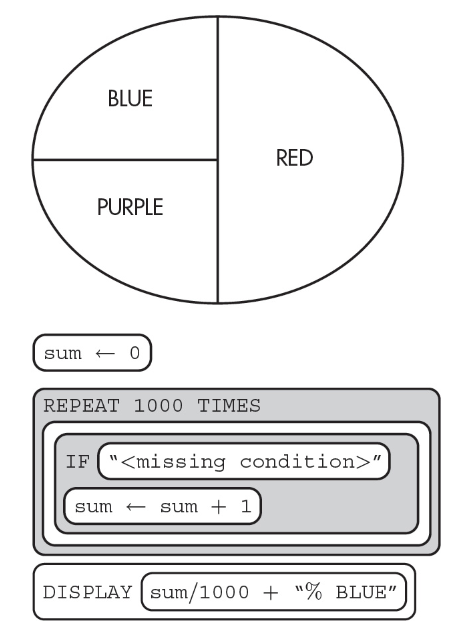
(A) RANDOM(1, 4) < 2
(B) RANDOM(250, 1000) < 251
(C) RANDOM(1, 2) > 1
(D) RANDOM(5, 8) > 7





