Practice Test 1 - AP Computer Science Principles Premium 2024
Practice Test 1
TIME: 120 MINUTES
70 QUESTIONS
1. Consider the following code.
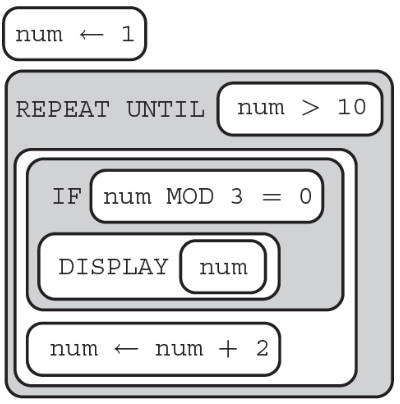
What is displayed because of executing the code segment?
(A) 1 3 5 7 9
(B) 1 5 7
(C) 3 9
(D) 9
2. Consider the following code segment.
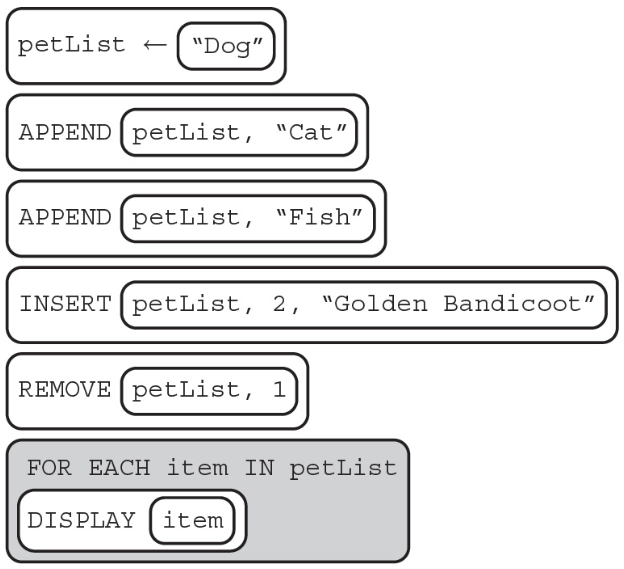
What is displayed as a result of executing the code segment?
(A) Dog Cat Fish Golden Bandicoot
(B) Dog Cat Fish
(C) Dog Golden Bandicoot Cat Fish
(D) Golden Bandicoot Cat Fish
3. Students at a high school receive letter grades based on the following scale:

Which of the following code segments will display the correct letter grade for a given score?
I.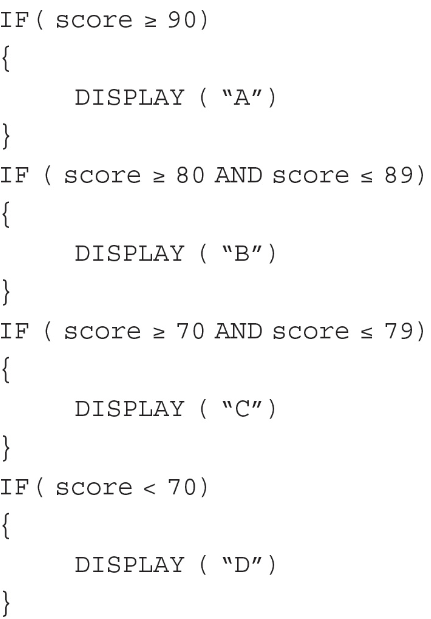
II.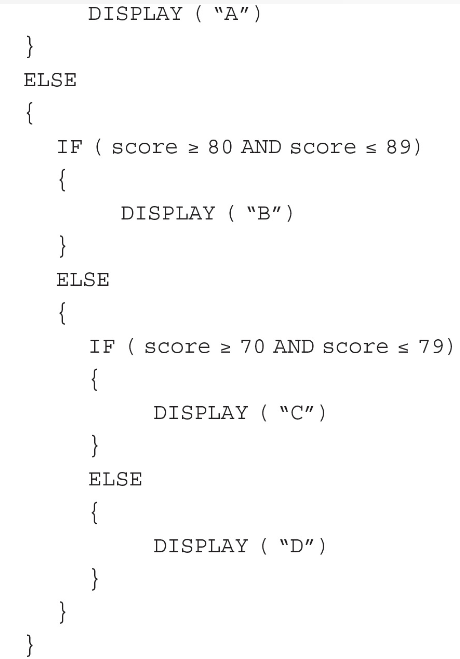
III.
(A) I only
(B) III only
(C) I and II only
(D) I, II, and III
4. Colors can be represented by decimal values from 0 to 255. If each pixel in a photo is a combination of three color values, what is the minimum number of bits needed to store a single pixel?
(A) 512
(B) 256
(C) 24
(D) 8
5. Which of the following is a true statement about data transmitted over the internet?
(A) All data traveling over the internet is binary.
(B) Packets are received in the same order that they are sent.
(C) Redundancy in the design of the internet is overseen by large companies that set the standards used.
(D) The domain name system (DNS) has been challenged by the Digital Millennium Copyright Act (DMCA).
6. What will the following code segment display?
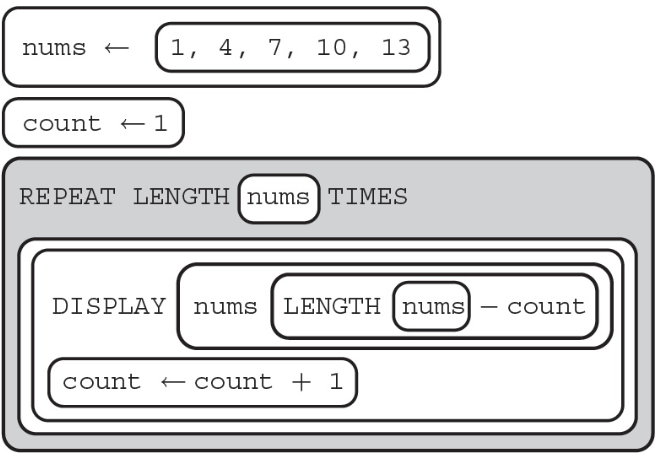
(A) 1 4 7 10 9
(B) 10 7 4 1
(C) 9 10 7 4 1
(D) Nothing will be displayed due to the error index out of bounds.
7. What should replace so that the program below displays TRUE 60% of the time?
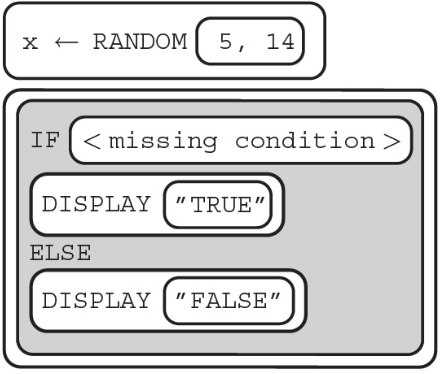
(A) x < 6
(B) x ≥ 6
(C) x > 10
(D) x ≤ 10
8. What percentage of the time will the program display an even number?

(A) 10%
(B) 20%
(C) 40%
(D) 50%
9. What will the following code segment display?
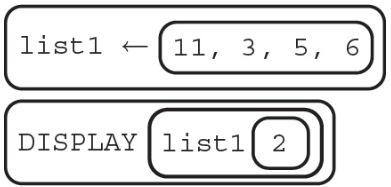
(A) 11
(B) 6
(C) 3
(D) Nothing will be displayed due to an error.
10. A flowchart is a way to represent an algorithm visually. The flowchart below uses the following building blocks.
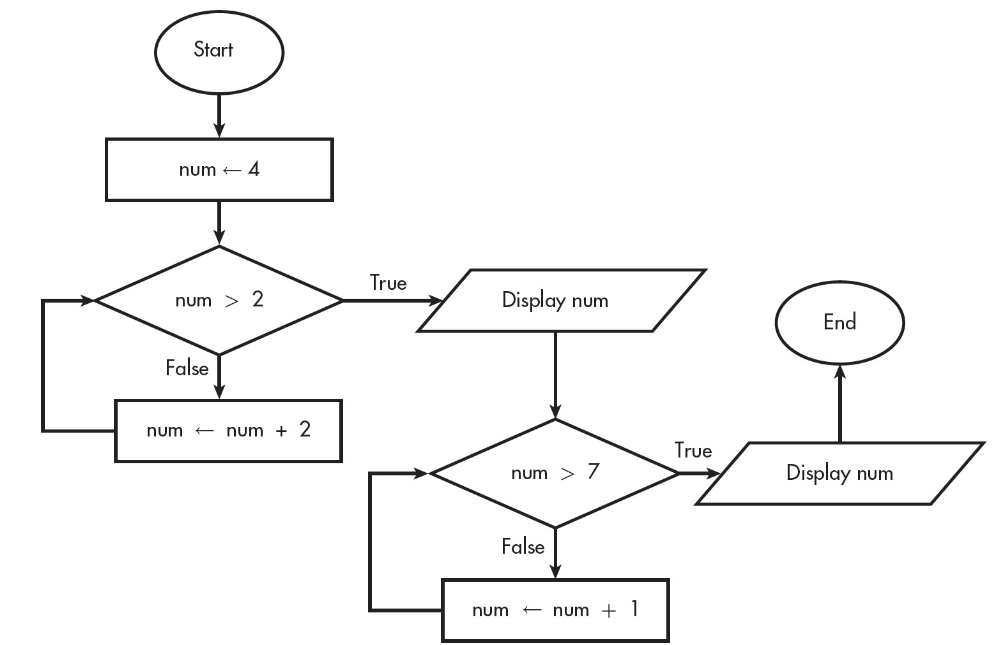
What will the program above display?
(A) 2 8
(B) 4 8
(C) 2 7
(D) 3 7
11. When run in series, a program that checks pictures for puppies takes 4,000 seconds to check 100 pictures for puppies. When running the same program in parallel, it takes 400 seconds to run. What is the speedup for the parallel solution?
(A) 1
(B) 10
(C) 100
(D) 1,000
12. Which of the following does NOT need to be considered when determining the credibility of a source?
(A) Author’s reputation and credentials
(B) Use of persuasive techniques within the source
(C) Publisher’s reputation and credentials
(D) Sponsorship of the article or publisher
13. The code segment below is intended to swap the variables a and b using a temporary variable, temp. What can replace so the algorithm works as intended?
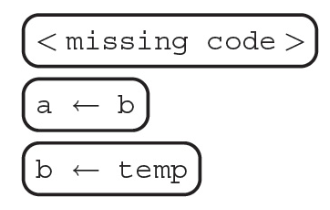
14. In 2018, the company Cambridge Analytica was found to have collected data regarding millions of Facebook users. This was done by utilizing a loophole in Facebook’s data collection policy, where apps connected to Facebook could collect information on a person’s friends without the friends’ permission. Which of the following concepts does this demonstrate?
(A) If security-related protections are ignored, the curation of data by commercial groups can be exploited.
(B) If privacy-related protections are ignored, the curation of data by commercial groups can be exploited.
(C) If security-related protections are ignored, the curation of data by governmental programs can be exploited.
(D) If privacy-related protections are ignored, the curation of data by governmental programs can be exploited.
15. Consider the following code segment, which uses the variables a, b, and c.
a ← 2
b ← a + a
c ← b + a
a ← c + a
DISPLAY(a)
DISPLAY(b)
DISPLAY(c)
What is displayed by running the code segment?
(A) 3 3 6
(B) 8 4 6
(C) 11 3 8
(D) 3 11 3
16. Which best describes the role of TCP?
(A) Protocols for how files are broken into packets, addressed, and transmitted on the internet.
(B) The set of rules for the path packets taken on the fault-tolerant internet
(C) Setting the rules for a numerical label assigned to each device connected to the internet
(D) A common protocol for encrypting and decrypting data transferring on the internet
17. What is the minimum number of lines that must be cut to isolate F completely?
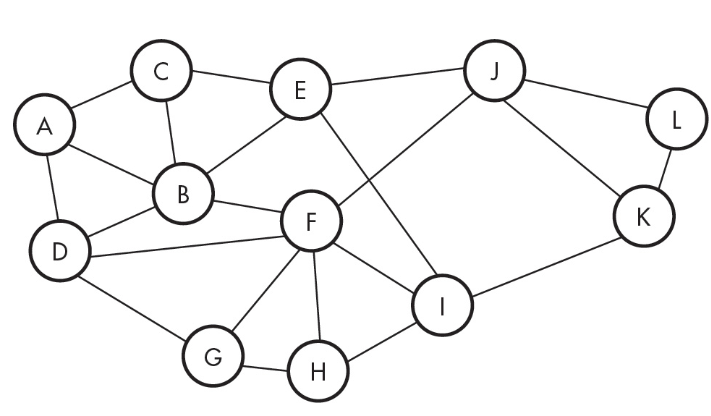
(A) 0
(B) 4
(C) 6
(D) 8
18. By switching from IPv4, which can store 232 IP addresses, to IPv6, which can store 2128 IP addresses, how many more IP addresses will become available?
(A) Twice as many IP addresses
(B) 22 as many IP addresses
(C) 96 as many IP addresses
(D) 296 as many addresses
19. The program below is intended to display the average of the numbers in aList.
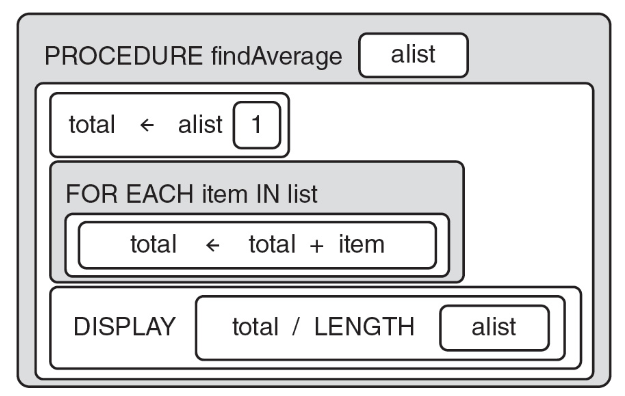
In order to test the program, the programmer initializes aList to [0,1, 7, 8, 2, 6]. The program displays 4, so the programmer concludes the program works as intended. Which of the following is true?
(A) Using the test case [0,1,7,8,2,6] is not sufficient to conclude that the program works as intended.
(B) The program works as intended.
(C) The conclusion is not correct as the test case gave an incorrect answer.
(D) The conclusion is only correct for test cases with 6 numbers.
20. Which of the following is NOT metadata for the picture?

(A) The picture of the dog
(B) The location where the picture was taken
(C) The time the picture was taken
(D) The memory space taken up by the picture
21. What are the possible landing spaces for the robot after running the program segment shown below?


(A)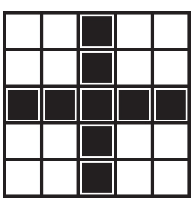
(B)
(C)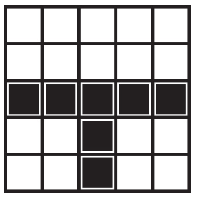
(D)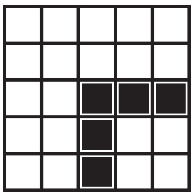
22. The two algorithms shown below, Algorithm A and Algorithm B, are intended to calculate average.
Algorithm A
Step 1: Set sum equal to 0.
sum ← 0
Step 2: Set count = 1.
count ← 1
Step 3: Add list[count] to sum.
sum ← sum + list[count]
Step 4: Add 1 to count.
Step 5: Repeat steps 3 and 4 until count is equal to LENGTH(list).
Step 6: Set ave to sum divided by count.
ave ← sum / count
Step 7: Return step 6.
Algorithm B
Step 1: Set sum equal to 0.
sum ← 0
Step 2: Set count = 1.
count ← 1
Step 3: Add list[count] to sum.
sum ← sum + list[count]
Step 4: Add 1 to count.
Step 5: Set ave to sum divided by count.
ave ← sum / count
Step 6: Repeat steps 3, 4, and 5 until count is equal to LENGTH(list).
Step 7: Return the last value calculated in step 5.
Which algorithm calculates average correctly?
(A) Algorithm A calculates average in all cases, while Algorithm B does not.
(B) Algorithm B calculates average in all cases, while Algorithm A does not.
(C) Neither Algorithm A nor Algorithm B calculates average correctly.
(D) Both Algorithm A and Algorithm B calculate average correctly, but Algorithm A is more efficient.
23. Why does program code have to be run through a compiler?
(A) Program code is write-only until it is run through a compiler.
(B) Program code must be translated into a language the computer understands.
(C) Program code must be debugged by the compiler before it can ever run.
(D) It doesn’t, as the new program could be run directly from the code.
24. The procedure findAverage is intended to return the average number in the list numbers. The procedure does not work as intended for all test cases.
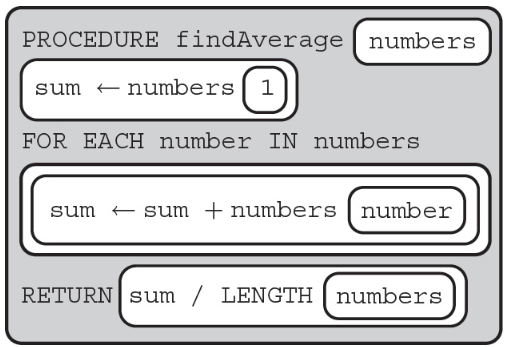
Which of the following test cases will return the correct average using the above procedure?
(A) numbers[1, 1, 35, 6]
(B) numbers[0, 1, 35, 6]
(C) numbers[11, 35, 6]
(D) numbers[3, 5, 11, 6]
25. Which of the following is NOT an example of using citizen science as a possible solution?
(A) Documenting the behavior of fireflies during the summer months.
(B) Documenting the number and type of jellyfish washing up on the shores of the Atlantic Ocean.
(C) Documenting sounds of bat pups during feeding using expensive ultrasonic microphones and sonograms.
(D) Comparing average PSAT scores for students in different counties.
Questions 26–28 refer to the information below.
A web browser is selling its information cookies to third-party marketing companies. These companies are profiling users and selling the sorted data to targeted advertisers.
The web browser is debating adding a setting called Do Not Track. Once enabled, this setting would send a Do Not Track signal to the websites you visit, informing them that you do not give them permission to collect or share your personal information for behavioral advertising, price discrimination, or for any other purpose.
This setting would stop data brokers from legally selling your personal information from the sites you visit.
26. Which of the following is the most likely data privacy concern for the original browser?
(A) Information collected about your personal preferences and private activities might be used to brand you as members of a particular group.
(B) Cookies are used to acquire users’ private encryption keys.
(C) Cookies are text files that keep track of such things as website visits and activity on that website.
(D) Cookies are responsible for spam and create pop-up advertisements.
27. Which of the following is least likely to receive targeted advertisements?
(A) Individuals using the web browser without the Do Not Track option
(B) Users who visit only websites with a digital certificate that block targeted advertisements
(C) Users with strong passwords and multifactor authentication
(D) Individuals using the web browser with the Do Not Track setting engaged
28. Which of the following potential benefits is MOST likely to be provided by the upgraded system?
(A) Weather websites customizing site information based on the user’s location without having the user enter the city every visit
(B) Increasing the speed in ordering pizza online because the pizza webpage remembers the user’s address and credit card information
(C) Limiting the information about the sites and stores that the user visits
(D) Offering products and services that are more relevant to the user
_________________________________________________________________________
29. What does the following code segment display?
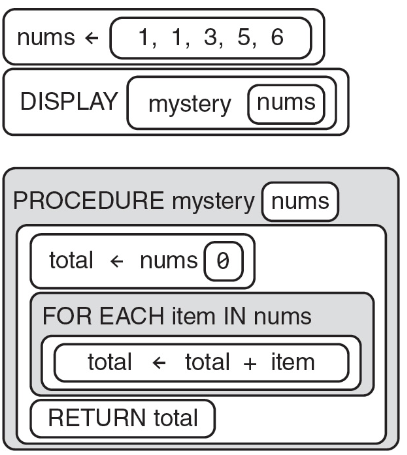
(A) 0
(B) 16
(C) 11356
(D) Nothing is displayed due to an error in the code.
30. Convert 88DEC to a binary number.
(A) 1111000BIN
(B) 1011000BIN
(C) 1010101BIN
(D) 1000001BIN
31. Assume a particular system stores text by connecting 8-bit sequences. Each character in a string is one sequence, with the number used corresponding to its place in the alphabet (thus, a would be 00000001, b would be 000000010, c would be 000000011, and so on). In this system, what would be the binary representation of the word dog?
(A) 00000111 00001111 00000100
(B) 00000100 00001111 00000111
(C) 00000100 00001001 00000111
(D) 00000010 00001111 00000111
32. The abstraction Draw(magnitude, direction) is used to draw line segments at a given magnitude and direction (north, south, east, or west) starting at the tip of the first vector to the tail of the second vector. Consider the following program, where the vector starts in the upper-left corner of a grid of dots.
Draw(2, east)
Draw(2, east)
Draw(3, south)
Draw(1, west)
Which of the following represents the figure that is drawn by the program?
(A)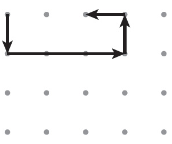
(B)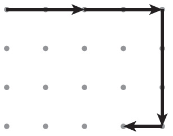
(C)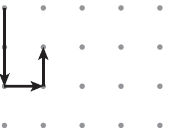
(D)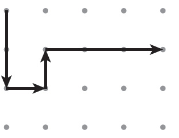
33. In the following flowchart, what is the value of RESULT?
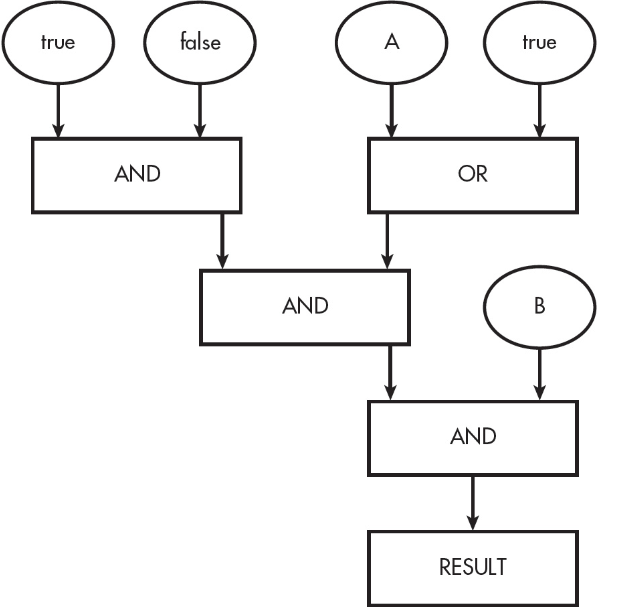
(A) True when both A and B are true
(B) True when either A or B are true
(C) Always true
(D) Always false
34. An economist wants to understand how changes in supply and demand affect the inflation rate of a country. What is a benefit of using a simulation?
(A) A simulation would be more cost-effective and easier to create than an experiment done to an entire country.
(B) A simulation would be able to account for every variable that would affect supply and demand.
(C) Simulations can be run only once, so they are guaranteed to be close to real life because an experiment like this could happen only once.
(D) Simulations have as much of an effect on the real world as an actual experiment of this scale would.
35. Which of the following is true about data compression?
(A) Data compression can be used for pictures and video only.
(B) Lossless data compression is the best compression under all conditions.
(C) Data compression can be used to reduce the size of a file for storage or transmission.
(D) Lossy compression cannot be used when sending pictures.
36. A programmer is writing a program that is intended to be able to process large amounts of data in a reasonable amount of time. Which of the following considerations is likely to affect the ability of the program to process large data sets?
(A) The amount of program documentation that should be minimized
(B) The order of the data put into the data set
(C) How much memory the program requires to run
(D) How many program statements the program contains
37. A certain company collaborates with scientists by creating and testing simulations for scientific research. Which of the following is a potential outcome of this?
(A) If a simulation continuously provides a result that is considered abnormal, this could be used as a basis for further research by scientists.
(B) If a concept would be too expensive to perform in real life, the company could create a simulation with the help of the scientists.
(C) If scientists need information to create a hypothesis, a simulation can be used to provide the information necessary.
(D) All of the above are potential outcomes.
38. Charlie Chaplin’s first movie, Making a Living, was released in 1915 and sampled real-world movements onto film at a rate of 16 frames per second. However, the actors’ movements did not accurately reflect motion observed in real life and had a jumpy effect.
What could be done to represent the natural movement more accurately?
(A) The film should have remained in an analog form.
(B) Increase the amplitude of the analog signal.
(C) Increase the frames per second sample rate.
(D) Decrease the frames per second sample rate.
39. Why does updating a file require more memory than reading a file?
(A) A read file needs only certain parts loaded to memory, but an updating file requires the entire file to be in memory.
(B) A read file requires no memory, so the updating file would always require more memory.
(C) A read file requires the entire file be loaded to memory, but an updating file requires both the original version and the updated version be in memory.
(D) A read file uses only the hard disk, while an updating file requires both the hard disk and the RAM.
40. Why do computing innovations tend to lead to legal concerns?
(A) Lawyers are unfamiliar with the laws governing computing innovations because these laws involve multiple states.
(B) Laws about the internet concerning copyrights have been passed, but the speed of innovations has made these laws harder to enforce.
(C) Laws involved in these concerns were often created before the advent of computers, meaning that these laws may not cover certain aspects of new technology.
(D) There is no way to hide your IP address on the internet, so laws are easily enforced.
41. To stop the spread of a contagious disease, social distancing of 6 feet is recommended. To test a person for the disease and comply with the 6-foot distancing recommendation, pharmacies are requiring customers to schedule an appointment online for the test. These appointments will reduce the in-pharmacy wait time during which people are at risk of catching the disease.
Which of the following is considered a potential effect of the digital appointments rather than the purpose of the digital appointments?
(A) People without internet access will not be able to make an appointment and thus are more likely to get and spread the disease.
(B) The digital appointments will allow for more testing.
(C) Digital appointments will ensure an even distribution of tests on both sides of the digital divide.
(D) Digital appointments will make people who live in cities less likely to get tested.
42. What is a major disadvantage of the internet’s model of trust?
(A) A trusted website can have a large amount of power over a computer, so improper trusts can be very damaging if the website is malicious.
(B) A trusted website has power over the computer’s ROM, which could be very damaging if the website is malicious.
(C) A trusted website cannot have encrypted communications, which means any data sent can be read by an interceptor.
(D) A trusted website can still download malicious code even if it is blocked by a firewall.
43.The design of a program incorporates investigations to determine its requirements. Most programs are designed to be used by people other than the programmers. To meet the needs of the users, the investigation must identify the program constraints as well as the concerns and interests of the people who will use the program.
Which of the following is NOT an investigation tool for designing programs?
(A) Programming the most elegant code
(B) Collecting data through surveys
(C) User testing
(D) Direct observations.
44. The Caesar cipher is an encryption technique. It is a substitution cipher that replaces a letter with a different letter a fixed number of positions down the alphabet. For example, a shift of 3 would cause the word “cat” to be translated to “fdw.” The Caesar cipher is an example of what type of encryption?
(A) Home key encryption
(B) Public key encryption
(C) Symmetric encryption
(D) No key encryption
45. What is the purpose of a digital certificate in secured communications?
(A) A digital certificate ensures that the communication system has been examined by a third party.
(B) A digital certificate ensures that the server’s own security features have been examined by a third party, are using public key encryption, and are ensuring that the transactions are being kept confidential.
(C) A digital certificate ensures that the server contacted in the secure connection is the actual server and not a copycat.
(D) A digital certificate ensures that the website’s code has been created by a professional programmer.
46. Which of the following illustrate ways that the internet facilitates collaboration?
I. People can communicate more quickly, enabling teams to work together regardless of distance.
II. Online technologies, such as messaging and file transfers, make it easier to send visuals that can be pertinent for projects.
III. File-sharing protocols enable documents to be saved in the cloud and edited by all team members.
(A) I only
(B) I and III only
(C) II and III only
(D) I, II, and III
47. A web browser contacts a server using IPv4 and pages a request for a website’s address. Which of the following could NOT be a potential response?
(A) 92.11.198.113
(B) 174.260.45.144
(C) 128.198.232.65
(D) 54.116.188.246
48. Which of the following types of components is necessary for cybersecurity?
I. Software
II. Hardware
III. Human
(A) I only
(B) III only
(C) I and II only
(D) I, II, and III
49. What is the maximum number of searches required if using a linear search on a list containing 2,000 numbers?
(A) 2,000
(B) 1,000
(C) 11
(D) 1
50. The procedure isFound(list, item) will return TRUE if an item is found in a list. What will the following procedure display?
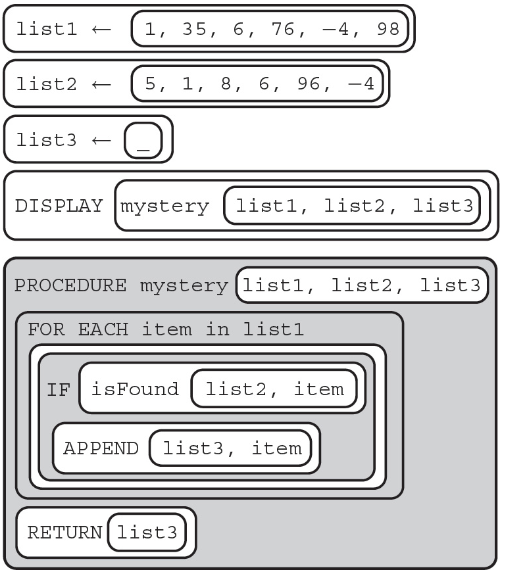
(A) [ ]
(B) [1, 6, −4]
(C) [4, 6, −4]
(D) [1, 35, 6, 76, 4, 98, 5, 1, 8, 96, −4]
51. What is the value of sum displayed after this algorithm is run?
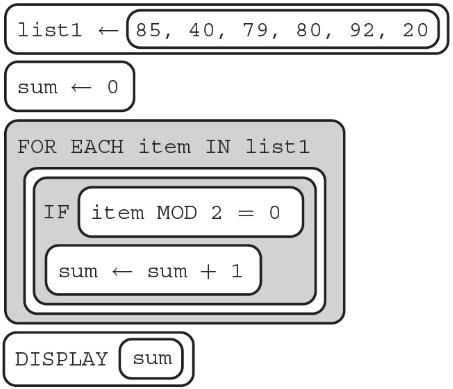
(A) 0
(B) 4
(C) 6
(D) Error
52. What will the following program display?
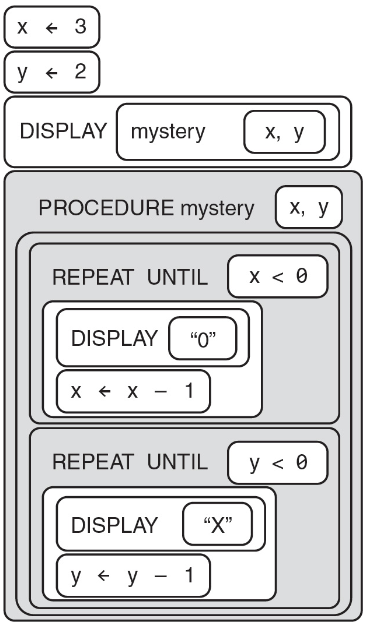
(A) OXXOXXOXX
(B) OXXOO
(C) OOOOXXX
(D) The program is an infinite loop.
53. What will be the result of the displayed program?
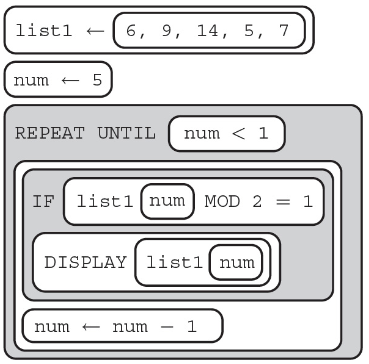
(A) 9 5 7
(B) 6 14
(C) 14 6
(D) 7 5 9
54. What will be the output of the following program?
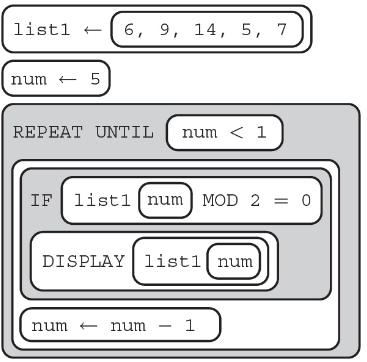
(A) 9 5 7
(B) 14 6
(C) 14
(D) 7 5 9
55. Consider the following code segment.
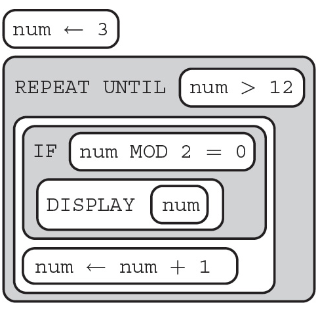
What will the executed code display?
(A) All odd numbers between 3 and 12
(B) All even numbers between 1 and 12
(C) All even numbers between 3 and 12
(D) All odd numbers between 1 and 12
56. What should replace so the program below displays TRUE 60% of the time?
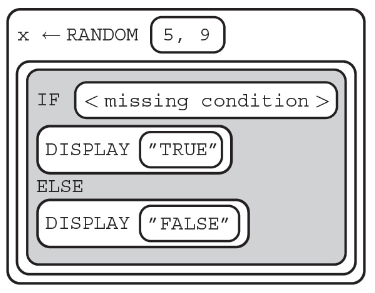
(A) x MOD 2 = 0
(B) x MOD 5 = 0
(C) x MOD 2 = 1
(D) x MOD 5 = 5
57. What percentage of the time will the following program display a number?

(A) 10%
(B) 20%
(C) 25%
(D) 75%
58. What is the following program displaying?
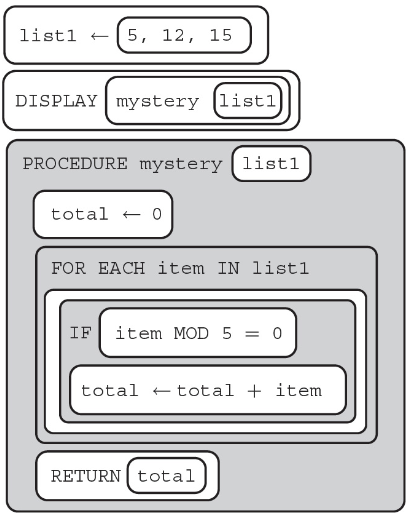
(A) 37
(B) 27
(C) 25
(D) 20
59. What is the code below displaying?

(A) 0
(B) 2, 4, 6, 8, 10, 12, 14
(C) 3, 6, 9, 12
(D) 3, 6, 9, 12, 15
60. What is the code segment displaying?
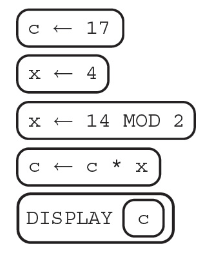
(A) 68
(B) 34
(C) 17
(D) 0
61. What does the algorithm display?
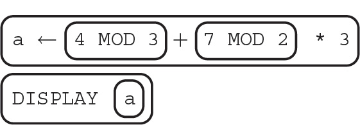
(A) 3
(B) 4
(C) 5
(D) 7
62. A certain computer has three identical processors that can run in parallel. Each processor can run only one process at a time, and each process must be executed on a single processor. The following table indicates the amount of time it takes to execute a particular process on a single processor. Assume none of the processes are dependent on any other process. Process Execution time (seconds)
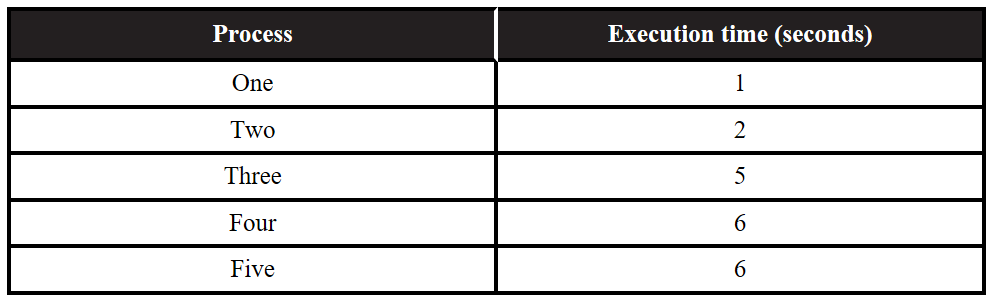
Which of the following best approximates the minimum possible time to run all five processes?
(A) 5 seconds
(B) 6 seconds
(C) 7 seconds
(D) 8 seconds
63. What will y display?
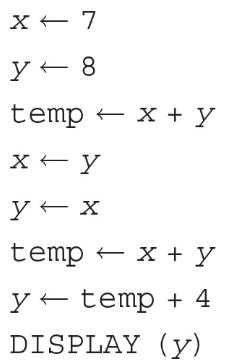
(A) 0
(B) 15
(C) 16
(D) 20
64. A certain computer has a single central processing unit. The following table indicates the amount of time it takes to execute a single process. Assume none of the processes are dependent on any other process.
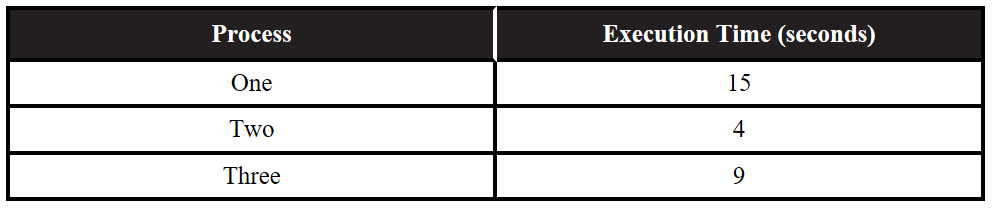
Which of the following best approximates the minimum possible time to run all three processes in series?
(A) 28 seconds
(B) 15 seconds
(C) 9 seconds
(D) 4 seconds
65. Why is it more effective to put procedures in a program than to repeat code? Select two answers.
(A) Procedures make a program harder to edit because every extraction is saved on a distinct file.
(B) Procedures simplify editing by requiring only one edit to the abstraction rather than to every instance of the code.
(C) Using procedures takes up less space than repeating code, which makes the program easier to read.
(D) Procedures are guaranteed to work in every instance they are used if they work once.
66. The following question uses a robot in a grid of squares. The robot is represented by a triangle, which is initially facing right. Which code can replace to have the robot end up in the gray square? Select two answers.
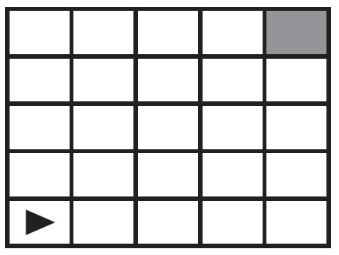
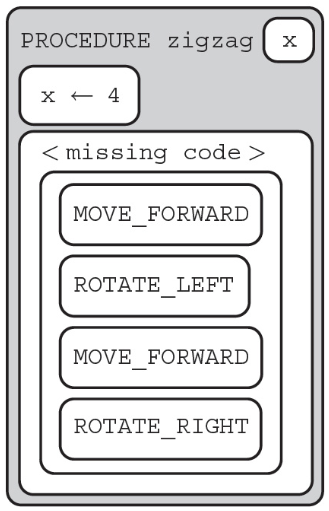
(A) REPEAT UNTIL x = 4
(B) REPEAT 4 TIMES
(C) FOR EACH item IN list
(D) REPEAT UNTIL (Goal_Reached)
67. The findings from a project are typically presented using a graph as opposed to a table or raw data. Why might this be? Select two answers.
(A) Graphs can be easily placed into a slideshow or document, while tables cannot.
(B) Graphs can show trends that might not be easily seen with raw data.
(C) Graphs are able to show all of the detail necessary to understand data.
(D) Graphs are easier to read and interpret at a glance.
68. The question below uses a robot in a grid of squares. The robot is represented by the triangle, which is initially in the top-left square of the grid and facing toward the top of the grid.
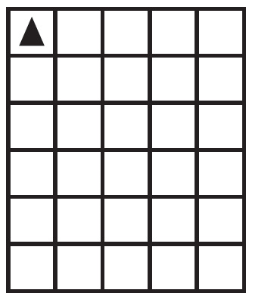
Code for the procedure Mystery is shown below. Assume that the parameter p has been assigned a positive integer value (e.g., 1, 2, 3, . . .).
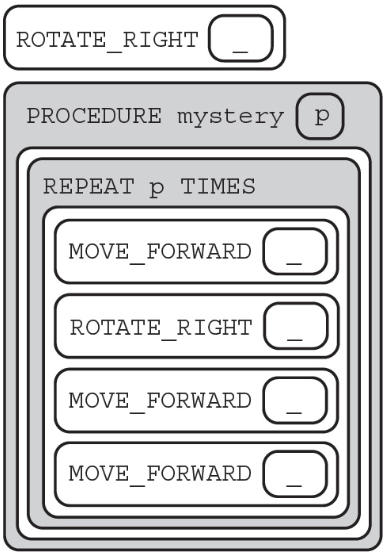
Which of the following shows possible results of running the code segment with any value of p ≥ 0 AND p < 2? Select two answers.
(A)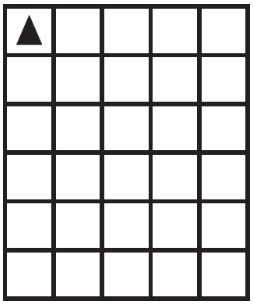
(B)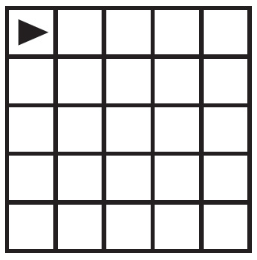
(C)
(D) Error. The robot leaves the grid.
69. A theme park wants to create a simulation to determine how long it should expect the wait time to be at its most popular ride. Which of the following characteristics for the virtual patrons would be most useful? Select two answers.
(A) Ride preference—denotes whether a patron prefers roller coasters, other thrill rides, gentle rides, or no rides
(B) Walking preference—denotes how far a patron is willing to walk in between rides
(C) Food preference—denotes the type of food that a patron prefers to eat (e.g., chicken, burgers, salads)
(D) Ticket type—denotes whether the patron has a single-day pass, a multiday pass, or an annual pass
70. A robot is shown in the lower-left corner of a grid and is pointing up.
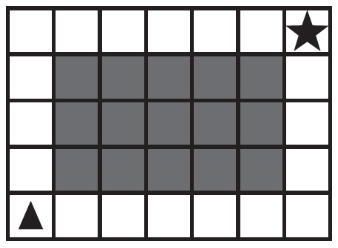

What procedure will result in the robot landing on the star? Select two answers.
(A) moveAndSpin(4, 1)
moveAndSpin(6, 0)
(B) moveAndSpin(0, 1)
moveAndSpin(6, 3)
moveAndSpin(4, 0)
(C) moveAndSpin(7, 3)
(D) moveAndSpin(0, 7)





