Practice Exercises - COMPUTER SYSTEMS AND NETWORKS - AP Computer Science Principles Premium 2024
COMPUTER SYSTEMS AND NETWORKS QUESTIONS
1. Which of the following is true about packets?
(A) Packets will travel along the fastest path from the sending to receiving computer.
(B) Packets can arrive at the receiving computer in a different order than sent by the sending computer.
(C) When sent by a sending computer packets are guaranteed to arrive at the receiving computer.
(D) One sending file will contain one packet.
2. Which characteristics of internet protocols have helped fuel the rapid growth of the internet? Select two answers.
(A) Internet standards cannot be altered, so different companies can focus on development.
(B) Internet protocols are open (nonproprietary).
(C) Internet protocols are designed to be useful for a growing population of users.
(D) The design of internet protocols involves large profits that motivate companies to innovate internally with no outside feedback.
3. Which of the following internet protocols defines how computers send packets of data to each other? Select two answers.
(A) HTTP
(B) TCP
(C) IP
(D) UDP
4. Which of the following protocols is responsible for addressing and routing your online requests?
(A) HTTP
(B) TCP
(C) IP
(D) UDP
5. When is it advantageous to use UDP instead of TCP?
(A) UDP should be used when the IP address of the receiving computer is not known.
(B) UDP should always be used when available since UDP is faster and more reliable than TCP.
(C) UDP should be used when a guarantee is required that the order of data at the sending computer matches the order of data arriving at the receiving computer.
(D) UDP should be used when the speed of data transfer is more important than error correction.
6. Many types of computing devices made by many types of companies can all access the internet. Which of the following makes this access possible?
(A) Redundancy
(B) Open standards and protocols
(C) Fault tolerance
(D) Large bandwidth
7. Why are most websites designed to work within the boundaries of current web protocols, even when that limits the website’s capabilities?
(A) Since the protocols are supported by all current web browsers, potential incompatibilities are minimized.
(B) It is illegal to go beyond the boundaries of current protocols.
(C) Current protocols are the limit of web technology, so going further is impossible.
(D) If a protocol is exceeded, an ISP will assume the website to be broken or malicious and block it.
8. What is the purpose of transitioning from IPv4 to IPv6?
(A) IPv4 has been found to be too insecure for modern communication.
(B) The rise of internet-connected devices means that the number of available unique IPv4 addresses is sharply decreasing, and IPv6 will allow for more addresses.
(C) IPv4 is too slow to be useful in modern communications.
(D) It is easier to spoof an IPv4 address, as compared to an IPv6 address.
9. How does redundancy improve the scaling of the internet?
(A) Redundancy leads to every communication being repeated, which keeps the data from being lost.
(B) Redundancy leads to every communication being repeated, which ensures that the connected devices do not disconnect from each other.
(C) Redundancy makes connections more reliable, which means that more devices are able to communicate without interruption.
(D) Redundancy makes connections more reliable, which ensures that computers are always on the internet.
10. How many lines need to be cut to isolate A completely?
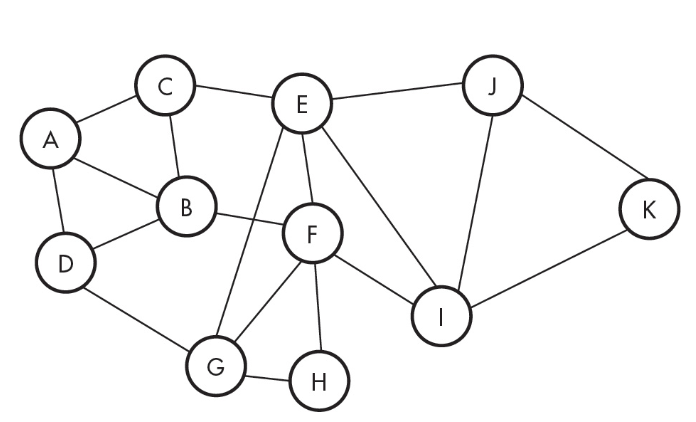
(A) 1 line
(B) 3 lines
(C) 4 lines
(D) 5 lines
11. How many lines need to be cut to isolate F completely?
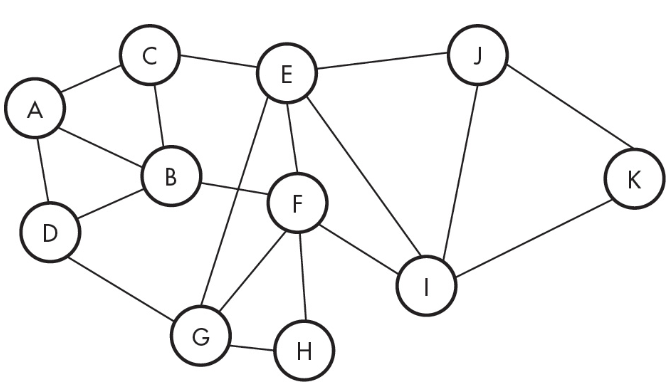
(A) 1 line
(B) 3 lines
(C) 4 lines
(D) 5 lines
12. How many lines need to be cut to isolate A completely?
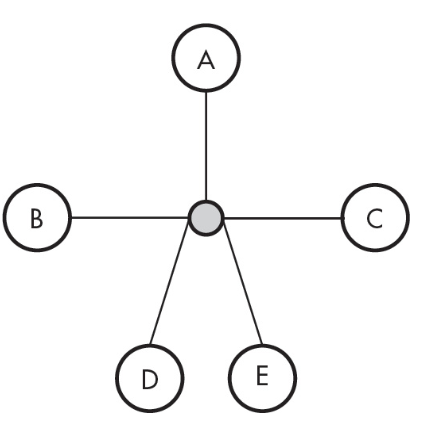
(A) 1 line
(B) 3 lines
(C) 4 lines
(D) 5 lines
13. What is the minimum number of computers a packet must go through when traveling from computer B to computer D?
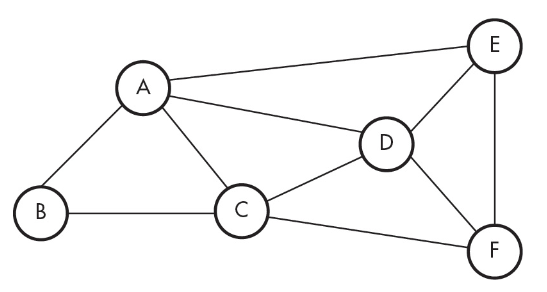
(A) 0
(B) 1
(C) 2
(D) 3
14. If the line between computers B and C has failed, which computer must a message go through if a message is sent between computers B and C?
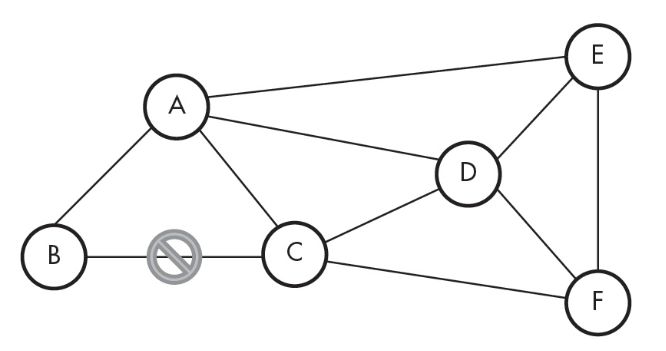
(A) A
(B) D
(C) E
(D) F
15. The internet is built on open standards. In this context, what does “open” mean?
(A) The standards are made freely available and can be used by anyone.
(B) The standards cannot be used in proprietary software of any form.
(C) The standards can be used in any program that is used exclusively to access the web.
(D) The official standards can be made, updated, and edited by anyone.
16. Which of the following best describes the fault-tolerant nature of the internet?
(A) The internet always picks the fastest routes for packets traveling between a sending and receiving computer.
(B) If a node on the internet fails, the packets choose a different path to the receiving computer.
(C) This fault-tolerant nature adds an additional layer of privacy for data traveling across the internet
(D) All of the above.
17. Which of the following statements about packets are true? Select two answers.
(A) Packets must be received in the order they are sent to be reassembled.
(B) Packets do not have to be received in the order they are sent to be reassembled.
(C) Packets can travel different paths from the sending computer to the receiving computer.
(D) Packets always choose the fastest path available from sending computer to receiving computer.
18. Which of the following is true about redundancy on the internet?
I. Redundancy slows down packets traveling from a sending computer to a receiving computer.
II. Redundancy allows for adding new devices to the network without disrupting traffic.
III. Redundancy makes the internet fault tolerant.
(A) I only
(B) I and II only
(C) II and III only
(D) I, II, and III
19. Which of the following describes a benefit of internet standards?
I. Internet standards are procedures to ensure that software and hardware created by different companies can communicate with each other online.
II. Internet standards are written to ensure that internet protocols are open and free to use.
III. Internet standards reduce the risk of malicious software affecting users of the internet.
(A) I only
(B) I and II only
(C) II and III only
(D) I, II, and III
20. Which of the following is contained in a packet?
(A) The sender’s IP address
(B) The receiver’s IP address
(C) Data
(D) All of the above
21. A certain computer has a single central processing unit. The following table indicates the amount of time three processes each take to execute on a single processor. Assume none of the processes are dependent on any other process.
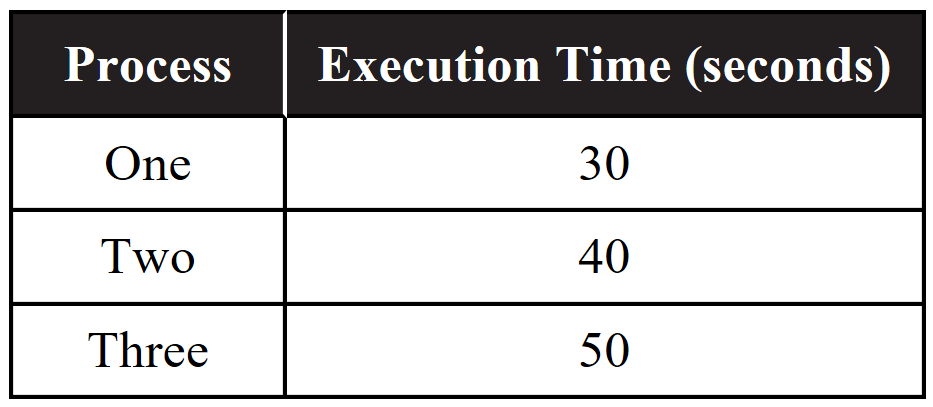
Which of the following best approximates the minimum possible time to run all three processes in series?
(A) 30 seconds
(B) 70 seconds
(C) 80 seconds
(D) 120 seconds
22. A certain computer has two identical processors that can run in parallel. Each processor can run only one process at a time, and each process must be executed on a single processor. The following table indicates the amount of time three processes each take to execute on a single processor. Assume none of the processes are dependent on any other process.
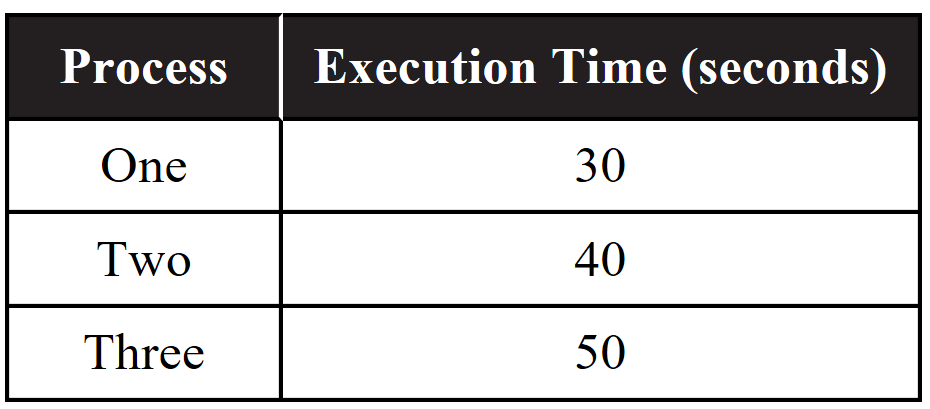
Which of the following best approximates the minimum possible time to run all three processes in parallel?
(A) 30 seconds
(B) 70 seconds
(C) 80 seconds
(D) 120 seconds
23. A certain computer has two identical processors that can run in parallel. Each processor can run only one process at a time, and each process must be executed on a single processor. Processes one and two must be run in series, while process three, four and five can all run in parallel. The following table indicates the amount of time needed to execute all five processes on a single processor.
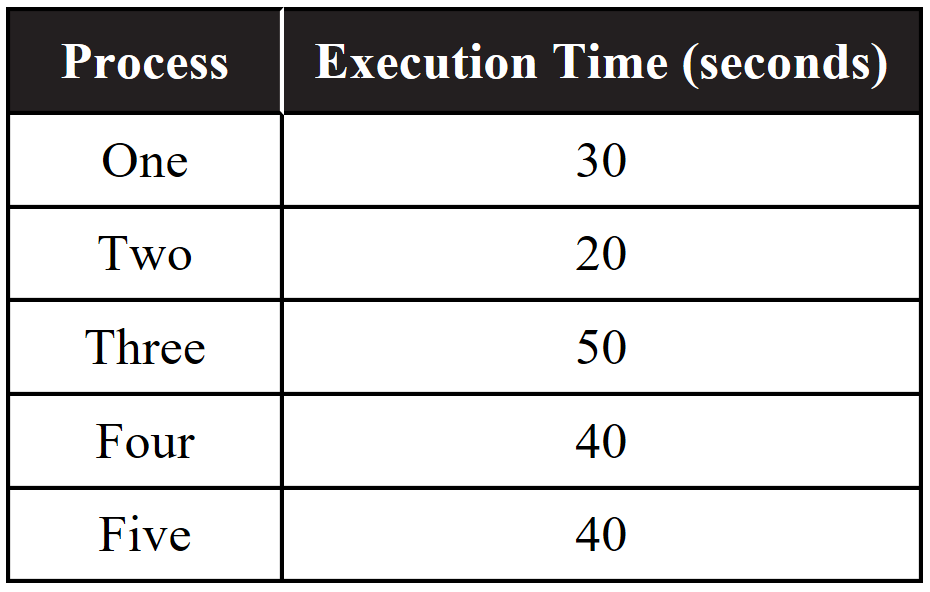
Which of the following best approximates the minimum possible time to run all five processes in parallel?
(A) 50 seconds
(B) 90 seconds
(C) 130 seconds
(D) 180 seconds
24. Which of the following algorithms is the best candidate to decrease run time by using parallel computing?
(A) An algorithm that cannot be broken down into independent operations
(B) An algorithm that can be broken down into independent operations
(C) An algorithm that is run on a single-processor machine
(D) An algorithm that has only one operation
25. When run in series, a program that checks pictures for ears takes 1,000 seconds to check 100 pictures. When running the same program in parallel, the two programs take 10 seconds to check 100 pictures. What is the speedup for the parallel solution?
(A) 1
(B) 10
(C) 100
(D) 1,000
26. When run in series, a program that sorts data takes 40 seconds to sort 300 students based on GPA. When running the same program in parallel, the two programs still take 40 seconds to run. What is the speedup for the parallel solution?
(A) 1
(B) 10
(C) 100
(D) 1,000
27. A program to encrypt pictures has different run times based on the resolution of the picture. The following table indicates the run times versus megapixels to process a picture.
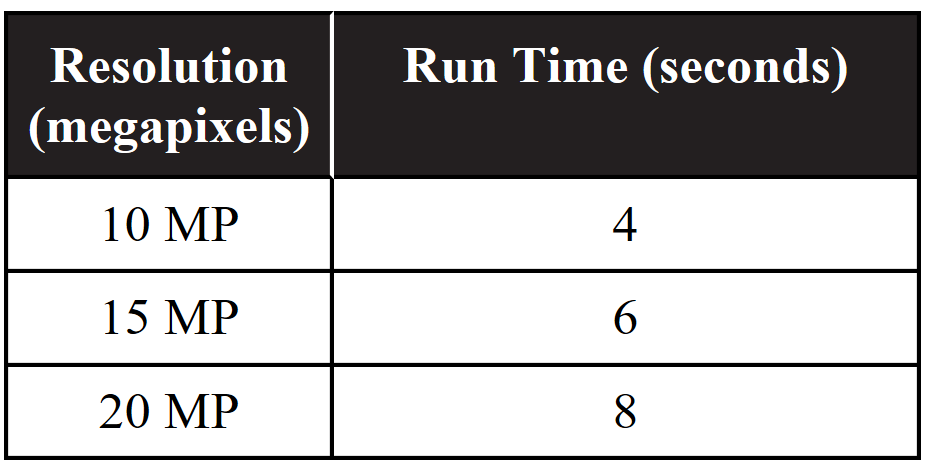
If the program takes 3 seconds for setup and can run processes in parallel using two processors, how long will the series/parallel solution take if two 10 MP, one 15 MP, and one 20 MP pictures need to be processed, assuming the four processes are not dependent on each other?
(A) 5 seconds
(B) 10 seconds
(C) 15 seconds
(D) 20 seconds
28. To predict the path of a hurricane, a programmer needs to use an extremely large volume of data reported by thousands of sensors. This problem is so large and complex that it is impractical to solve on a single computer, so the programmer decides to use a distributed computing solution.
How can a distributed computing solution help speed up the time needed to execute the program?
(A) A distributed computing solution can speed up run time by using multiple computers in parallel.
(B) A distributed computing solution can speed up run time by using multiple computers in series.
(C) A distributed computing solution can speed up run time by using multiple processors in parallel on a single computer.
(D) A distributed computing solution can speed up run time by using multiple processors in series on a single computer.
29. A program that sorts data takes 10 seconds to sort 300 students based on GPA when run on a single computer. When the same program is run using two computers in parallel, the programs takes 5 seconds to run. What is the speedup for the parallel distributed solution?
(A) 1/4
(B) 1/2
(C) 1
(D) 2


.png)


