Practice Exercises - AP Computer Science Principles 2024
CREATIVE DEVELOPMENT QUESTIONS
1. Which of the following is NOT true about a computing innovation?
(A) A computing innovation includes a program as an integral part of its function.
(B) A computing innovation can have a physical side to it.
(C) A computing innovation can be nonphysical.
(D) A computing innovation can be purely hardware.
2. Where can the inspiration for a computing innovation come from?
(A) Inspiration for computing innovations can be found anywhere.
(B) Innovations build on previous innovations only.
(C) Customer needs are the sole driving force of new computing innovations.
(D) Money is the sole driving force of new computing innovations.
3. Who or what creates computing innovations?
(A) Industry
(B) People
(C) Companies
(D) Other innovations
4. Which of the following traits is NOT necessary for effective collaboration?
(A) Communication
(B) Consensus building
(C) Proximity
(D) Conflict resolution and negotiation
5. What is a program?
(A) A collection of program statements that perform a specific task when run by a computer
(B) A collection of program statements that are part of an algorithm
(C) How software behaves and how it functions
(D) A code segment
6. What is a code segment?
(A) A collection of program statements that perform a specific task when run by a computer
(B) A collection of program statements that are part of a program
(C) How software behaves and how it functions
(D) An innovation that solves a problem
7. What is true about program input?
(A) A program can have many inputs, but they all need to be of the same type.
(B) A single program takes in a single input and has a single output.
(C) A program’s input needs to be text based.
(D) Input can come in a variety of forms, such as tactile, audio, visual, or text.
8. What is NOT true about an event?
(A) An event is associated with an action and supplies input data to a program.
(B) An event does not affect the sequence of a program.
(C) An event can be triggered by a mouse click.
(D) An event affects the flow of execution of a program.
9. The design of a program incorporates investigations to determine its requirements. Most programs are designed to be used by people other than the programmers. To meet the needs of the users, the investigation must identify the program constraint, as well as the concerns and interests of the people who will use the program.
Which of the following is NOT an investigation tool for designing programs?
(A) Programming the most elegant code
(B) Collecting data through surveys
(C) User testing
(D) Direct observations
10. What type of error will the following procedure cause?
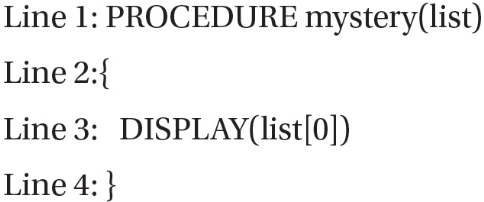
(A) Logic error on line 3
(B) Syntax error on line 3
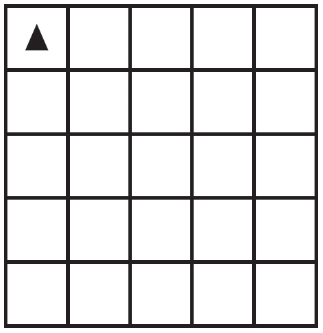
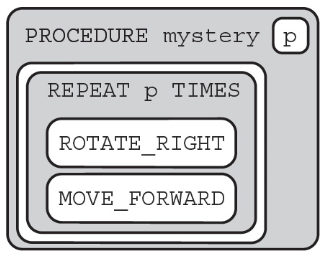
(C) Runtime error on line 3
(D) Overflow error on line 3
11. The following procedure is intended to add two variables, a and b. What type of error will the following procedure cause?
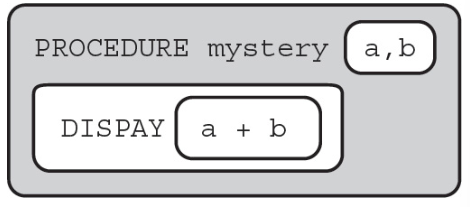
(A) Logic error on line 3
(B) Syntax error on line 3
(C) Runtime error on line 3
(D) No error
12. What type of error will the following procedure cause?
// The following procedure is intended to display 4 added to the value contained in the variable a.

(A) Logic error on line 1
(B) Syntax error on line 1
(C) Runtime error on line 3
(D) No error
13. The following program is intended to display the string 4cat4. What type of error will the following procedure cause?
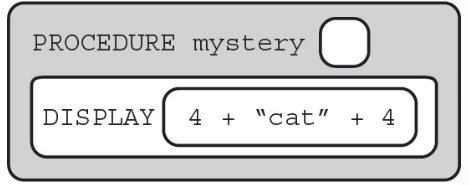
(A) Logic error
(B) Syntax error
(C) Runtime error
(D) No error
14. What type of error will the following procedure cause?

(A) Logic error on line 1
(B) Syntax error on line 1
(C) Runtime error on line 3
(D) No error
15. What type of error will the following procedure cause?

(A) Syntax error on line 1
(B) Syntax error on line 3
(C) Runtime error on line 3
(D) No error
16. What is the largest number that will not cause an overflow error using 1 bit of storage?
(A) 0
(B) 1
(C) 2
(D) 3
17. What is the largest number that will not cause an overflow error using 3 bits of storage?
(A) 3
(B) 6
(C) 7
(D) 8
18. How many numbers can 1 bit of storage hold?
(A) 0
(B) 1
(C) 2
(D) 3
19. How many numbers can 4 bits of storage hold?
(A) 0
(B) 4
(C) 15
(D) 16
20. What type of error will the following procedure cause?

(A) Logic error on line 3
(B) Syntax error on line 1
(C) Runtime error on line 3
(D) No error
21. A programmer is working on an algorithm to sort students by their grade point averages. The program will run but is not correctly sorting students. The programmer has tried to debug the program but cannot figure out where the error is occurring.
Which of the following will most likely lead to fixing the program?
(A) Post the program on social media and hope someone will quickly find and fix the error.
(B) Redesign the program so sorting is no longer a function.
(C) Ask a peer with fresh eyes to look over the code and hopefully find the solution together.
(D) Take code from the internet that sorts numbers and change the code to the correct variables.
22. Which of the following is NOT a characteristic of collaborating?
(A) The location of the collaboration should be in one neutral physical location similar to a conference room.
(B) Collaboration that includes diverse perspectives can help to avoid bias in the development of computing innovations.
(C) Collaboration requires that individuals have interpersonal skills to collaborate effectively.
(D) All of the above.
23. A programming team is developing a computer game where a troll is on an adventure while throwing bugs and boogers at frogs to gain points while making burping noises. Although the game runs smoothly without any errors, both adults and children said they do not like the theme of the game and would not play it on their own. Which of the following steps in the design process should the programmers revisit first?
(A) Investigating and reflecting
(B) Testing code
(C) Prototyping
(D) Designing
DATA QUESTIONS
1. Computers are described as processing data iteratively. In what order will the computer process the following program?
Line 1: a ← 38
Line 2: b ← 54
Line 3: a ← b + a
Line 4: DISPLAY(a + b)
(A) A computer will process all lines of code at once.
(B) A computer will process the metadata before the pure data.
(C) A computer will process data one step at a time in the given 1, 2, 3, 4 order.
(D) A computer will display the value 92 while processing lines 1, 2, 3, and 4 at the same time.
2. An Alaskan biologist is tracking a pod (group) of whales using tracking collars. For the whales, the following geolocation data are collected at frequent intervals:
■ Time
■ Date
■ Geographical location of the sea mammals
Which of the following questions about a whale could NOT be answered using only the data collected from the tracking collars?
(A) Approximately how many miles did the animal travel in one week?
(B) Does the animal travel in groups with other tracked animals?
(C) Do the movement patterns of the animal vary according to the weather?
(D) In what geographic location does the animal typically travel?
3. Large data sets are useful in finding patterns in the data that can predict future usage. Which of the following is used to predict future usage?
(A) Calculating the monthly bill charged
(B) Using past purchases to recommend products for possible purchase
(C) Identifying the largest-spending addresses
(D) Identifying the time at which most purchases are made
4. Suppose that a company is creating an algorithm that matches people to advertisements in which they might have an interest. The company is basing its algorithm on a data source accumulated from data bought from social media. Which of the following sources would be useful for the algorithm?
(A) Information about a person’s video-watching preferences (whether they watch viral videos, reviews, animations, etc.)
(B) A social network’s information on what sites a person likes and follows
(C) Information on a person’s previous purchases
(D) All of the above
5. A short message service (SMS) can be sent from one phone to another phone. Once the message is converted into binary form, it is sent by radio waves to the control tower. Once the SMS travels through the control tower, it arrives at the short message service center to be stored or sent immediately. In addition to sending the SMS, the cell phone carrier sends metadata.
Which of the following is NOT metadata?
(A) The time the message was sent and received
(B) The content of the SMS
(C) The geographic location of both the sender and the receiver
(D) The phone number of both the sender and the receiver
6. Spotify is a music-streaming service that uses collected metadata to suggest future playlists. The metadata contain the album name, the genre, the tags describing the music, the mood of the music, and the time and date the music was played.
Which of the following CANNOT be determined using only the information contained in the metadata?
(A) The most popular current album
(B) The time when the streaming service is used
(C) Whether the streaming service is used more during the celebration parade for the Mets winning the World Series
(D) The least common mood of the audience
7. An online e-commerce site maintains a database containing the following information:
■ Price
■ Colors
■ Quantity available
■ Customer comments from the purchasing public
Using only the database, which of the following CANNOT be determined?
(A) How some of the buying public feel about their purchases
(B) The popularity of a color depending on the season
(C) What color sold the most product
(D) The average price paid for each color
8. Google Trends is a website by Google that analyzes the popularity of top search queries in Google Search across various regions and languages. The large number of searches make Google Trends one of the world’s largest real-time data sets. Which of the following is Trends data most likely to answer?
(A) Whether the public is concerned about the celebration parade for the Jets winning the Superbowl
(B) What date is the cheapest date to book a hotel room
(C) The cost of a gas-powered chainsaw
(D) The length of the Iditarod (a popular sled dog race in Alaska) in meters
9. In 2000, the Chicago Public Schools set up a computing algorithm to detect teachers who had changed their students’ answers on standardized tests. The algorithm looked at students’ answers, with letters representing correct answers, a 0 representing a blank answer, and other numbers representing an incorrect answer. Which of the following is a way that the algorithm could have used this data?
(A) To look for consecutive answer patterns shared by students in the same class
(B) To look at the number of correct answers on harder questions
(C) To look for consecutive correct answers shared by students in the same class
(D) To look at the percentage of students who passed the test
10. A large data set contains information on students about to take the College Board’s SAT test, including the following:
■ The student’s parents’ highest education level
■ The student’s grade point average (GPA)
■ The student’s intended college major
■ The college that the student is interested in attending
■ The student’s current address
■ The student’s high school name and location
Which of the following could NOT be answered by analyzing only information in the student data set?
(A) The number of students accepted to a college
(B) The number of students interested in a particular college major
(C) The average GPA for students with an intended college major
(D) The college with the most interest from a particular high school
11. Suppose a team is creating a program that contains several different data-based algorithms. Which of the following would be the most effective strategy for creating algorithms?
(A) Each algorithm is created by the entire group before the next one is started.
(B) Each algorithm is created by a different member, and one member tries to implement the different algorithms as they are completed.
(C) Each algorithm is created by a different member and is implemented by the entire group after all algorithms are completed.
(D) Each algorithm is created by a different member based on strengths and experiences that the group agrees on at the start of programming.
12. Why might it be more beneficial to create processing algorithms with a team rather than alone? Select two answers.
(A) Different team members will have different understandings of the concepts used, which can create stronger algorithms through their incorporation.
(B) Team coding guarantees that all team members will do an equal share of work and perform at a high level.
(C) Team members will compete with each other, resulting in an increase in trust between partners and eliminating the need for personal conflict resolution.
(D) Different team members will be skilled in different areas, so each part of the algorithm can be made by the most skilled in the necessary area.
13. What predictions can be made by using only the data provided in the following table?

(A) Doubling the mass results in half the time required to fall 1 meter.
(B) Doubling the mass results in twice the time required to fall 1 meter.
(C) Mass has no effect on time for an object to fall 1 meter in a vacuum.
(D) Increasing the mass results in increasing the time to fall 1 meter in a vacuum.
14. The following data show growth of companies (series 1 to series 4) versus time.
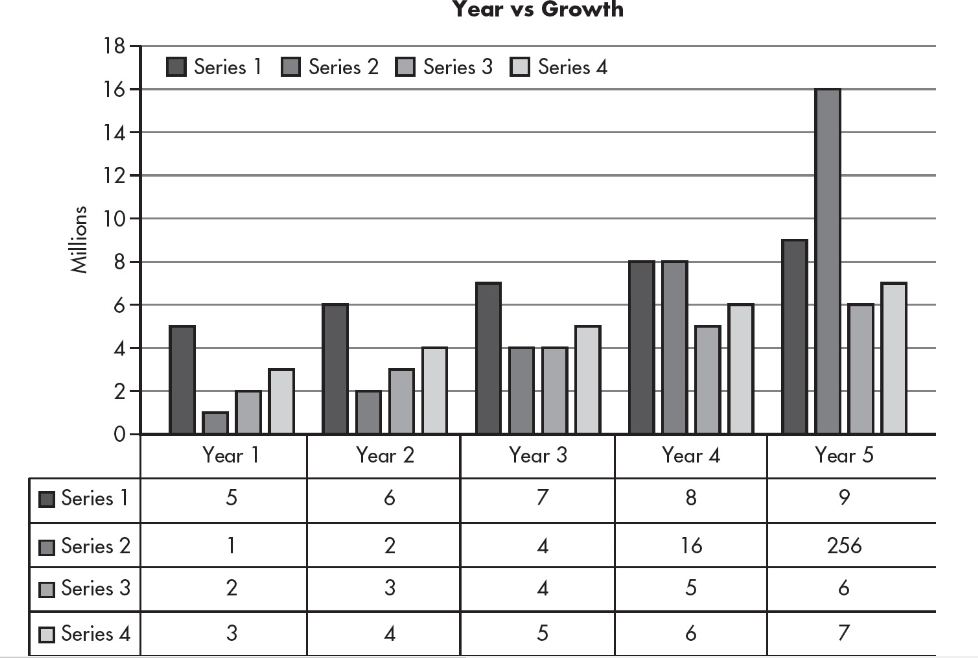
Which of the following series would most likely be predicted to show the greatest growth in year 6?
(A) Series 1
(B) Series 2
(C) Series 3
(D) Series 4
15. The following table contains types of cakes sold in cities for a date. Which of the following CANNOT be determined using only the information in the database?
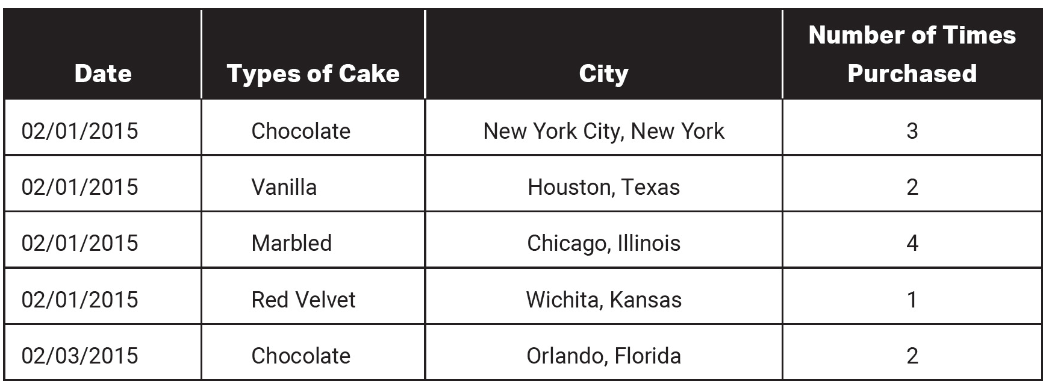
(A) The date when a certain type of cake was purchased most
(B) The total number of times chocolate cake was purchased
(C) The total number of times a bakery sold a certain type of cake
(D) Which city, Orlando or New York City, sold more chocolate cake on 02/01/2015
16. A programmer is writing a program that is intended to process large amounts of data. Which of the following is likely to affect the ability of the program to process larger data sets?
(A) How well the program is documented
(B) The order in which the data are put into the data set
(C) How much memory the program requires to run
(D) How many program statements the program contains
17. The following table details the date and location of rented movies. Which of the following CANNOT be found using the provided table?
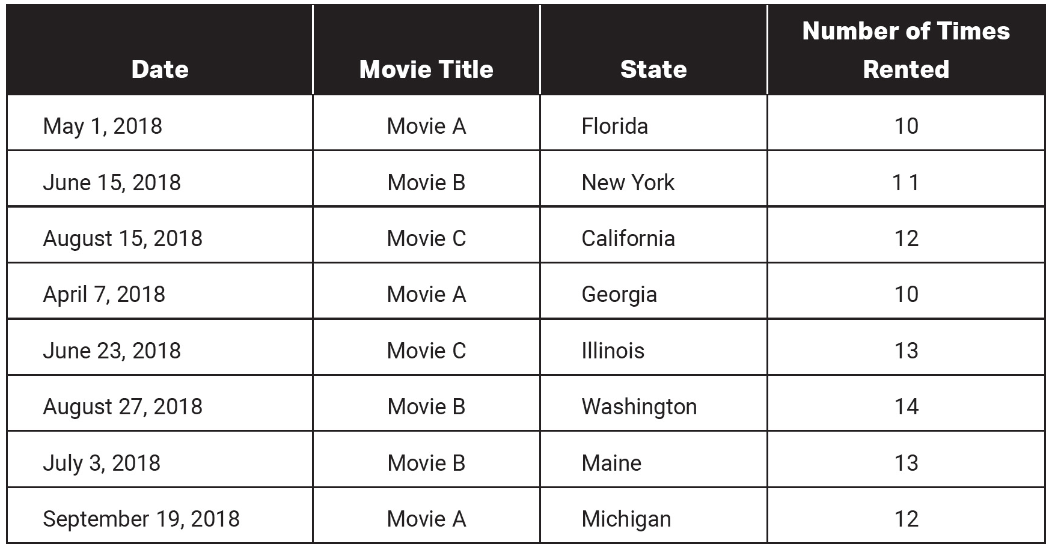
(A) The average number of rented movies for a given month
(B) The movie that was rented the most overall for all time periods
(C) The number of times an individual person rented a movie
(D) The movies that were rented more than 12 times for any time period
18. Some computer science companies have certain rules that employees must meet face-to-face or over video chat a certain amount of times per week. What is the importance of these face-to-face meetings?
(A) Face-to-face interactions make it easier to share and discuss information used in the project, compared to impersonal methods such as messaging.
(B) Face-to-face interactions are more convenient than any other form of communication.
(C) Impersonal methods such as messaging are more expensive than face-to-face methods.
(D) Face-to-face methods are more time efficient than impersonal methods.
19. Why do most data-analyzing programs include options for creating graphs?
(A) Graphs are less taxing on the computer’s graphics card than a plain spreadsheet.
(B) Graphs make it easier to interpret data values, trends, and proportions, so they are an incredibly useful feature.
(C) It is easier to code a graph-based data analyzer than a spreadsheet-based one.
(D) It is harder to make spreadsheets properly display because the resulting file is not an image.
20. When the findings from a project are presented, they are typically presented using a graph as opposed to a table or raw data. Why might this be? Select two answers.
(A) Graphs can be easily placed into a slideshow or document, while tables cannot.
(B) Graphs can show trends that might not be easily seen with raw data.
(C) Graphs are able to show all the details necessary to understand data.
(D) Graphs are easier to read and interpret at a glance.
21. Google’s website Trends provides information about the frequency of searches made using the search engine. Why might this be more useful than a similar tool offered by less popular search engines? Select two answers.
(A) Google is the largest search engine, so its results are guaranteed to be accurate.
(B) Google is a more popular search engine; therefore, it will have a larger data set, creating more accurate data.
(C) The less popular search engines might primarily be used by certain demographics (scholars, politicians, etc.), distorting the data in comparison to the broad reach of Google.
(D) Google tracks the popularity of websites present in its search results, so it can show more accurate data about its responses.
22. Which of the following is a uniquely useful feature of search engines?
(A) The ability to distinguish among different versions of something (e.g., differentiating a 1984 film from its 2005 remake)
(B) The ability to find and filter information from a large variety of sites
(C) The ability to find basic information, such as creators or release dates
(D) The ability to find information originally released in print form
23. Suppose that a team was creating an online registry of the books in a library system. The purpose of the registry is to make it easier to find a certain book by using both filters and searches. Which of the following would NOT be a useful way for a user to filter the entries?
(A) The genre of the book
(B) The library/libraries in the system that have a copy of the book
(C) The author of the book
(D) The number of letters in the book’s title
24. A small business needed a way to keep track of its profit and expenses daily. The following are features of the spreadsheet application. Which of the following would be of most use to the business? Select two answers.
(A) The ability to create a graph of the data easily
(B) The ability to create and add map charts
(C) The ability to have specified rows (such as total profit) update automatically
(D) An error checker that finds errors in advanced formulas
25. Which of the following is an example of metadata that serves to be descriptive of the content of a file?
(A) User-selected tags (e.g., “vacation” and “personal work”)
(B) File size
(C) Date created
(D) Program used to read the file
26. Which of the following are ways the use of metadata improves the use of actual data?
(A) Files can be sorted by date of creation to make finding an old file easier.
(B) The “author” and “organization” fields in documents can be used to keep track of the source of a document.
(C) The length of a set of videos can be used to determine the way that those videos should be presented.
(D) All of the above
27. Why might it be far harder for companies to maintain the privacy of larger data sets than smaller ones? Select two answers.
(A) Larger data sets are less secure simply by nature of their size.
(B) Larger data sets might have more opportunities for attacks because they tend to have more access channels.
(D) Larger data sets are bigger targets for hackers, so they are more likely to receive attacks more sophisticated than security protocols can handle.
(E) Larger data sets are easier for thieves to navigate.
28. Why is it important that online systems with large data sets be scalable?
(A) If the workload placed on the system increases, the resulting decrease in performance can be mitigated.
(B) If the workload placed on the system increases, the resulting increase in performance can be mitigated.
(C) If a system is scalable, all future programs will run faster.
(D) If a system is scalable, all future programs are guaranteed to run properly.
29. Which of the following is an example of a way to improve the transmission of large data sets?
(A) Encryption—it uses a public key to scramble the code and requires a specific private key for the code to be reassembled properly.
(B) Compression—files are made smaller by utilizing an algorithm and then must be uncompressed by the receiver.
(C) Ping—a client and server periodically send small messages to each other to ensure that the connection between them has not been severed.
(D) Emulation—a computer runs a program that allows the computer to behave like another machine.
30. Which of the following is an inherent trade-off from the ease of handling a file when using lossy compression?
(A) Smaller file size (bytes)
(B) Speed of transmitting file
(C) Image quality
(D) Image size (number of pixels)
31. Which of the following is a way to protect data containing personal information?
(A) Encryption—it uses a public key to scramble the code and requires a specific private key for the code to be reassembled properly.
(B) Compression—files are made smaller by utilizing an algorithm and then must be uncompressed by the receiver.
(C) Ping—a client and server periodically send small messages to each other to ensure that the connection between them has not been severed.
(D) Emulation—a computer runs a program that allows the computer to behave like another machine.
32. Convert 100001BIN to a decimal number.
(A) 29
(B) 31
(C) 33
(D) 63
33. Convert 111111BIN to a decimal number.
(A) 29
(B) 31
(C) 33
(D) 63
34. Convert 3DEC to a binary number.
(A) 10BIN
(B) 11BIN
(C) 110BIN
(D) 111BIN
35. Convert 7DEC to a binary number.
(A) 10BIN
(B) 11BIN
(C) 110BIN
(D) 111BIN
36. Convert 10DEC to a binary number.
(A) 1000BIN
(B) 1010BIN
(C) 1100BIN
(D) 1111BIN
37. Convert 30DEC to a binary number.
(A) 10000BIN
(B) 11000BIN
(C) 11010BIN
(D) 11110BIN
38. Convert 32DEC to a binary number.
(A) 100000BIN
(B) 110000BIN
(C) 110100BIN
(D) 111000BIN
39. Convert 48DEC to a binary number.
(A) 100000BIN
(B) 110000BIN
(C) 110011BIN
(D) 111000BIN
40. Convert 97DEC to a binary number.
(A) 1000000BIN
(B) 1100001BIN
(C) 1100111BIN
(D) 1110001BIN
41. Convert 10100001BIN to a decimal number.
(A) 29DEC
(B) 47DEC
(C) 161DEC
(D) 178DEC
42. Convert 101111BIN to a decimal number.
(A) 29DEC
(B) 47DEC
(C) 161DEC
(D) 178DEC
43. What is the value in binary of 1100BIN + 1DEC?
(A) 1101BIN
(B) 1110BIN
(C) 1111BIN
(D) 10000BIN
44. What is the value in binary of 1101BIN + 1DEC?
(A) 1101BIN
(B) 1110BIN
(C) 1111BIN
(D) 10000BIN
45. What is the value in binary of 1111BIN + 1DEC?
(A) 1101BIN
(B) 1110BIN
(C) 1111BIN
(D) 10000BIN
46. What is the value in binary of 11001BIN + 2DEC?
(A) 11111BIN
(B) 11101BIN
(C) 11100BIN
(D) 11011BIN
47. What is the value in binary of 11001BIN + 100BIN?
(A) 11111BIN
(B) 11101BIN
(C) 11100BIN
(D) 11011BIN
48. Convert 48DEC to a binary number.
(A) 110000BIN
(B) 110001BIN
(C) 110111BIN
(D) 111111BIN
49. Convert 63DEC to a binary number.
(A) 110000BIN
(B) 110001BIN
(C) 110111BIN
(D) 111111BIN
50. Convert 17DEC to a binary number.
(A) 1111BIN
(B) 10001BIN
(C) 10111BIN
(D) 11111BIN
51. What is the smallest number of bits needed to store the decimal number 7?
(A) 1
(B) 2
(C) 3
(D) 4
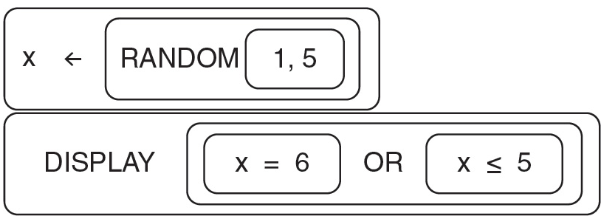
52.
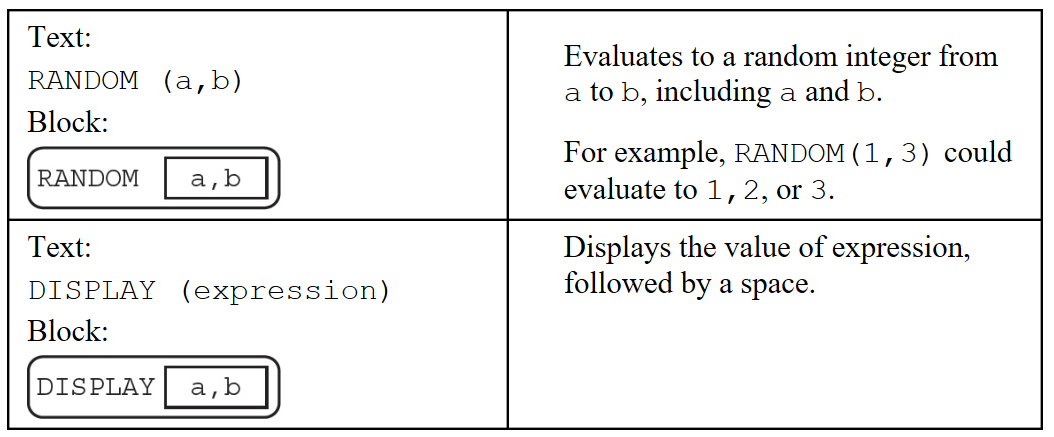
Which of the following is NOT a possible displayed value using the RANDOM(a, b) and DISPLAY(expression) abstractions?

(A) 2
(B) 4
(C) 5
(D) 6
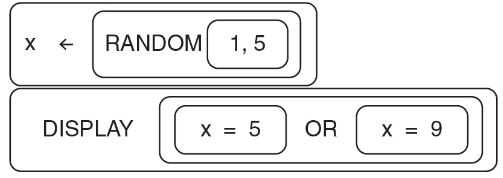
53. Which of the following is NOT a possible displayed value using the RANDOM (a, b) and DISPLAY(expression) abstractions?
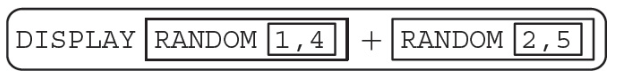
(A) 9
(B) 6
(C) 5
(D) 1
54. Which number will result in an overflow error in a 3-bit system?
(A) 3
(B) 4
(C) 6
(D) 8
55. Which of the following will result in an overflow error in a 4-bit system?
(A) 6
(B) 9
(C) 15
(D) 16
56. Which of the following is the largest number that will NOT result in an overflow error in a 5-bit system?
(A) 30
(B) 32
(C) 33
(D) 34
57. Which math calculation could result in a roundoff error?
(A) 1/3
(B) 2 * 6
(C) 6 − 2
(D) 3 + 5
58. Many older computers were designed to handle only 8-bit systems, meaning that all numbers that the computers used could not exceed 8 bits in length. Which of the following numbers would NOT be viable in an 8-bit system?
(A) 14DEC
(B) 34DEC
(C) 255DEC
(D) 256DEC
59. Many computing languages store an integer in 4 bytes, limiting the range of numbers to from 2,147,483,648 to −2,147,483,647. Given that numbers can be of infinite size, why is this limitation put in place? Select two answers.
(A) Programmers need numbers to be as small as possible because that limits overflow errors.
(B) Most computed numbers are within this range, so 4 bytes is a reasonable size for most purposes.
(C) Making a very large, almost infinite integer would require so much space that it would be impractical for most uses.
(D) No programmer ever needs a number outside of this range, so there’s no point in extending the limit.
60. A programmer working for an architect needs to create a program to describe several properties with given names, areas, and images. Assume that the properties behave in an identical manner. What would be a benefit of creating an abstraction that uses these three parameters?
(A) The parameters would allow all the objects to hold their own properties without requiring each to be coded separately.
(B) The abstraction would be able to account for every difference in the way the objects behave.
(C) The abstraction would make them harder to include in the code, which makes stealing and editing the program code more difficult.
(D) The use of an abstraction would ensure that each object’s files can be edited.
61. Find the error in the following low-level programming code.
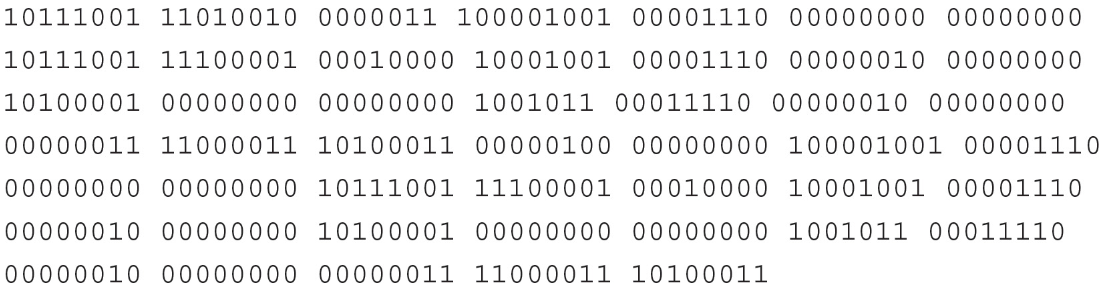
(A) The 17th 1 needs to be changed to a 0.
(B) This is too difficult. To determine errors, it would be considerably easier to use an upper-level language.
(C) The 34th 0 should be a 1.
(D) The 84th digit should be a 1.
62. Which of the following phrases would have the highest lossless compression rate?
(A) She loves you, yeah, yeah, yeah.
(B) The quick brown fox jumps over the lazy dog.
(C) Sphinx of black quartz, judge my vow.
(D) How razorback-jumping frogs can level six piqued gymnasts!
63. Using the following abbreviation table, reconstruct the lossless compression to its original form.
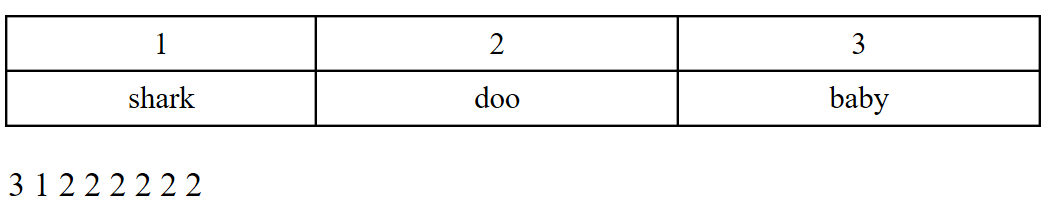
(A) shark doo baby
(B) baby shark doo 6
(C) baby shark doo doo doo doo doo doo
(D) baby shark doo
64. Why is it usually easier to read code written in a high-level language than code written in a low-level language?
(A) High-level languages tend to be written by smarter people.
(B) High-level languages tend to be closer to basic computer code, which makes them easier to translate.
(C) High-level languages tend to be written for more experienced programmers to use, which implicitly makes them easier to read.
(D) High-level languages tend to be closer to natural language by utilizing simplified abstractions with descriptive names.
65. The abstraction Draw(magnitude, direction) is used to draw line segments at a given magnitude and direction (north, south, east, or west) starting at the tip of the first vector and ending at the tail of the second vector. Consider the following program, where the vector starts in the upper-left corner of a grid of dots.
Draw(2, south)
Draw(1, east)
Draw(2, east)
Draw(1, north)
Which of the following represents the figure that is drawn by the program?
(A)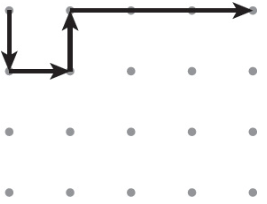
(B)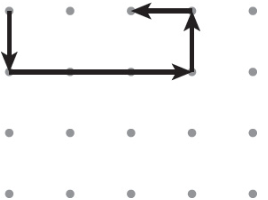
(C)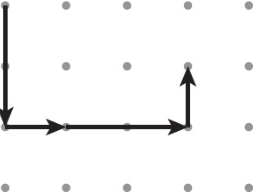
(D)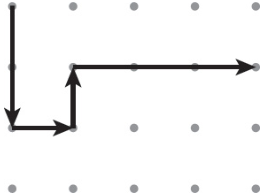
66. When taken as a whole, is a physical computer low-level or high-level abstraction?
(A) Low level, because the computer processes the lowest-level form of software.
(B) High level, because the computer contains many low-level components, such as the CPU.
(C) High level, because the computer is capable of utilizing high-level programming languages.
(D) Neither, as a computer is not software.
67. Logic gates are physical hardware that are used to determine Boolean functions such as AND and OR. Given this, are Boolean functions abstractions?
(A) Yes, they represent the activity of these gates in a manner that can be coded.
(B) Yes, they represent the physical presence of the gates.
(C) No, they are performed by processors; logic gates are merely a way to visualize this.
(D) No, they are not abstractions because they deal with things at the bit level.
68. A theme park wants to create a simulation to determine how long it should expect the wait time at its most popular ride. Which of the following characteristics for the virtual patrons would be most useful? Select two answers.
(A) Ride preference—denotes whether a patron prefers roller coasters, other thrill rides, gentle rides, or no rides.
(B) Walking preference—denotes how far a patron is willing to walk in between rides.
(C) Food preference—denotes the type of food that a patron prefers to eat (e.g., chicken, burgers, salads).
(D) Ticket type—denotes whether the patron has a single-day pass, a multiday pass, or an annual pass.
69. A programmer has created a program that models the growth of foxes and rabbits. Which of the following potential aspects of the simulation does NOT need to be implemented?
(A) Grass that rabbits must eat frequently to survive is represented.
(B) Each rabbit may have only a certain number of children per litter.
(C) Each fox must eat a rabbit frequently to survive.
(D) Each rabbit can live only to a certain age, assuming that it is not eaten.
70. When the FAA investigates plane crashes, it often has high-level pilots replay the scenario to see if the situation could have been avoided. This is typically done using a moving simulator as opposed to an actual airplane. Why?
(A) A simulator is much clumsier to pilot than a real airplane, so the pilots being successful is proof that an amateur pilot would be successful as well.
(B) A simulator is much easier to pilot than a real airplane, so the pilots failing is proof that any pilot would be unsuccessful.
(C) If the crash could not be properly avoided, it would be much more expensive to replace a simulator than an actual airplane.
(D) If the crash could not be properly avoided, using an actual airplane would put the pilots (and potentially others) in mortal danger.
71. The heavy use of chemicals called chlorofluorocarbons (CFCs) has caused damage to Earth’s ozone layer, creating a noticeable hole over Antarctica. A scientist created a simulation of the hole in the layer using a computer, which models the growth of the hole over many years. Which of the following could be useful information that the simulation could produce?
(A) The approximate length of time until the hole would be refilled (due to various atmospheric processes)
(B) The exact size of the hole at any given point in time
(C) The exact length of time until the hole would be refilled (due to various atmospheric processes)
(D) The exact depth of the hole at any point in time
72. Suppose that an environmentalist wanted to understand the spread of invasive species. What would be a benefit of doing this with a simulation rather than in real life?
(A) The species used in the simulation could be designed to mimic many different species at once.
(B) The species created could be quickly tested in multiple environments to understand better how its spread is affected by environmental factors.
(C) The simulation could be run much more quickly than in real life.
(D) All of the above.
73. A program is being created to simulate the growth of a brain based on randomly determined environmental factors. The developer plans to add a feature that lets the user quickly run several hundred simulations with any number of factors kept constant. Why would this be useful? Select two answers.
(A) It would allow the user to gather data without taxing the computer’s hardware.
(B) It would allow the user to see the effect of specific variables by ensuring that the other variables do not change.
(C) Several hundred simulations would guarantee the simulation will accurately model the growth of the brain.
(D) It would make simulations more detailed.
74. What is displayed using the following DISPLAY(expression) abstractions?
List1 ← [11, 35, 6]
DISPLAY(List1[2])
(A) An error message is produced, and the program will terminate.
(B) 35
(C) 11
(D) 6
75. What is displayed using the following DISPLAY(expression) abstractions?
List1 ← [11, 35, 6]
DISPLAY(List1[0])
(A) An error message is produced, and the program will terminate.
(B) 35
(C) 11
(D) 6
76. Which of the following characteristics does NOT represent digital data?
(A) A constant stream of smoothly changing data
(B) Discrete levels that represent the size of the data
(C) Samples of the data at regular intervals
(D) Digital data approximately representing the analog signal but not exactly
77. The signal below is an example of what type of signal?
(A) Analog signal
(B) Digital signal
(C) Static signal
(D) Random signal
78. What signal can be represented using a digital signal without losing any data?
(A) The human voice in air
(B) The varying temperature during the day
(C) Volume due to a train honking its horn
(D) The varying grades of a student during the school year
ALGORITHMS AND PROGRAMMING QUESTIONS
1. What will the following algorithm display?
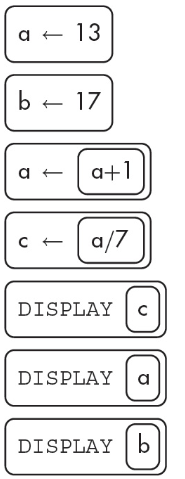
(A) 2 14 17
(B) 13 17 5
(C) 2 12 2
(D) 14 17 2
2. What will the following algorithm display?
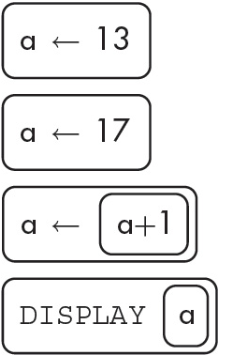
(A) 13
(B) 17
(C) 18
(D) 19
3. What will the following algorithm display?
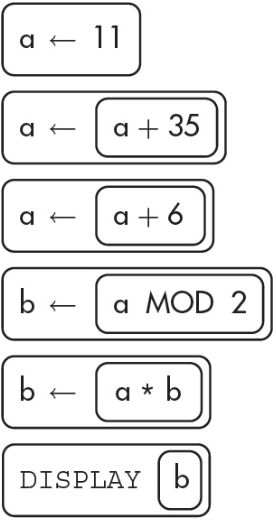
(A) 0
(B) 42
(C) 84
(D) 126
4. What will the following algorithm display?
(A) Milk
(B) Milk Cookies Soda
(C) put them in a bag and they stay crisp
(D) Milk Cookies Soda Chips put them in a bag so you know they stay crisp
5. What is the value displayed after the program is run?
(A) a 8
(B) a 6
(C) 8 6
(D) 16 4
6. What is the value displayed after the program is run?
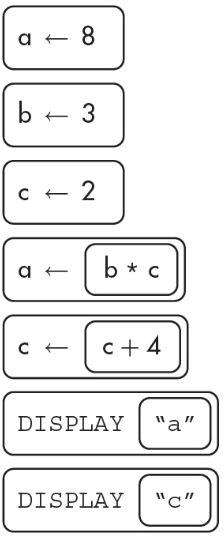
(A) a 8
(B) a c
(C) 8 6
(D) 16 4
7. What will the following algorithm display?
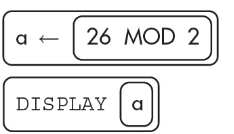
(A) 26
(B) 13
(C) 1
(D) 0
8. What will the following algorithm display?
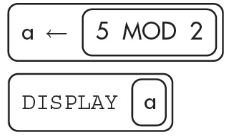
(A) 26
(B) 13
(C) 1
(D) 0
9. What will the following algorithm display?
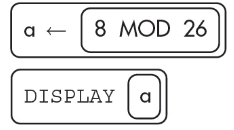
(A) 26
(B) 13
(C) 8
(D) 1
10. What will the following algorithm display?
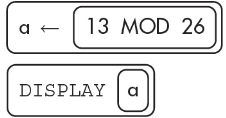
(A) 26
(B) 13
(C) 8
(D) 0
11. What will the following algorithm display?
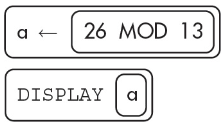
(A) 26
(B) 13
(C) 2
(D) 0
12. What will the following algorithm display?
(A) 26
(B) 13
(C) 1
(D) 0
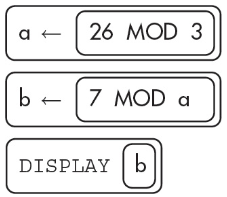
13. What will the following algorithm display?
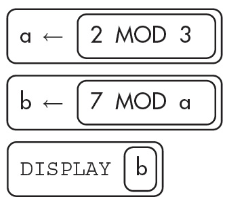
(A) 26
(B) 13
(C) 1
(D) 0
14. What will the following code segment display?
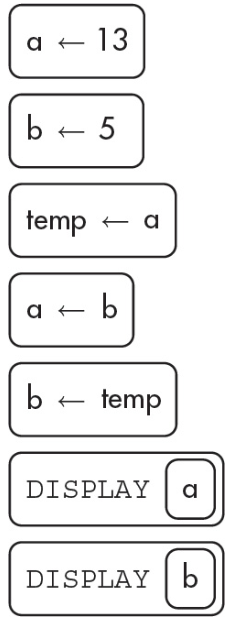
(A) 13 5
(B) 5 13
(C) a b
(D) 13 13
15. If this statement is executed many times, about what percentage of times does it display true?

(A) 9%
(B) 10%
(C) 60%
(D) 100%
16. If this statement is executed many times, about what percentage of times does it display true?

(A) 10%
(B) 20%
(C) 60%
(D) 100%
17. If this statement is executed many times, about what percentage of times does it display true?

(A) 0%
(B) 20%
(C) 60%
(D) 100%
18. If this statement is executed many times, about what percentage of times does it display true?

(A) 0%
(B) 20%
(C) 60%
(D) 100%
19. If this statement is executed many times, about what percentage of times does it display true?

(A) 0%
(B) 20%
(C) 60%
(D) 100%
20. If this statement is executed many times, about what percentage of times does it display true?
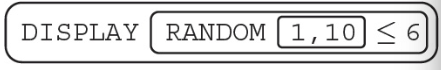
(A) 9%
(B) 10%
(C) 60%
(D) 100%
21. If this statement is executed many times, about what percentage of times does it display true?
(A) 20%
(B) 40%
(C) 60%
(D) 100%
22. If this statement is executed many times, about what percentage of times does it display true?
(A) 0%
(B) 40%
(C) 60%
(D) 100%
23. What is the percentage of times that this algorithm displays true?
(A) 0%
(B) 40%
(C) 60%
(D) 100%
24. The algorithm below displays true 60% of the time.
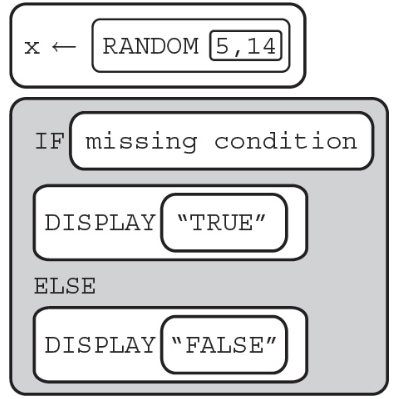
What can replace the missing condition so the code segment works as intended?
(A) x < 10
(B) x ≤ 10
(C) x > 10
(D) x ≥ 10
25. What is the value displayed after the algorithm is run?
(A) 0
(B) 1
(C) 10
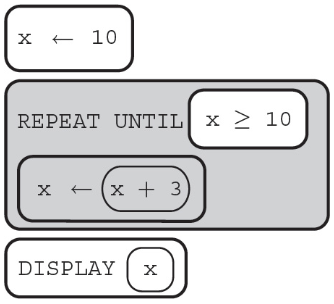
(D) 13
26. What is the value displayed after the algorithm is run?
(A) 0
(B) 1
(C) 10
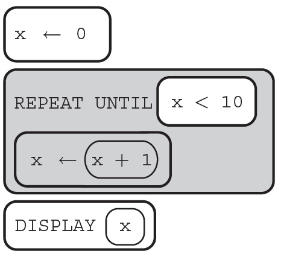
(D) 12
27. What is the value displayed after the algorithm is run?
(A) 0
(B) 1
(C) 9
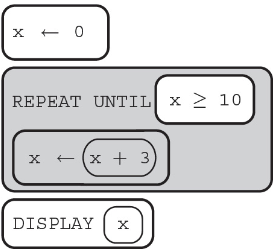
(D) 12
28. What is the value displayed after the algorithm is run?
(A) 0
(B) 1
(C) 10
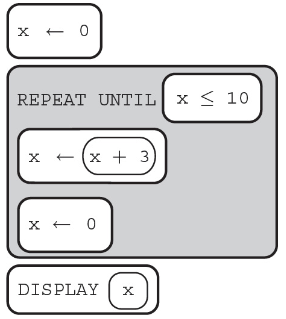
(D) Nothing is displayed due to an infinite loop.
29. What is the value displayed after the algorithm is run?
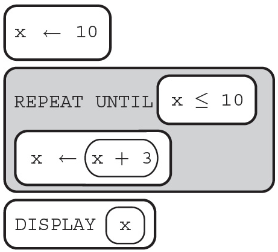
(A) 0
(B) 1
(C) 10
(D) 12
30. What is the value displayed after the algorithm is run?
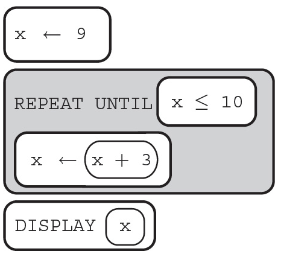
(A) 0
(B) 9
(C) 10
(D) 12
31. What is the value displayed after the algorithm is run?
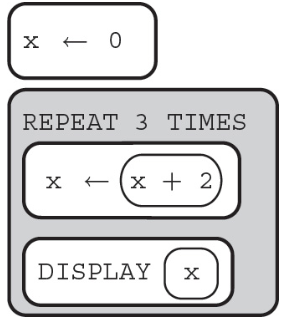
(A) 2 4 6
(B) 0 2 4 6
(C) 6
(D) 8
32. What is the value displayed after the algorithm is run?
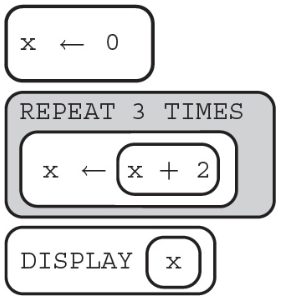
(A) 2 4 6
(B) 0 2 4 6
(C) 6
(D) 8
33. What is the value displayed after the algorithm is run?
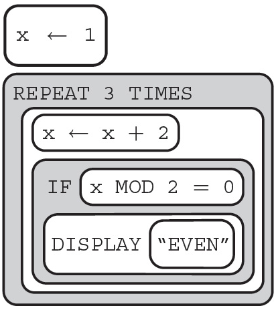
(A) Nothing is displayed.
(B) Even Even Even
(C) ODD ODD ODD
(D) 2 4 6
34. What is the value displayed after the algorithm is run?
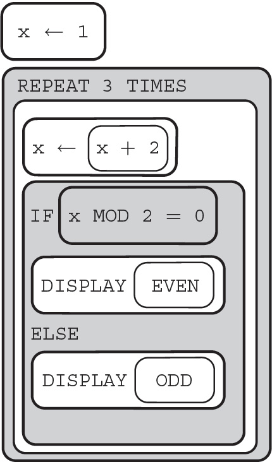
(A) Nothing is displayed.
(B) Even Even Even
(C) ODD ODD ODD
(D) 2 4 6
35. What is the value displayed after the algorithm is run?
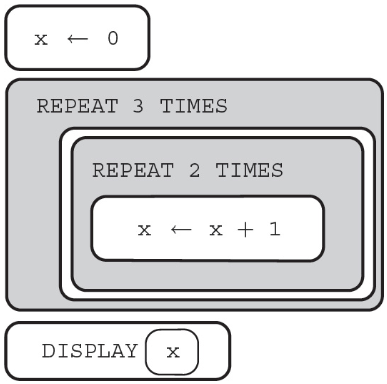
(A) 0
(B) 2
(C) 5
(D) 6
36. What is displayed after the algorithm is run?
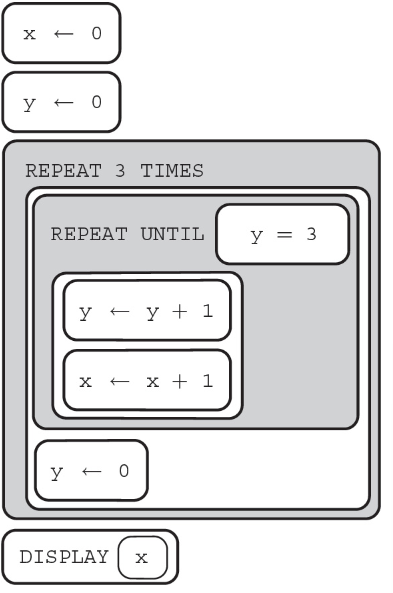
(A) 0
(B) 3
(C) 9
(D) 12
37. What is displayed after the algorithm is run?
(A) 0
(B) 3
(C) 9
(D) 12
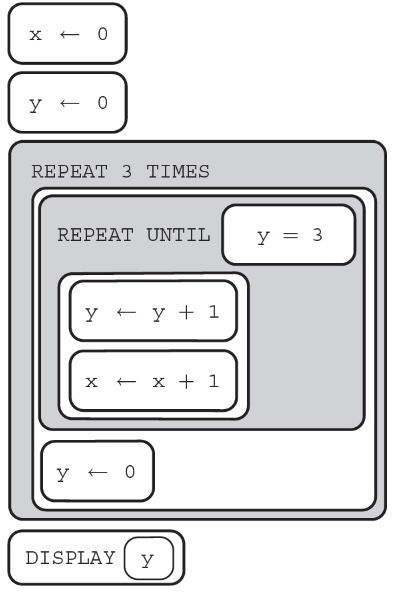
38. How many numbers will the following algorithm display?
(A) 0
(B) 10
(C) 100
(D) An infinite amount
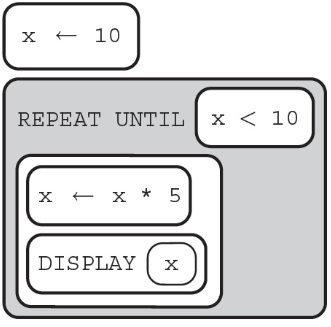
39. What will be printed when this algorithm is run?
(A) Pineapple
(B) Kumquat
(C) Star Fruit
(D) Pineapple Kumquat Star Fruit
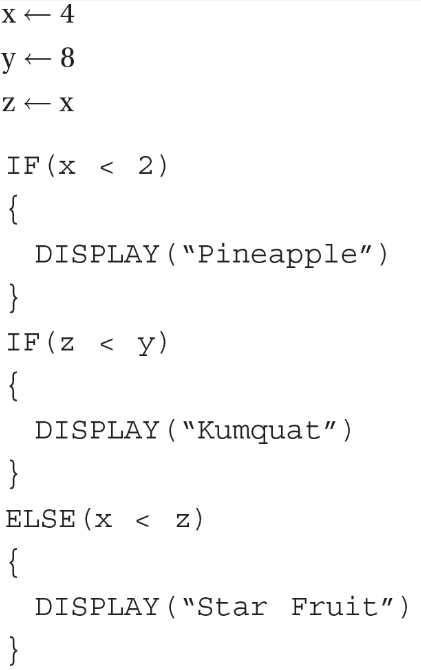
40. How many times will “fish” be displayed?

(A) 4
(B) 3
(C) 2
(D) 1
41. What is displayed at the end of the algorithm?
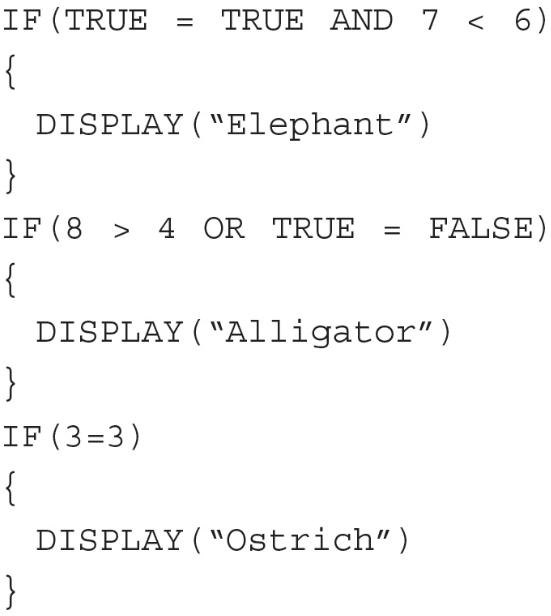
(A) Elephant
(B) Alligator Ostrich
(C) Alligator
(D) Elephant Alligator Ostrich
42. A user inputs 5 for the value of a. What is a possible value of c?
a ← INPUT( )
b ← RANDOM(a, 6)
c ← b − 6
(A) −3
(B) −1
(C) 1
(D) 3
43. The following is a truth table for all possible values of A and B.
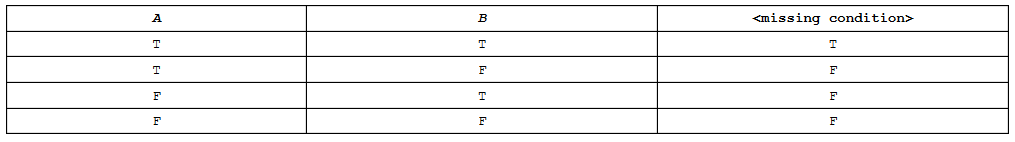 Which of the following can replace the missing condition?
Which of the following can replace the missing condition?
(A) (A AND B)
(B) (A OR B)
(C) (A OR NOT(A))
(D) (A AND NOT(A))
44. The following is a truth table for all possible values of A.
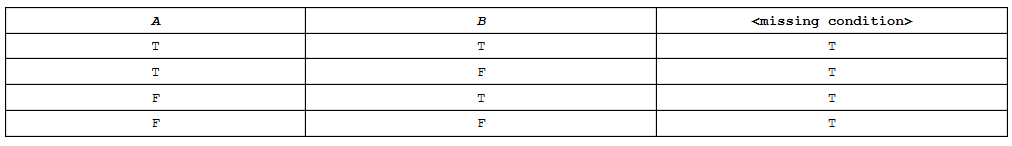 Which of the following can replace the missing condition?
Which of the following can replace the missing condition?
(A) (A AND B)
(B) (A OR B)
(C) (A OR NOT(A))
(D) (A AND NOT(A))
45. Which of the following statements describes the major building blocks of algorithms?
I. Sequencing—statements execute in a given order
II. Selection—Boolean conditions determine an algorithm’s path
III. Iteration—the repetition of parts of an algorithm
(A) I only
(B) I and II only
(C) II and III only
(D) I, II, and III
46. A programmer is writing code to display the difference of the squares of two user-inputted numbers (i.e., a2 − b2). The following lines represent parts of the code. What order should they be placed in?
1. DISPLAY(a - b)
2. b ← INPUT()
3. a ← a * a
4. a ← INPUT()
5. b ← b * b
(A) 1, 2, 3, 4, 5
(B) 1, 2, 4, 5, 3
(C) 2, 4, 3, 5, 1
(D) 4, 2, 5, 1, 3
47. An algorithm compares the user-inputted number picked to the randomly selected number drawing and calls the method victoryJingle( ) if the two are the same. What should replace in the following algorithm?

(A) IF(picked AND drawing)
(B) IF(picked = drawing)
(C) IF(picked ≠ drawing)
(D) IF(picked NOT drawing)
48. Using the program below, where will the robot land after the code segment executes?
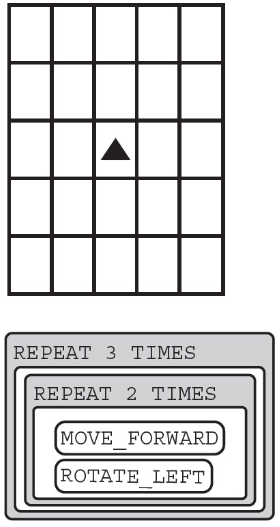
(A)
(B)
(C)
(D)
49. Using the program below, which of the following is a possible landing spot after the code segment executes?
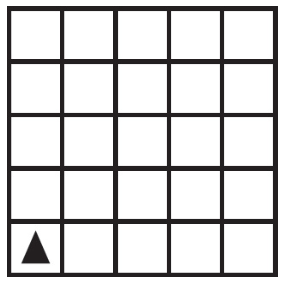
Line 1: move ← INPUT()
Line 2: REPEAT move TIMES
Line 3: {
Line 4: MOVE_FORWARD()
Line 5: ROTATE_RIGHT()
Line 6: }
(A)
(B)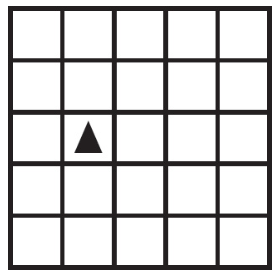
(C)
(D)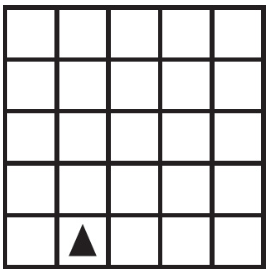
50. Using the program below, what are the possible locations the robot could visit?
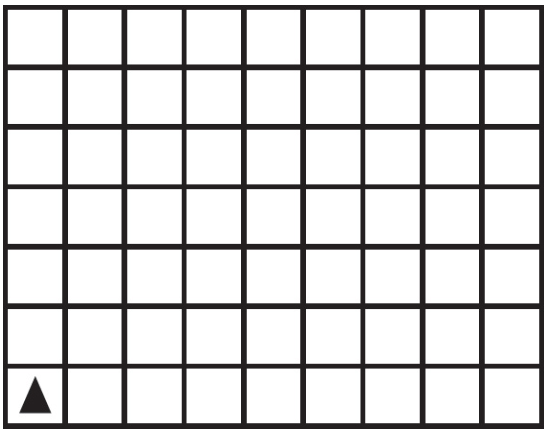
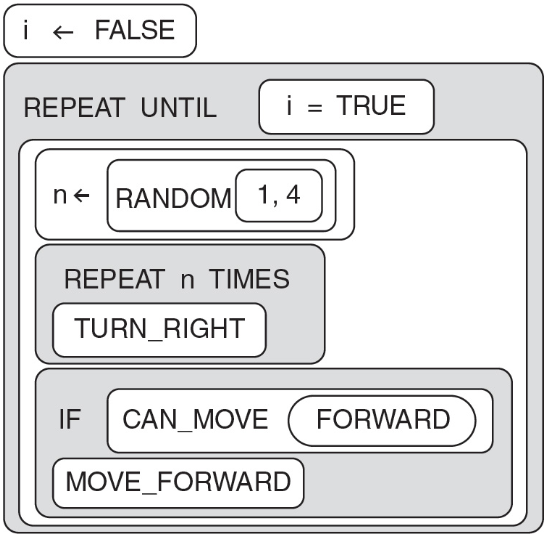
What are the possible landing spots for the robot?
(A)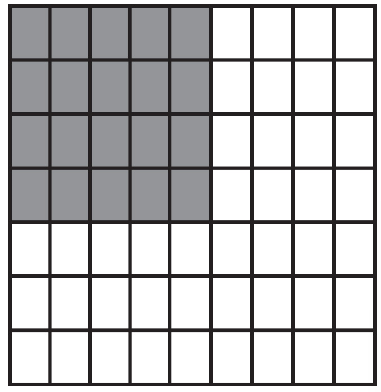
(B)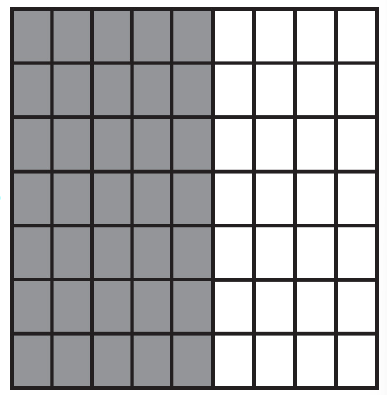
(C)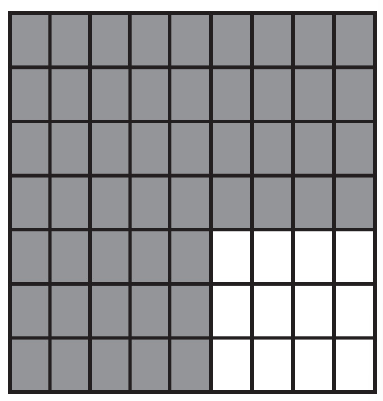
(D)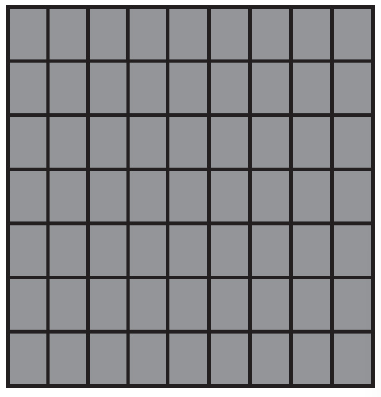
51. Using the program below, where will the robot land after the code segment executes?
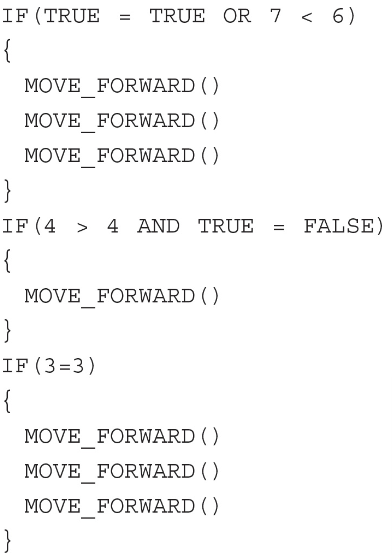
Starting Grid
(A)
(B)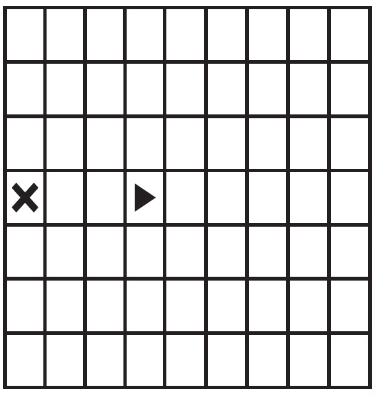
(C)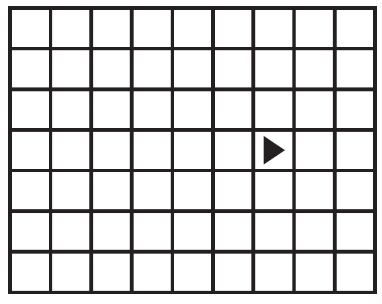
(D)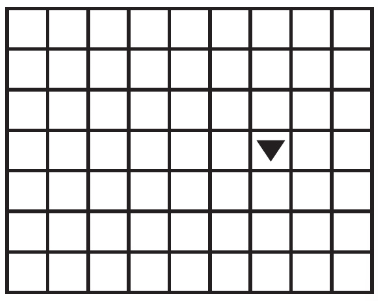
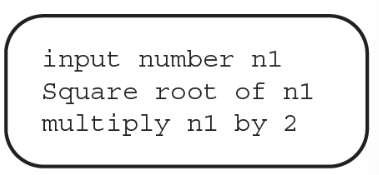
52. A programmer is creating an algorithm that doubles the square root of an inputted number and prints “small” if the result is less than 100. Which of the following would be an appropriate way to express it?
(A) input number n1
square root of n1
multiply n1 by 2
is n1 < 100?
yes -> print “small”
no -> do nothing
(B)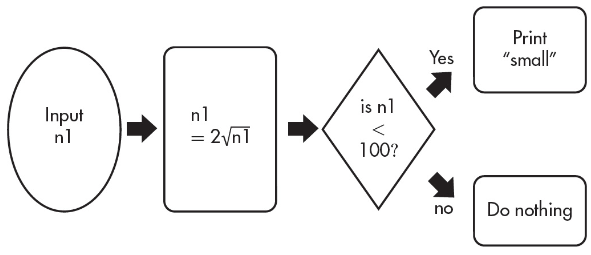
(C)
(D) All of the above
53. Which of the following MUST an algorithm be written in or be converted into to be executed by a computer?
(A) Natural language
(B) Pseudocode
(C) High-level language
(D) Low-level machine language
54. Suppose that a programmer has created an algorithm using a low-level assembly language. If the algorithm is translated exactly into a higher-level language such as Python, will the solution utilized still work? Why?
(A) Yes, because an exact translation of an algorithm affects only the way that it is read.
(B) Yes, because an algorithm will always work regardless of the language.
(C) No, because the readability of a language affects how complex algorithms can be.
(D) No, because an algorithmic solution can exist only in the language it is written in.
55. Why is it important that algorithms be executed in a reasonable time?
(A) An algorithm that does not execute in a reasonable time will break the computer it is running on.
(B) An algorithm that does not execute in a reasonable time will be rejected by the compiler.
(C) This ensures that the algorithm is capable of handling the data sets it will be given.
(D) This ensures that the algorithm is capable of finding an exact answer.
56. An algorithm has n number of steps. Which of the following would NOT be considered a reasonable number of steps?
(A) n
(B) 4n + 8n2
(C) 100n4
(D) 3n
57. Why might a programmer decide to make a portion of an algorithm heuristic?
(A) Heuristics are more accurate, so adding them makes for a stronger algorithm.
(B) Although heuristics are not as accurate compared to an algorithmic solution, they are much faster to run, which would make the ultimate algorithm more efficient.
(C) Heuristics are always easier to add into a program.
(D) Heuristics make an algorithm much harder to copy.
58. Which of the following would be considered a heuristic solution?
(A) A file-organizing algorithm determines the content of a file based on a certain number of bytes in the beginning of the file.
(B) A sorting algorithm passes every value, swapping two values where the first is lower. This repeats until there are no more swaps left.
(C) An antivirus program scans the entirety of every file on the hard drive.
(D) A searching algorithm determines the bit-level location of a text string in a document.
ALGORITHMS AND PROGRAMMING QUESTIONS PART 2
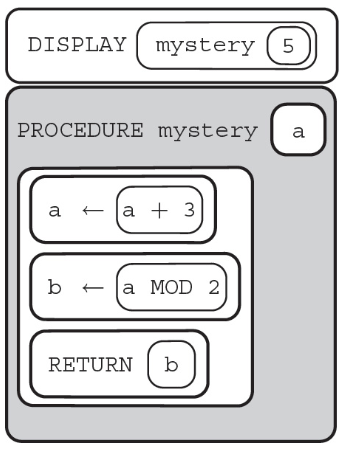
59.What will the following call to the procedure “mystery” display?
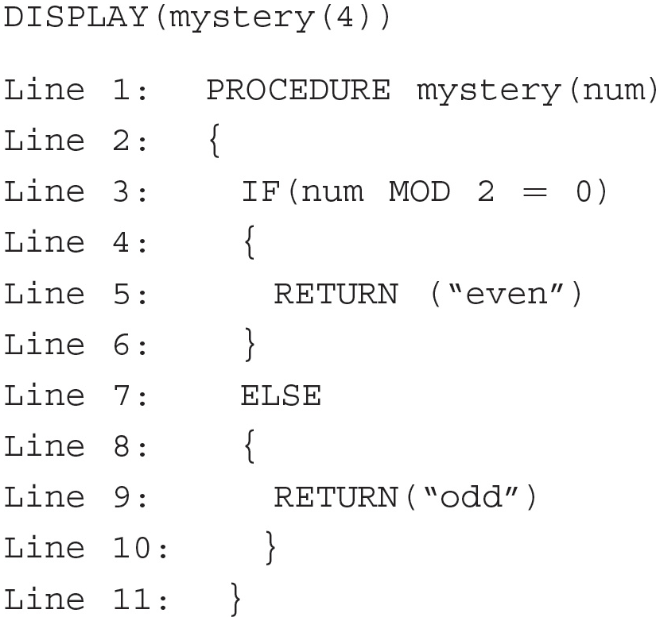
(A) even
(B) odd
(C) True
(D) False
60. What will the following call to the procedure “mystery” display?
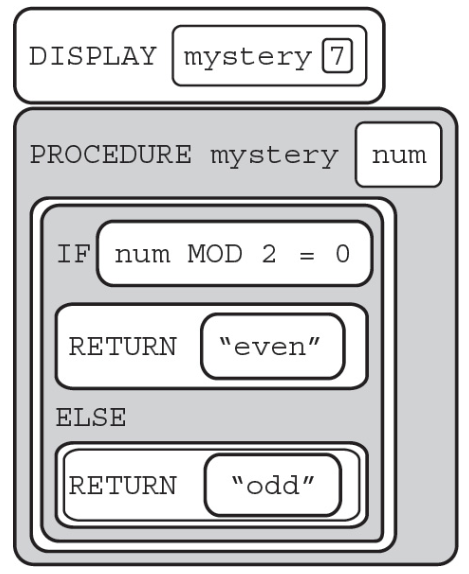
(A) even
(B) odd
(C) True
(D) False
61. What will the following call to the procedure “mystery” display?

(A) 0
(B) 1
(C) 2
(D) Nothing is returned due to an infinite loop.
62. What will the following call to the procedure “mystery” display?
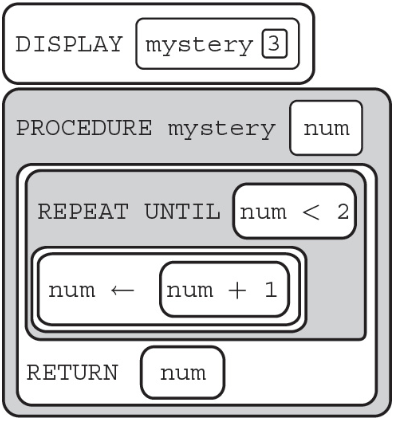
(A) 0
(B) 1
(C) 2
(D) Nothing is returned due to an infinite loop.
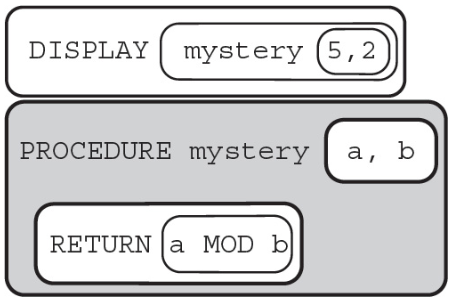
63. What will the following call to the procedure “mystery” display?

(A) 2 4
(B) 2 4 5
(C) 9
(D) 6
64. What will the following call to the procedure “mystery” display?
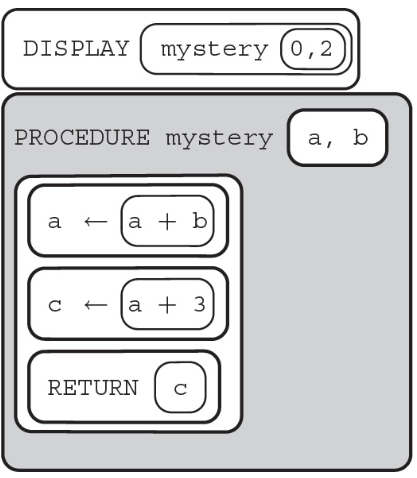
(A) 0 2
(B) 2 4 5
(C) 2
(D) 5
65. What will the following call to the procedure “mystery” display?

(A) 0 2
(B) 2 4 5
(C) 2
(D) 5
66. What will the following call to the procedure “mystery” display?
(A) 0
(B) 2 4 5
(C) 2
(D) 5
67. What will the following call to the procedure “mystery” display?

(A) 0
(B) 2 4 5
(C) 2
(D) 5
68. The following call to the procedure “mystery” is intended to display the number 2.
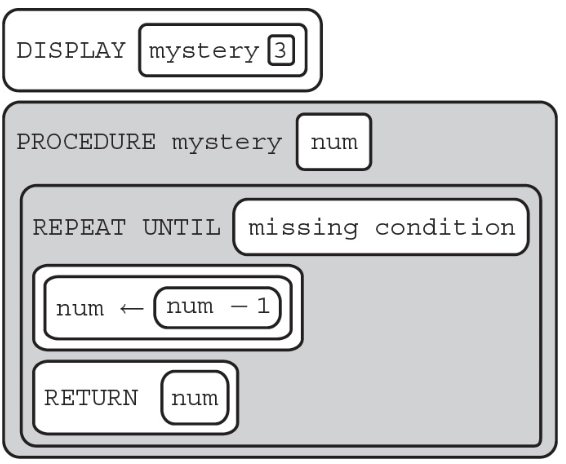
Which of the following can be used to replace so that the procedure will work as intended?
(A) (num < 2)
(B) (num > 2)
(C) (num < 3)
(D) (num > 3)
69. The following call to the procedure “mystery” is intended to display the number 6.

Which of the following can be used to replace so that the procedure will work as intended?
(A) (num < 3)
(B) (num > 3)
(C) (num < 6)
(D) (num > 5)
70. What will the following call to the procedure “mystery” display?
(A) 0
(B) 1
(C) 2
(D) 3
71. What will the following call to the procedure “mystery” display?

(A) 0
(B) 1
(C) 2
(D) 3
72. What will the following program display?
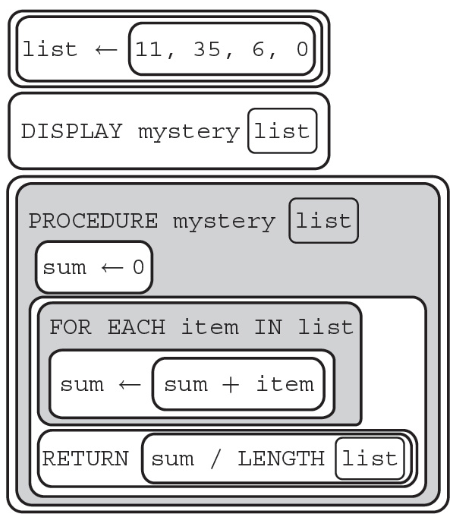
(A) 0
(B) 4
(C) 13
(D) 35
73. What will the following program display?
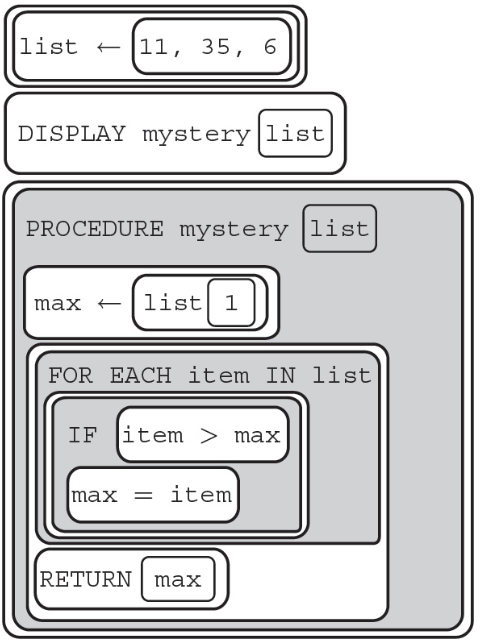
(A) 0
(B) 12
(C) 16
(D) 35
74. What does list2 contain after the program is run?
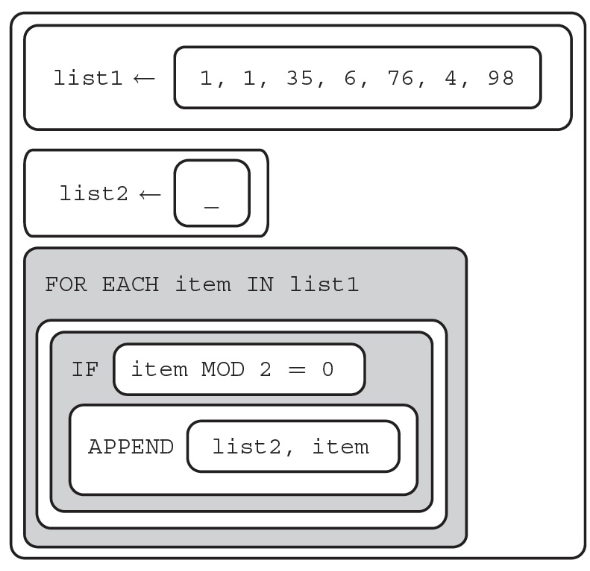
(A) [ 6, 76, 4, 98]
(B) [1, 1, 35]
(C) [1, 1, 35, 6, 76, 4, 98]
(D) [ ]
75. What will the following program display?
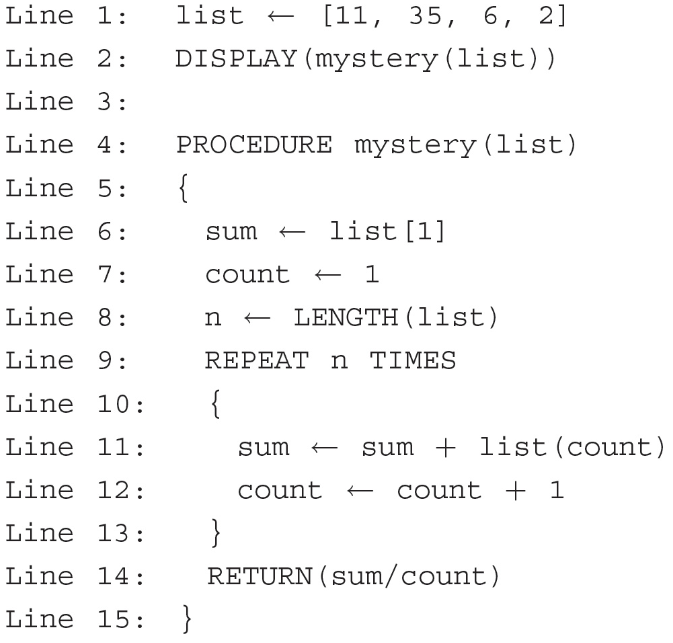
(A) 0
(B) 13
(C) 16
(D) 35
76. What will list2 contain after this program segment is run?
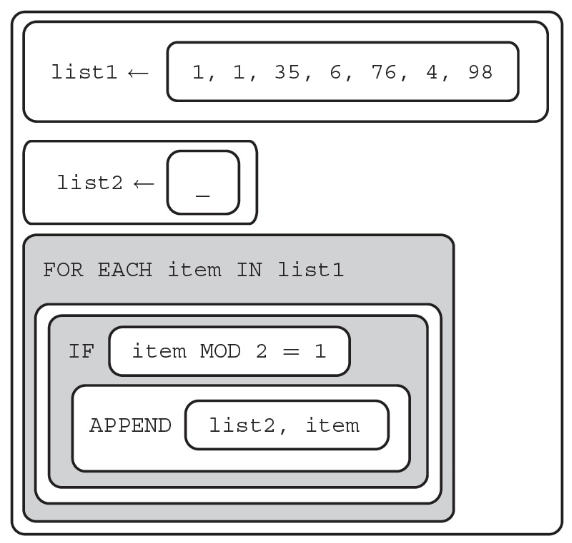
(A) [6, 76, 4, 98]
(B) [1, 1, 35]
(C) [1, 1, 35, 6, 76, 4, 98]
(D) [ ]
77. What will list2 contain after this program segment is run?
(A) [0]
(B) [−11]
(C) [−35]
(D) [ ]
78. What will list2 contain after this program segment is run?
(A) [6, 76, 4, 98]
(B) [1, 1, 35]
(C) [1, 1, 35, 6, 76, 4, 98]
(D) [ ]
79. What will the following program display?
(A) 0
(B) 1
(C) 76
(D) 98
80. What will the following program display?
(A) 98
(B) 1
(C) 0
(D) −98
81. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the top-left square of the grid and facing toward the top of the grid.
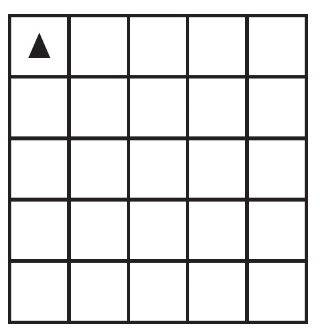
Code for the procedure “mystery” is shown here. Assume that the parameter p has been assigned a positive integer value (e.g., 1, 2, 3, . . .).
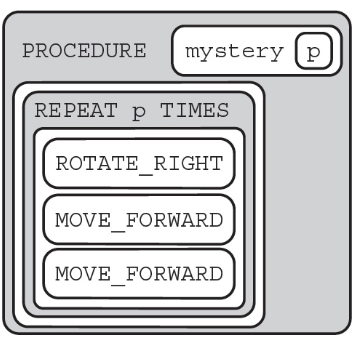
Which of the following shows a possible result of calling the procedure?
(A)
(B)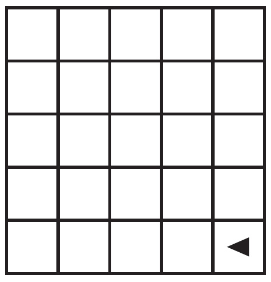
(C)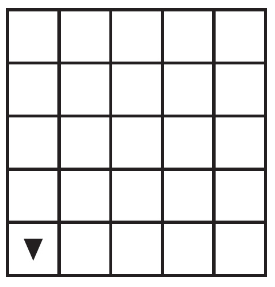
(D)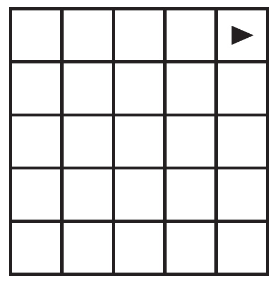
82. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the top-left square of the grid and facing toward the top of the grid.
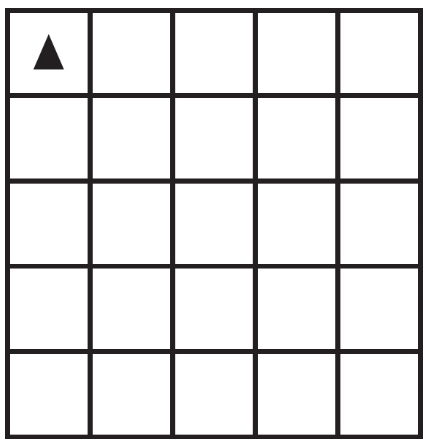
Code for the procedure “mystery” is shown below. Assume that the parameter p has been assigned a positive integer value (e.g., 1, 2, 3, . . .).
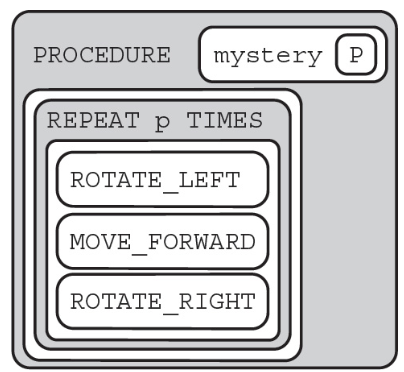
Which of the following shows the result of calling the procedure when p = 4?
(A)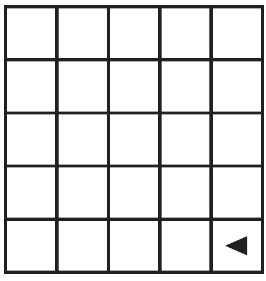
(B)
(C)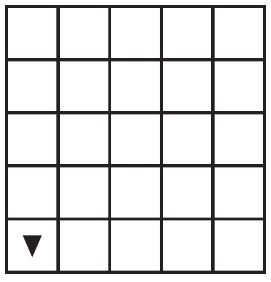
(D) Error. The robot will be out of the grid.
83. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the top-left square of the grid and facing toward the top of the grid.
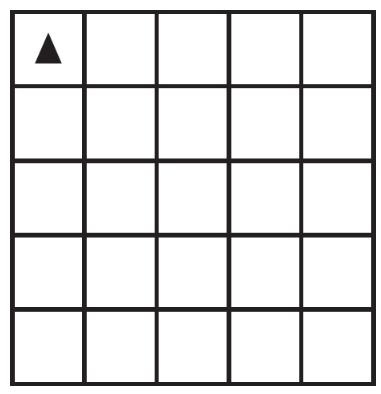
Code for the procedure “mystery” is shown below. Assume that the parameter p has been assigned a positive integer value (e.g., 1, 2, 3, . . .).
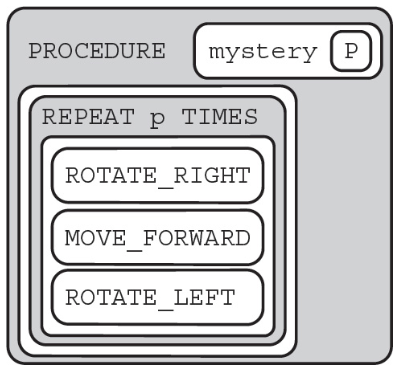
Which of the following shows the result of calling the procedure when p = 4?
(A)
(B)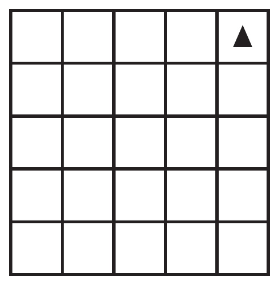
(C)
(D)
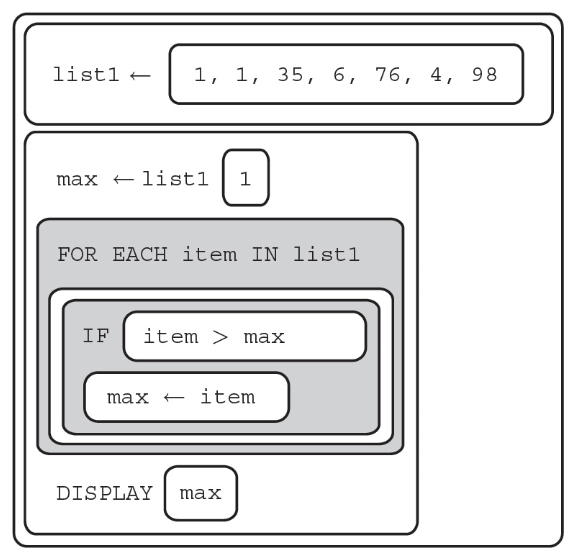
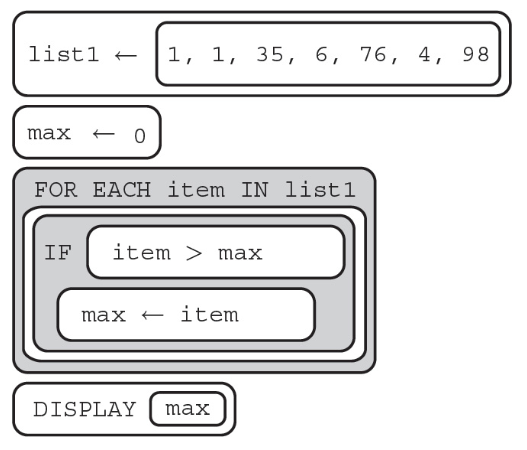
84. The program below is intended to find the highest non-negative number in a list.
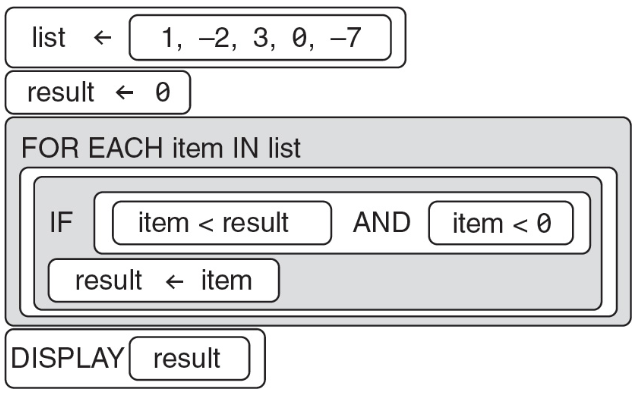
Does the program work as intended?
(A) Yes, the program works as intended; it displays 1.
(B) No, the program does not work as intended; the result starts at 0.
(C) Yes, the program works as intended; it displays 3.
(D) No, the program does not work as intended; the “IF” conditional should be “item > result AND item < 0.”
85. The following program is intended to find the lowest number in a list.
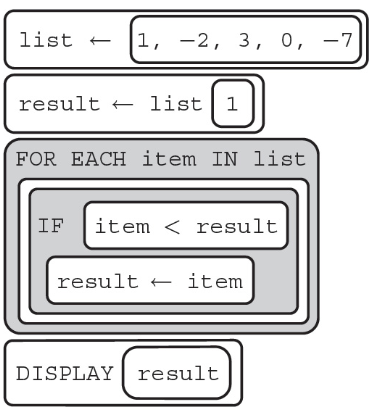
Does the program work as intended?
(A) Yes, the program works as intended; it displays −7.
(B) No, the program does not work as intended; the result is always list[1].
(C) Yes, the program works as intended; it displays 1.
(D) No, the program does not work as intended; it produces a runtime error.
86. The following program is intended to find the lowest number in a list.
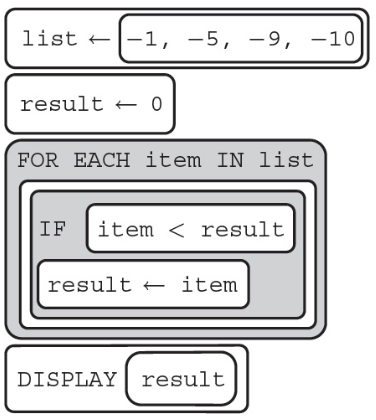
Does the program work as intended?
(A) Yes, the program works as intended and returns −10.
(B) No, the program does not work as intended; although this code runs, it returns a logical error of the value 0.
(C) Yes, the program works as intended and returns the value −1.
(D) No, the program does not work as intended and results in a runtime error not returning a number.
87. The following program is intended to find the greatest number in a list.
Does the program work as intended?
(A) Yes, the program works as intended, returning −200.
(B) No, the program does not work as intended; the result never changes and instead returns −3.
(C) Yes, the program works as intended and returns −1.
(D) No, the program does not work as intended; it produces a runtime error.
88. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the top-left square of the grid and facing toward the top of the grid.
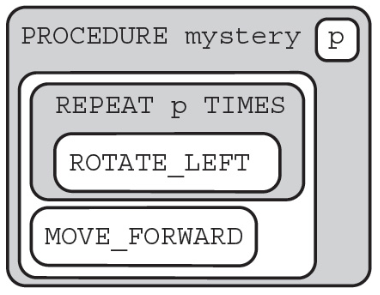
Code for the procedure “mystery” is shown below. Assume that the parameter p has been assigned a positive integer value (e.g., 1, 2, 3, . . .).
Which of the following shows the result of calling the procedure when mystery(6)?
(A)
(B)
(C)
(D)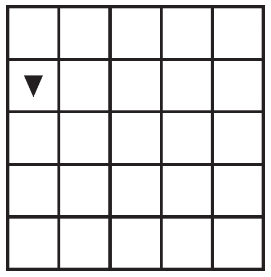
89. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the top-left square of the grid and facing toward the top of the grid.
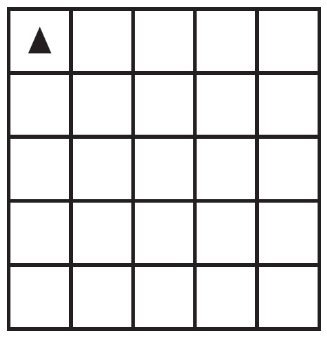
Code for the procedure “mystery” is shown below. Assume that the parameter p has been assigned a positive integer value (e.g., 1, 2, 3, . . .).
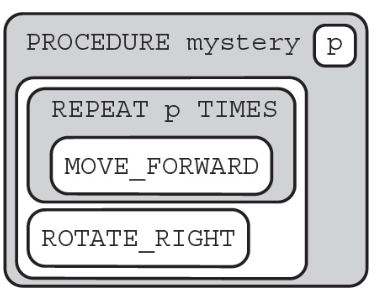
Which of the following shows the result of calling the procedure when calling mystery(6)?
(A)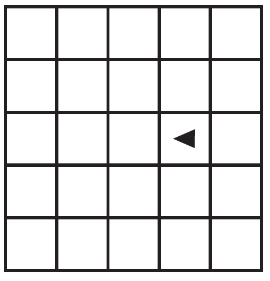
(B)
(C)
(D) Error. The robot will stay in its current location and the program will terminate.
90. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the bottom-left square of the grid and facing toward the top of the grid.
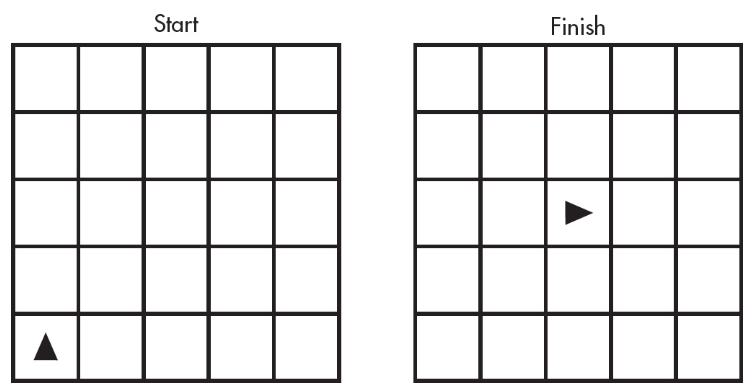
Which of the following code segments produces the result above?
(A)
(B)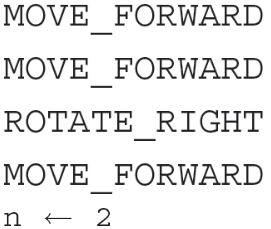
(C)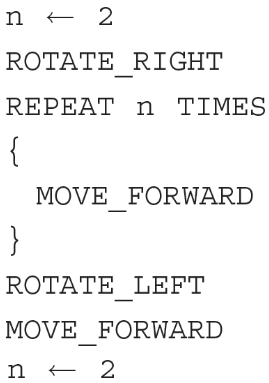
(D)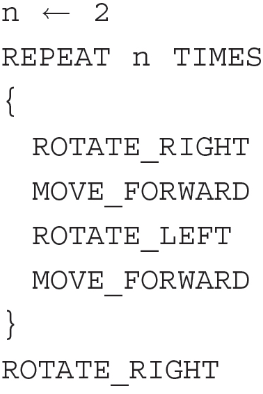
91. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the top-left square of the grid and facing toward the top of the grid.
Code for the procedure “mystery” is shown below. Assume that the parameter p has been assigned a positive integer value (e.g., 1, 2, 3, . . . ).
Which of the following could be the result of calling the procedure for any positive value of p?
Select two answers.
(A)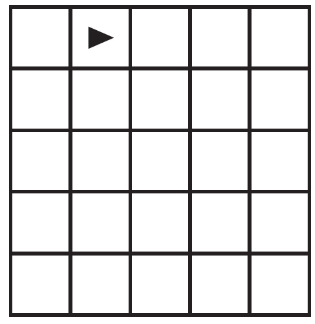
(B)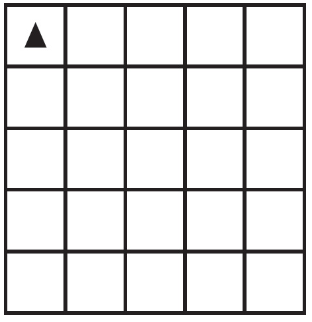
(C)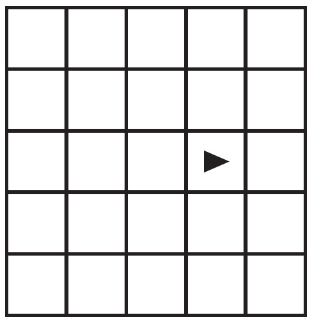
(D)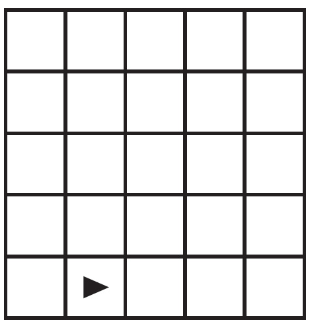
92. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the top-left square of the grid and facing toward the top of the grid.
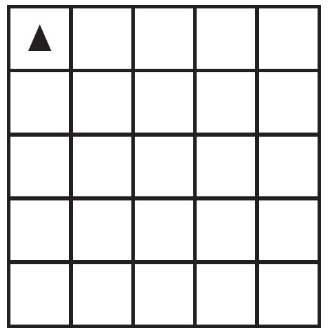
Code for the procedure “mystery” is shown below. Assume that the parameter p has been assigned a positive integer value of either 0 or 1.
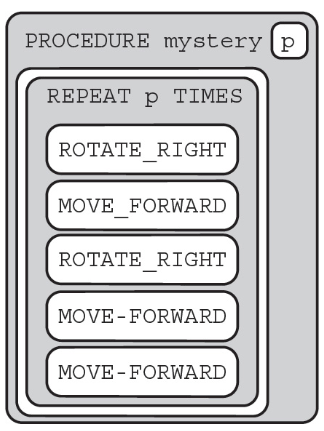
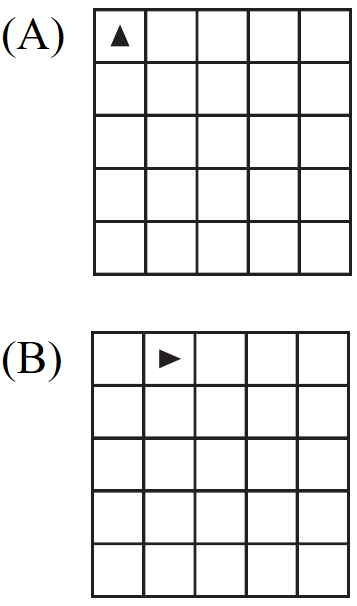
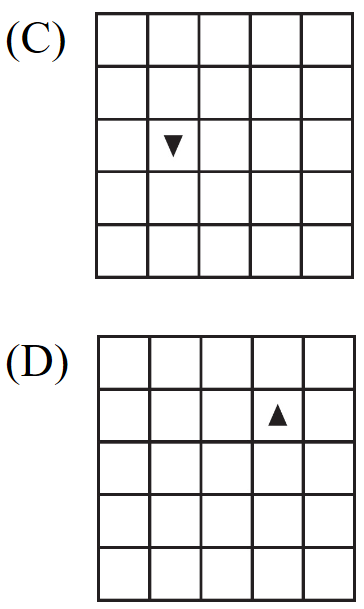
Which of the following shows the result of calling the procedure for the value of p equal to 0 or 1?
Select two answers.
93. The following program is intended to find the average of a class’s scores.
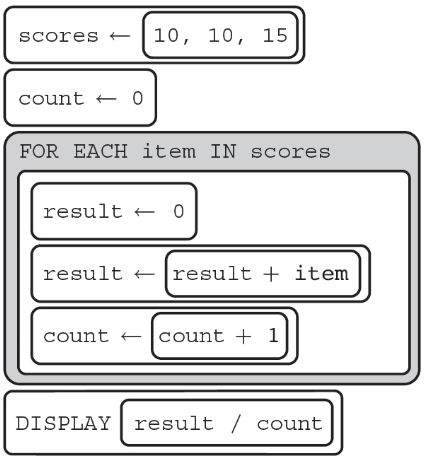
What does the code segment display?
(A) 0
(B) 5
(C) 20
(D) Nothing, runtime error
94. The following code segment is intended to find the maximum.
Which of the following code segments can replace missing code to make the procedure work as intended?
(A) max > item
(B) max = item
(C) item > max
(D) max >= item
95. What does the following code segment return?
(A) The number of even items in list
(B) The number of items in list
(C) The number of odd items in list
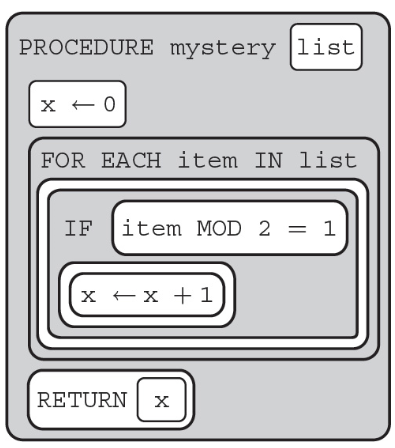
(D) Nothing, the code causes a runtime error
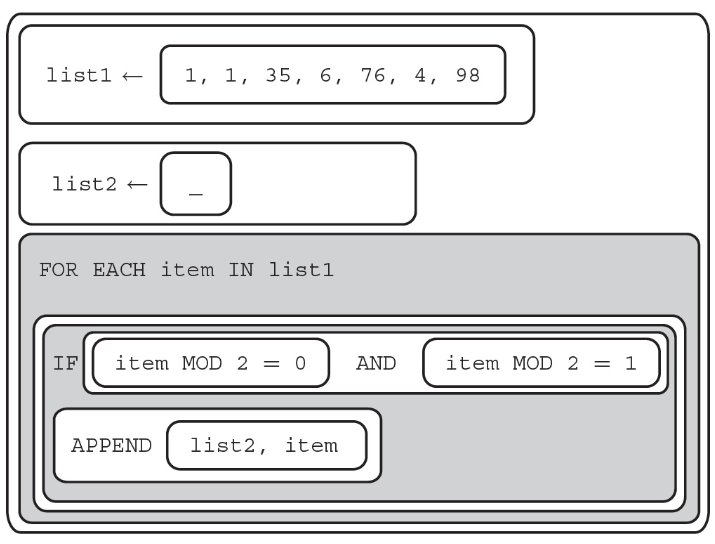
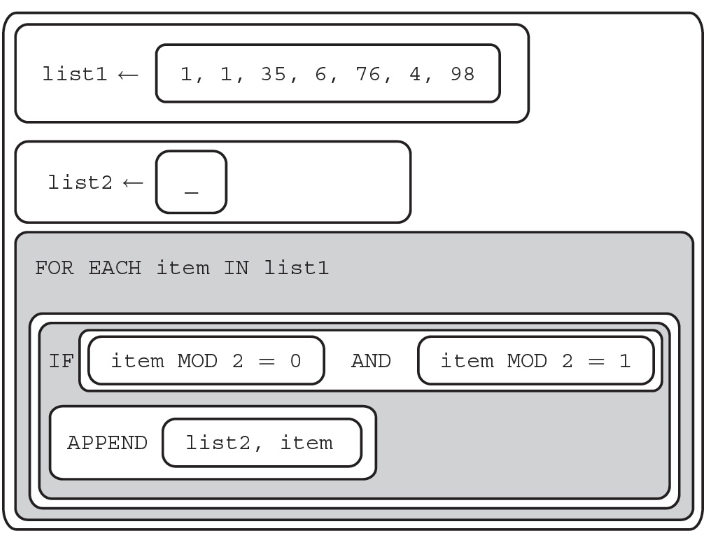
96. The following procedure is intended to find the amount of numbers in a list that are divisible by 5 and 2.
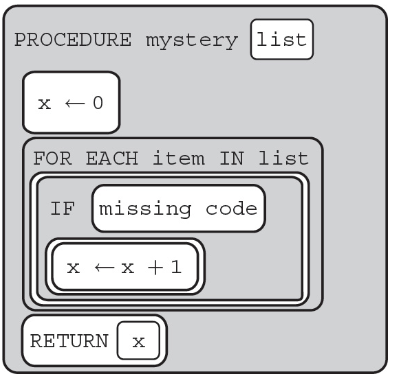
Which of the following code segments can replace missing code to make the procedure work as intended?
(A) item MOD 5 = 0 OR item MOD 2 = 1
(B) item MOD 2 = 1 AND item MOD 5 = 1
(C) item MOD 5 = 0 AND item MOD 2 = 1
(D) item MOD 2 = 0 AND item MOD 5 = 0
97. The following code segment is intended to switch the values of x and y (assume x and y have already been initialized).
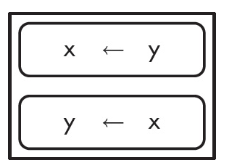
What can be done to make the code segment work as intended?
(A) Add “temp ← x” above “x ← y” and replace “y ← x” with “y ← temp.”
(B) Nothing, the code works as intended
(C) Add “temp ← x” below “x ← y”
(D) Add “temp ← y” above “x ← y”
98. What is the purpose of the following procedure?
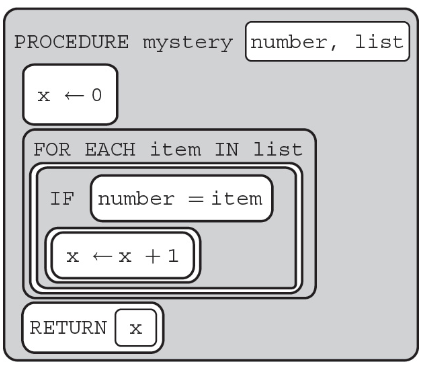
(A) To find the amount of items in list
(B) To find the amount of items in list that are equal to number
(C) To find the amount of items in list that do not equal number
(D) Nothing, syntax error
99. What is returned by the following procedure?
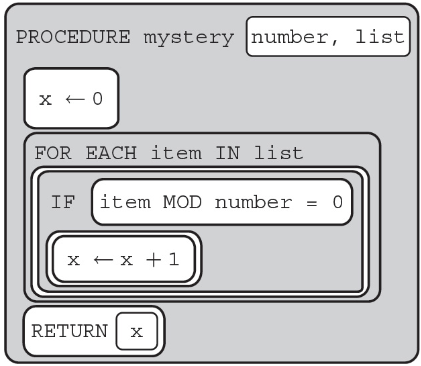
(A) Nothing, syntax error
(B) To find the number of items in list that equal number
(C) To find the amount of items in list that are divisible by number
(D) Nothing, runtime error
100. The following procedure is intended to find the amount of values divisible by 15 in list.
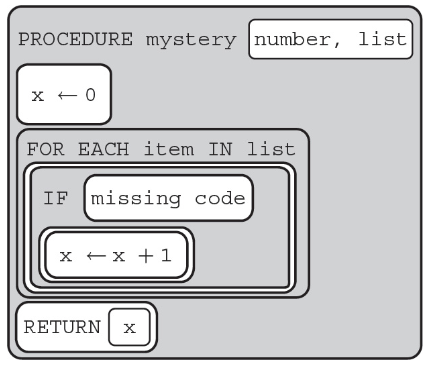
What can replace missing code to make the function work as intended?
(A) item MOD 15 = 0
(B) item/15 = 1
(C) item MOD 15 = 1
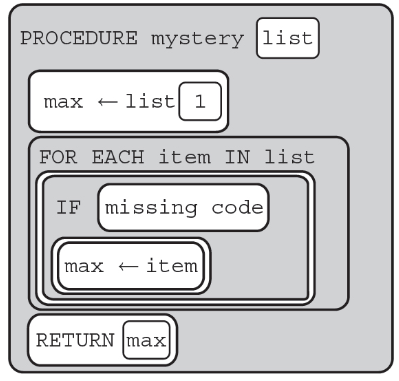
(D) item/15 = 0
101. What will the following code segment display?
x ← 10
arr ← [“I”, “Love”, “Puppies”]
DISPLAY(arr[(x − LENGTH(arr)) MOD 4])
(A) I
(B) Love
(C) Puppies
(D) ArrayOutOfBoundsException
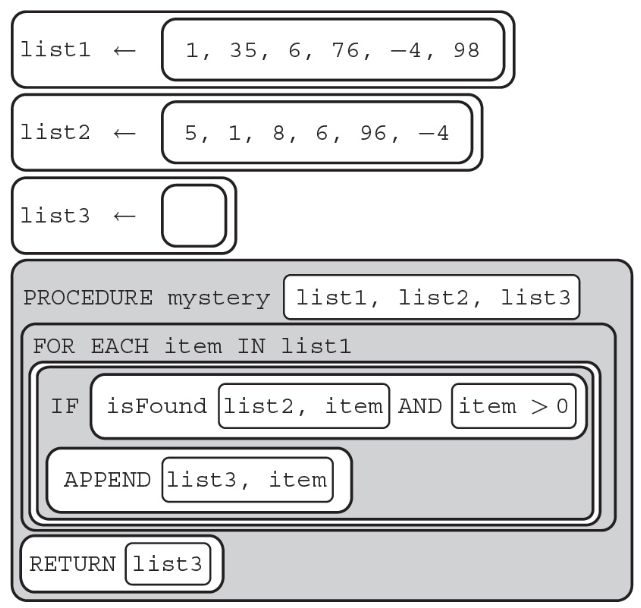
102. The method isFound(list, item) returns true if the item is in the list. What does list3 contain after the procedure is run below?
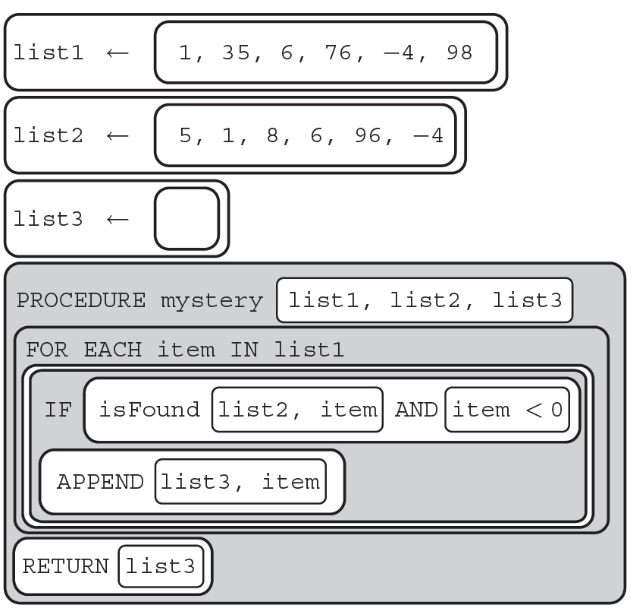
(A) [−4, −98]
(B) [1, 6, −4]
(C) [−4]
(D) [1, 35, 6, 76, 4, 98, 5, 1, 8, 96, −4]
103. The method isFound(list, item) returns true if the item is in the list. What does list3 contain after the program is run below?
(A) [−4, −98]
(B) [1, 6, −4]
(C) [−4]
(D) [1, 6]
104. In the following program, which chart displays the ways in which the variables are changed?
x ← 5
y ← 10
z ← 15
z ← x − y
x ← z − 15
y ← y + x
x ← x + y + z
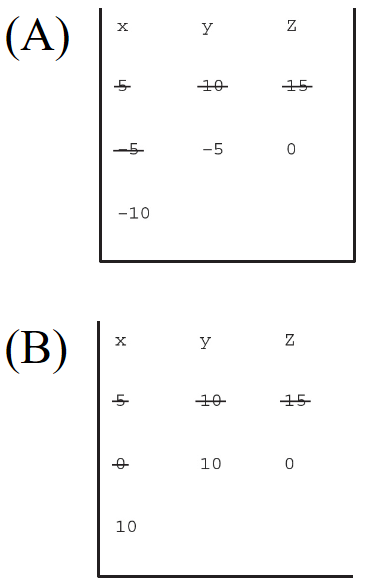
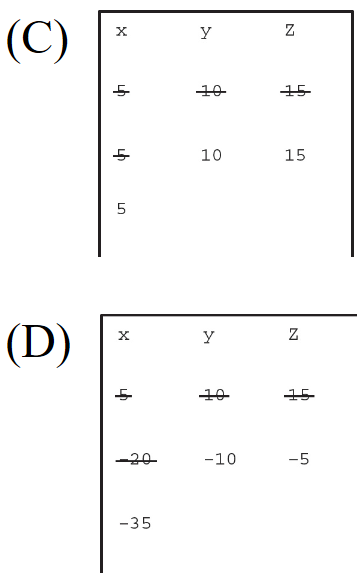
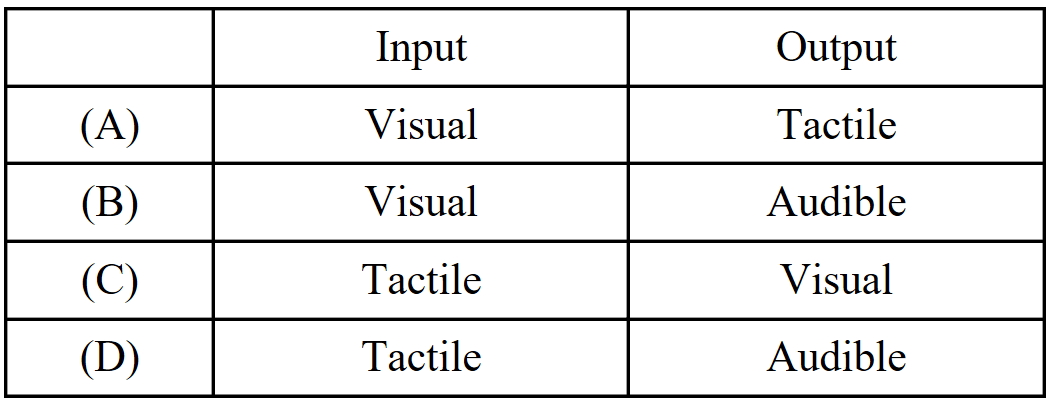
105. A programmer is curious about the accuracy of a new touchpad. To test it, he creates a program that graphically displays the location of the detected pressure and technical information about the device’s current state. What types of input and output are used by this program?
106. Which of the following statements correctly describes a procedure?
I. A procedure can be used in any program as long as the original procedure can be located.
II. A procedure is able to work in any program without translation, regardless of the language in which the program is coded.
III. A procedure can be reused throughout a program.
(A) I only
(B) I and II only
(C) I and III only
(D) II and III only
107. Why is it generally considered a better idea to use procedures in a program?
Select two answers.
(A) Procedures make a program easier to read because they can collapse complex algorithms into a single procedure call.
(B) Procedures make a program easier to share because procedures used in the program will always be in the same file.
(C) Procedures are easier to read because they ensure that the code is working correctly.
(D) Procedures make a program easier to modify because editing a repeated algorithm in a procedure requires editing only the procedure.
108. What is the benefit of using a programming library?
(A) Programming libraries include procedures for common functions, such as exponents, which save programmers from having to make such procedures themselves.
(B) Programming libraries make it easy to translate code from one programming language to another.
(C) Programming libraries allow people to derive code from a compiled program because these libraries correspond between compiled code and high-level code.
(D) Programming libraries slow the execution time of programs.
109. The following question uses a robot in a grid. The robot is presented as a triangle, which is initially in the lower-left square of the grid and facing toward the top of the grid.
Which of the following programs will place the robot in the ending grid location?
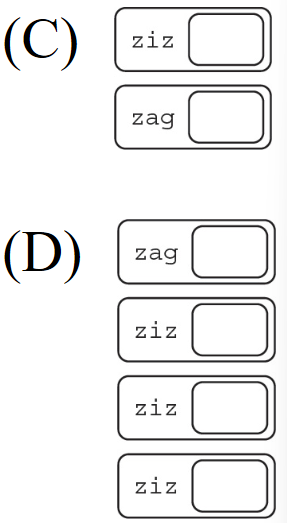
110. The following question uses a robot in a grid. The robot is presented as a triangle, which is initially in the lower row of the grid and facing up. Which of the following calls to moveAndTurn will result in the robot’s landing on the star?
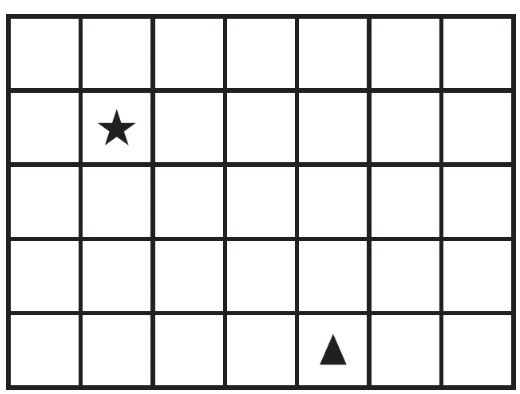
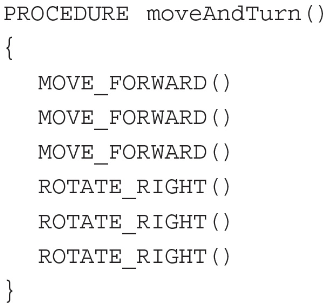
(A) moveAndTurn()
(B) moveAndTurn()
moveAndTurn()
(C) moveAndTurn()
moveAndTurn()
moveAndTurn()
(D) moveAndTurn()
moveAndTurn()
moveAndTurn()
moveAndTurn()
111. The following question uses a robot in a grid. The robot is presented as a triangle, which is initially in the lower-left row of the grid and is facing up. Which of the following calls to moveAndSpin will result in the robot’s landing on the star?

Select two answers.
(A) moveAndSpin(4, 1)
moveAndSpin(6, 0)
(B) moveAndSpin(0, 1)
moveAndSpin(6, 3)
moveAndSpin(4, 0)
(C) moveAndSpin(7, 3)
(D) moveAndSpin(0, 7)
112. A procedure is shown.
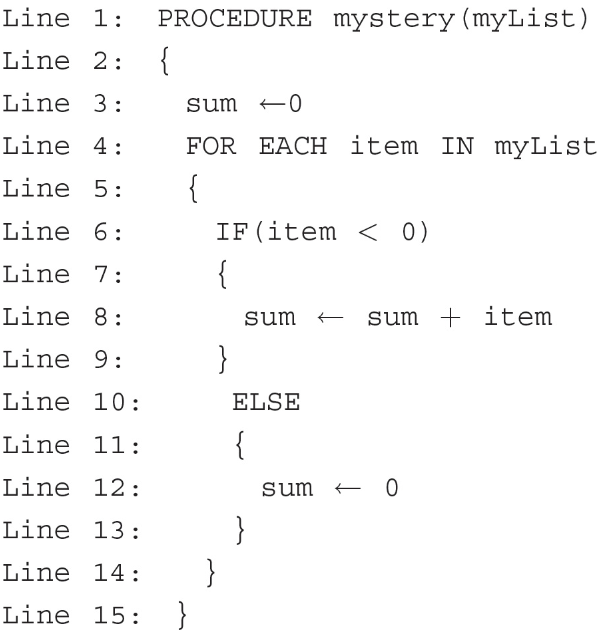
Which of the following values for myList will cause the procedure mystery to assign the value of sum to the total value of all the elements in myList added together?
(A) [3, 5, 23, 88]
(B) [−3, −5]
(C) [−3, 5, −8]
(D) [−4, 0]
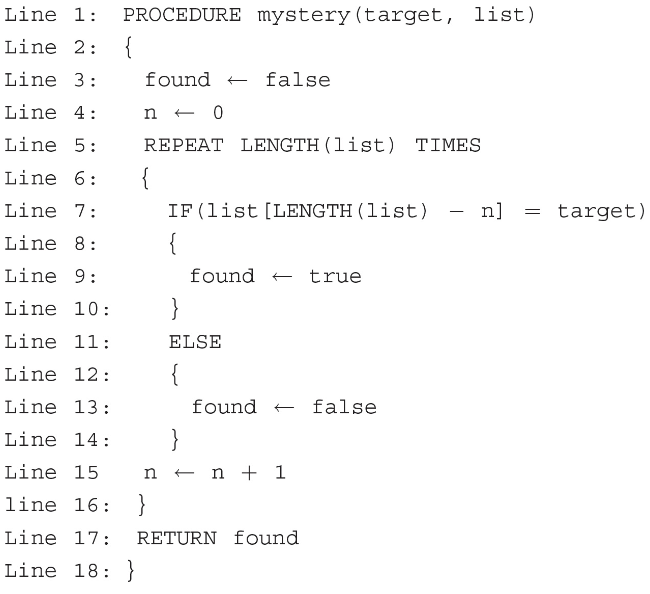
113. The following procedure is intended to return true if the string contained in target is in the data structure list.
.png)
Which of the following method calls will NOT return true?
(A) mystery(“pig”, [“cat”, “pig”])
(B) mystery(“pig”, [“cat”, “pig”, “snake”])
(C) mystery(“pig”, [“cat”, “pig”, “pig”])
(D) mystery(“Cookie”, [pig”, “elephant”, “Cookie”])
114. The following procedure is intended to return true if the string contained in the target is in the data structure list.
Which of the following test cases will return the value true?
(A) mystery(“pig”, [“cat”, “pig”])
(B) mystery(“pig”, [“cat”, “pig”, “snake”])
(C) mystery(“pig”, [“cat”, “pig”, “pig”])
(D) mystery(“pig”, [“pig”, “elephant”, “Cookie”]
115. In the procedure “mystery” below, the parameter number is a positive integer.
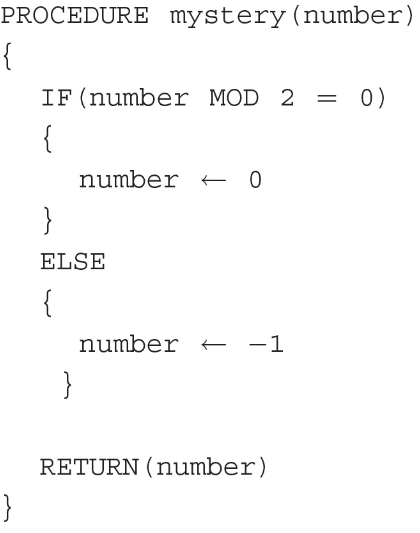
Which of the following best describes the result of running the procedure “mystery”?
(A) The procedure will return 0 if the number is even and −1 if the number is odd.
(B) The procedure will return −1 if the number is greater than 3 and 0 if the number is less than 3.
(C) The procedure will return −1 for all numbers that are greater than 0.
(D) This program will not return a number as it is in an infinite loop.
116. What will the procedure “mystery” below return when the parameters (A, B) are Boolean values?
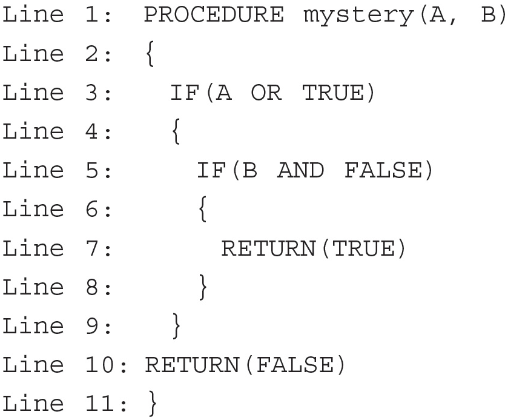
(A) The output will be TRUE no matter the value of A or B.
(B) The output will be FALSE no matter the value of A or B.
(C) The output will be TRUE if input A is TRUE; otherwise it will be FALSE.
(D) The output will be TRUE if input B is TRUE; otherwise it will be FALSE.
117. What will the procedure “mystery” below return when the parameters (A, B) are Boolean values?
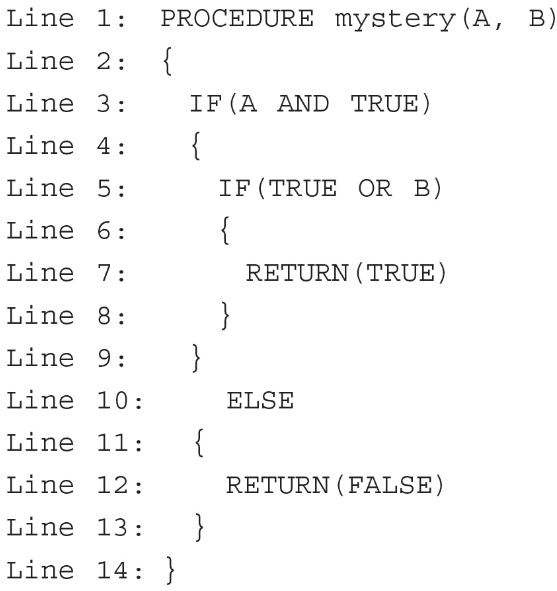
(A) The output will be TRUE no matter the value of A or B.
(B) The output will be FALSE no matter the value of A or B.
(C) The output will be TRUE if input A is TRUE; otherwise it will be FALSE.
(D) The output will be TRUE if input B is TRUE; otherwise it will be FALSE.
COMPUTER SYSTEMS AND NETWORKS QUESTIONS
1. Which of the following is true about packets?
(A) Packets will travel along the fastest path from the sending to receiving computer.
(B) Packets can arrive at the receiving computer in a different order than sent by the sending computer.
(C) When sent by a sending computer packets are guaranteed to arrive at the receiving computer.
(D) One sending file will contain one packet.
2. Which characteristics of internet protocols have helped fuel the rapid growth of the internet? Select two answers.
(A) Internet standards cannot be altered, so different companies can focus on development.
(B) Internet protocols are open (nonproprietary).
(C) Internet protocols are designed to be useful for a growing population of users.
(D) The design of internet protocols involves large profits that motivate companies to innovate internally with no outside feedback.
3. Which of the following internet protocols defines how computers send packets of data to each other? Select two answers.
(A) HTTP
(B) TCP
(C) IP
(D) UDP
4. Which of the following protocols is responsible for addressing and routing your online requests?
(A) HTTP
(B) TCP
(C) IP
(D) UDP
5. When is it advantageous to use UDP instead of TCP?
(A) UDP should be used when the IP address of the receiving computer is not known.
(B) UDP should always be used when available since UDP is faster and more reliable than TCP.
(C) UDP should be used when a guarantee is required that the order of data at the sending computer matches the order of data arriving at the receiving computer.
(D) UDP should be used when the speed of data transfer is more important than error correction.
6. Many types of computing devices made by many types of companies can all access the internet. Which of the following makes this access possible?
(A) Redundancy
(B) Open standards and protocols
(C) Fault tolerance
(D) Large bandwidth
7. Why are most websites designed to work within the boundaries of current web protocols, even when that limits the website’s capabilities?
(A) Since the protocols are supported by all current web browsers, potential incompatibilities are minimized.
(B) It is illegal to go beyond the boundaries of current protocols.
(C) Current protocols are the limit of web technology, so going further is impossible.
(D) If a protocol is exceeded, an ISP will assume the website to be broken or malicious and block it.
8. What is the purpose of transitioning from IPv4 to IPv6?
(A) IPv4 has been found to be too insecure for modern communication.
(B) The rise of internet-connected devices means that the number of available unique IPv4 addresses is sharply decreasing, and IPv6 will allow for more addresses.
(C) IPv4 is too slow to be useful in modern communications.
(D) It is easier to spoof an IPv4 address, as compared to an IPv6 address.
9. How does redundancy improve the scaling of the internet?
(A) Redundancy leads to every communication being repeated, which keeps the data from being lost.
(B) Redundancy leads to every communication being repeated, which ensures that the connected devices do not disconnect from each other.
(C) Redundancy makes connections more reliable, which means that more devices are able to communicate without interruption.
(D) Redundancy makes connections more reliable, which ensures that computers are always on the internet.
10. How many lines need to be cut to isolate A completely?
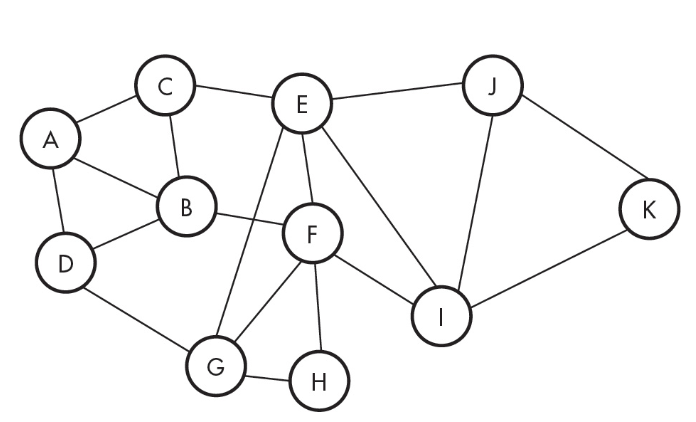
(A) 1 line
(B) 3 lines
(C) 4 lines
(D) 5 lines
11. How many lines need to be cut to isolate F completely?
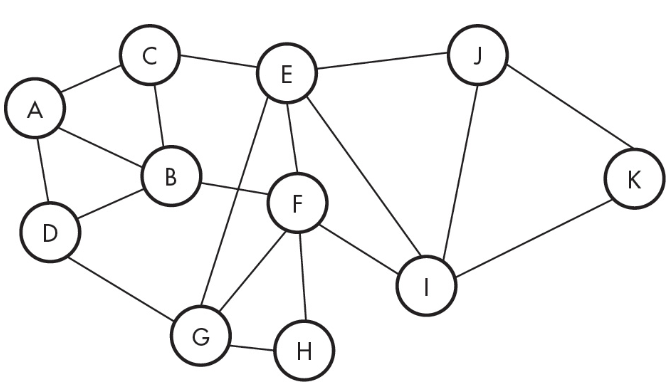
(A) 1 line
(B) 3 lines
(C) 4 lines
(D) 5 lines
12. How many lines need to be cut to isolate A completely?
(A) 1 line
(B) 3 lines
(C) 4 lines
(D) 5 lines
13. What is the minimum number of computers a packet must go through when traveling from computer B to computer D?
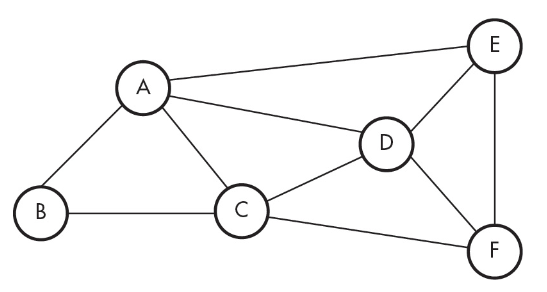
(A) 0
(B) 1
(C) 2
(D) 3
14. If the line between computers B and C has failed, which computer must a message go through if a message is sent between computers B and C?
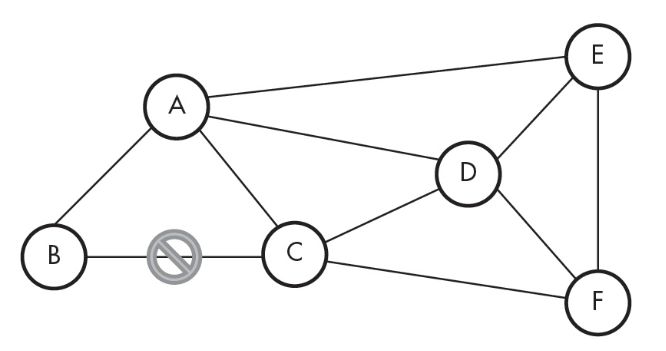
(A) A
(B) D
(C) E
(D) F
15. The internet is built on open standards. In this context, what does “open” mean?
(A) The standards are made freely available and can be used by anyone.
(B) The standards cannot be used in proprietary software of any form.
(C) The standards can be used in any program that is used exclusively to access the web.
(D) The official standards can be made, updated, and edited by anyone.
16. Which of the following best describes the fault-tolerant nature of the internet?
(A) The internet always picks the fastest routes for packets traveling between a sending and receiving computer.
(B) If a node on the internet fails, the packets choose a different path to the receiving computer.
(C) This fault-tolerant nature adds an additional layer of privacy for data traveling across the internet
(D) All of the above.
17. Which of the following statements about packets are true? Select two answers.
(A) Packets must be received in the order they are sent to be reassembled.
(B) Packets do not have to be received in the order they are sent to be reassembled.
(C) Packets can travel different paths from the sending computer to the receiving computer.
(D) Packets always choose the fastest path available from sending computer to receiving computer.
18. Which of the following is true about redundancy on the internet?
I. Redundancy slows down packets traveling from a sending computer to a receiving computer.
II. Redundancy allows for adding new devices to the network without disrupting traffic.
III. Redundancy makes the internet fault tolerant.
(A) I only
(B) I and II only
(C) II and III only
(D) I, II, and III
19. Which of the following describes a benefit of internet standards?
I. Internet standards are procedures to ensure that software and hardware created by different companies can communicate with each other online.
II. Internet standards are written to ensure that internet protocols are open and free to use.
III. Internet standards reduce the risk of malicious software affecting users of the internet.
(A) I only
(B) I and II only
(C) II and III only
(D) I, II, and III
20. Which of the following is contained in a packet?
(A) The sender’s IP address
(B) The receiver’s IP address
(C) Data
(D) All of the above
21. A certain computer has a single central processing unit. The following table indicates the amount of time three processes each take to execute on a single processor. Assume none of the processes are dependent on any other process.
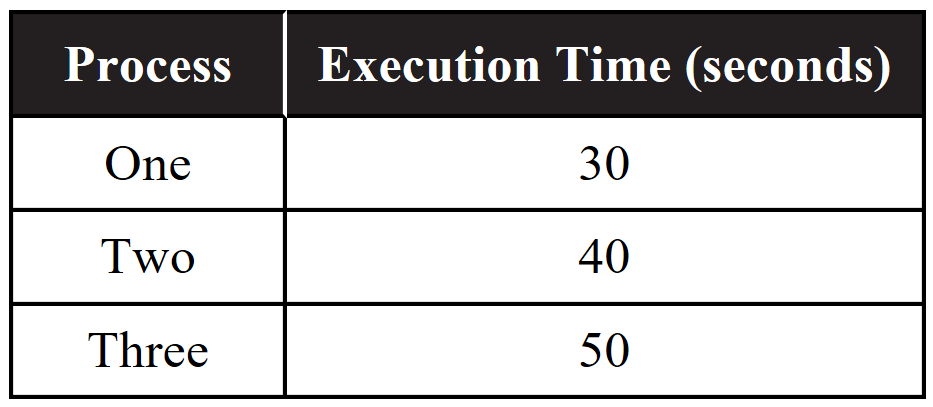
Which of the following best approximates the minimum possible time to run all three processes in series?
(A) 30 seconds
(B) 70 seconds
(C) 80 seconds
(D) 120 seconds
22. A certain computer has two identical processors that can run in parallel. Each processor can run only one process at a time, and each process must be executed on a single processor. The following table indicates the amount of time three processes each take to execute on a single processor. Assume none of the processes are dependent on any other process.
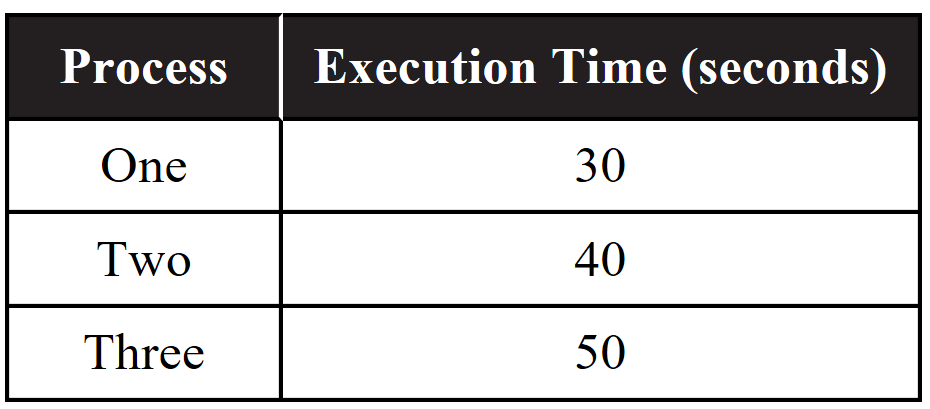
Which of the following best approximates the minimum possible time to run all three processes in parallel?
(A) 30 seconds
(B) 70 seconds
(C) 80 seconds
(D) 120 seconds
23. A certain computer has two identical processors that can run in parallel. Each processor can run only one process at a time, and each process must be executed on a single processor. Processes one and two must be run in series, while process three, four and five can all run in parallel. The following table indicates the amount of time needed to execute all five processes on a single processor.
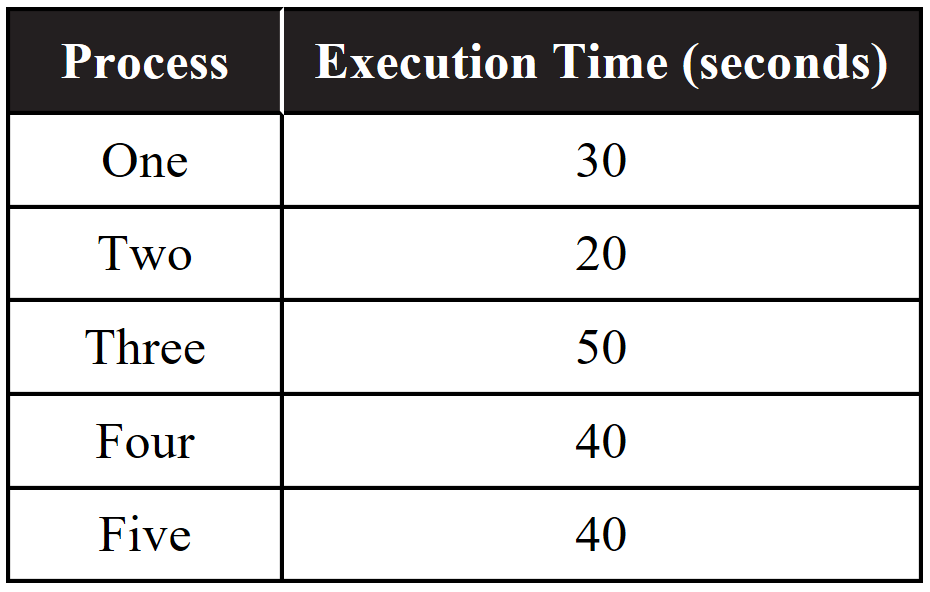
Which of the following best approximates the minimum possible time to run all five processes in parallel?
(A) 50 seconds
(B) 90 seconds
(C) 130 seconds
(D) 180 seconds
24. Which of the following algorithms is the best candidate to decrease run time by using parallel computing?
(A) An algorithm that cannot be broken down into independent operations
(B) An algorithm that can be broken down into independent operations
(C) An algorithm that is run on a single-processor machine
(D) An algorithm that has only one operation
25. When run in series, a program that checks pictures for ears takes 1,000 seconds to check 100 pictures. When running the same program in parallel, the two programs take 10 seconds to check 100 pictures. What is the speedup for the parallel solution?
(A) 1
(B) 10
(C) 100
(D) 1,000
26. When run in series, a program that sorts data takes 40 seconds to sort 300 students based on GPA. When running the same program in parallel, the two programs still take 40 seconds to run. What is the speedup for the parallel solution?
(A) 1
(B) 10
(C) 100
(D) 1,000
27. A program to encrypt pictures has different run times based on the resolution of the picture. The following table indicates the run times versus megapixels to process a picture.
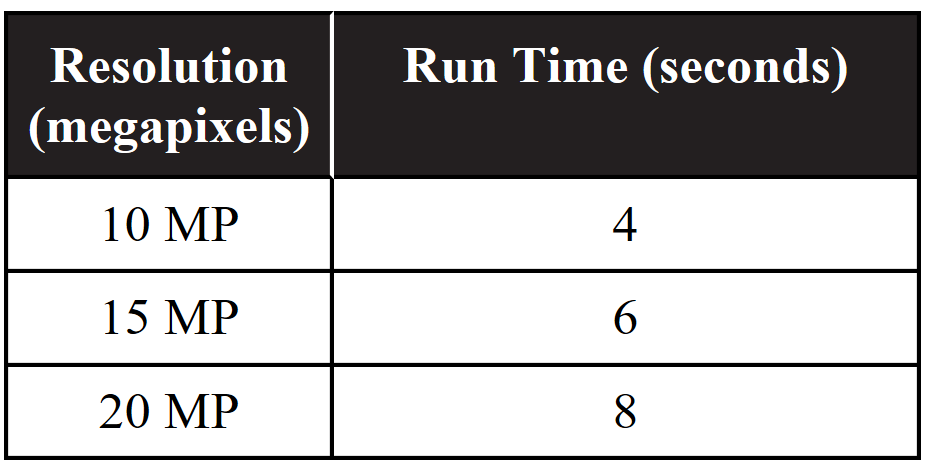
If the program takes 3 seconds for setup and can run processes in parallel using two processors, how long will the series/parallel solution take if two 10 MP, one 15 MP, and one 20 MP pictures need to be processed, assuming the four processes are not dependent on each other?
(A) 5 seconds
(B) 10 seconds
(C) 15 seconds
(D) 20 seconds
28. To predict the path of a hurricane, a programmer needs to use an extremely large volume of data reported by thousands of sensors. This problem is so large and complex that it is impractical to solve on a single computer, so the programmer decides to use a distributed computing solution.
How can a distributed computing solution help speed up the time needed to execute the program?
(A) A distributed computing solution can speed up run time by using multiple computers in parallel.
(B) A distributed computing solution can speed up run time by using multiple computers in series.
(C) A distributed computing solution can speed up run time by using multiple processors in parallel on a single computer.
(D) A distributed computing solution can speed up run time by using multiple processors in series on a single computer.
29. A program that sorts data takes 10 seconds to sort 300 students based on GPA when run on a single computer. When the same program is run using two computers in parallel, the programs takes 5 seconds to run. What is the speedup for the parallel distributed solution?
(A) 1/4
(B) 1/2
(C) 1
(D) 2
IMPACT OF COMPUTING QUESTIONS
1. Which of the following are examples of how global positioning systems (GPS) have affected human navigation? Select two answers.
(A) GPS can be used to calculate the most efficient route to a location.
(B) GPS can be used to inform people of nearby points of interest, such as restaurants.
(C) GPS is used to give people information about points of interest, such as user reviews.
(D) GPS is used to communicate with other drivers or commuters.
2. Which of the following is an example of a sensor network leading to enhanced interaction?
(A) At a theme park, pressure-sensitive pads in the ground cause different aspects of the surrounding area to move when they are walked over.
(B) At a mall, security cameras are used to monitor the activity of patrons.
(C) At a hospital, a digital system is used to schedule doctor-patient interactions, such as checkups and surgical procedures.
(D) At a news station, a digital system is used to send locations to reporting teams.
3. Data transmitted across the internet can contain private data like but not limited to social security numbers, credit card information, birth dates, and medical information. Encryption is essential to help protect personal information. Which features of public key encryption (asymmetric) reduce the risk of having a private key comprised? Select two answers.
(A) The sender and receiver use different keys, thus reducing the risk of the private key being discovered.
(B) The sender and receiver use one public key that is a secret common key.
(C) The private key algorithm cannot be derived from the public key.
(D) The sender in public key encryption must exchange the key with the receiver so that the data can be decrypted.
4. A Caesar cipher uses a number that indicates by how much to offset a letter. For example, a Caesar cipher using 2 as a key would change the word “dog” to the scrambled word “fqi.” The Caesar cipher is an example of which of the following encryption methods?
I. Symmetric key encryption
II. Asymmetric key encryption
III. Public key encryption
(A) I only
(B) II only
(C) II and III only
(D) I, II, and III
5. What would pose the greatest security risk when using public key encryption?
(A) Exposure of the public key
(B) Exposure of the private key
(C) Open standards for encrypting data
(D) The encrypted message being intercepted by a third party
6. What is an example of a way that a “smart grid” could assist with human capabilities?
(A) The grid could control the temperature of an A/C or heating unit directly.
(B) The grid could prevent blackouts altogether.
(C) The grid could distribute power in the most efficient manner possible, maximizing the users that are capable of using power.
(D) The grid could ensure that all computers on it are properly updated.
7. On which of the following areas has the internet had a major effect?
(A) Commerce
(B) Access to information
(C) Education
(D) All of the above
8. Which of the following is a NEGATIVE effect that the web has on productivity?
(A) It is harder to communicate with team members efficiently since this requires an exceptionally high-end internet connection.
(B) It is harder to verify the authenticity of productivity-related communications.
(C) It is easier to access activities that are unrelated to work, creating potential distractions.
(D) It is easier to damage the infrastructure (i.e., network) of a workplace or similar environment.
9. The digital divide refers to differing access to computing devices and the internet based on socioeconomic, geographic, or demographic characteristics. Which of the following is affected negatively by the digital divide?
I. A student unable to access the internet to participate in a distance-learning model put in place by a school district to replace a face-to-face model used for a high school under quarantine.
II. A citizen keeping up on governmental policy announced on the online computing innovation Twitter.
III. A citizen looking for work but companies posting job vacancies online.
(A) I only
(B) II and III only
(C) I and III only
(D) 1, II, and III
10. Which of the following is NOT a determining factor in which side of the digital divide a citizen is on?
(A) Education
(B) Socioeconomic status
(C) Location
(D) Gender
11. Which of the following is LEAST likely to be a phishing attack?
(A) An email claiming to be from the IRS that needs you to update your account by changing a password. The email offers a link to a site that looks identical to the official IRS website.
(B) Receiving an email from a “friend” asking for a reply that seems off.
(C) The IRS is emailing you to update your information by going to a link on the site www.irs.gov.scamcentral.com.
(D) Receiving an email from a hotel asking you to call your credit card company to validate charges made to the hotel.
12. Which of the following is true about a keylogger?
(A) A keylogger can be a piece of software.
(B) A keylogger can be a piece of hardware.
(C) Keyloggers can be installed by malware or can have legitimate uses, such as employers wanting to monitor their employees.
(D) All of the above.
13. Which of the following would be an example of citizen science that utilizes technology?
(A) People take pictures of wildlife using an app that sends information about species and location to researchers.
(B) A specially fitted camera records the hair and eye color of people that are in a certain public square.
(C) An advertising firm tests several potential commercials among members of a focus group and determines how demographics such as gender and race affect reactions.
(D) An app sends basic diagnostic information about errors and crashes to its developer.
14. Which of the following are new models of collaboration that have been created through crowdsourcing? Select two answers.
(A) Small teams and businesses can collaborate with the general public to receive financing for projects.
(B) A moderately sized development team can have members of the general public edit and improve a beta version’s source code.
(C) A development team can invite and pay a small number of potential users to give comments and check for errors on a current beta build.
(D) A project that used proprietary and secure software that was abandoned can be remade and finished by another group made up of members of the general public.
15. Which of the following describes the human component of phishing?
(A) An unethical programmer develops a webpage to look identical to an e-commerce site asking for PII data.
(B) An unethical programmer develops a program to infect a computer to send emails to every person in the victims’ email address list.
(C) An unethical programmer decides which site to impersonate based on current events.
(D) An unethical programmer sets up a system to collect PII data when an unsuspected victim enters the information in a fraudulent site.
16. How has the rise of mobile computing led to new applications?
(A) Since mobile devices are typically always on and connected to the internet throughout the day, applications can assume that a user is capable of using it at any time.
(B) Smartphones make audio-based communication much easier.
(C) Since mobile devices are much smaller than laptops, they are easier to modify from a hardware perspective.
(D) By design, it is easier to modify a mobile device’s firmware than that of a laptop.
17. Which of the following describes an impact that machine learning has had on its given field?
(A) Medicine—machine learning can be used to determine the conditions that indicate a disease, leading to better diagnosis.
(B) Business—algorithms can be produced through machine learning that ensure the efficient use of resources, such as money allocated to advertising.
(C) Science—machine learning can be used to organize data and determine noteworthy values collected in scientific research.
(D) All of the above.
18. How does the ability to share information lead to additional innovation?
(A) Sharing information allows people with identical perspectives to assess and create innovations based on the information.
(B) Sharing information allows people with different perspectives to assess and create different innovations based on the same information.
(C) Sharing information enables different people to develop the same innovation, which proves how strong the underlying idea is.
(D) Sharing information enables people to understand other innovations better.
19. The website Napster was originally created as a hub for peer-to-peer communications that were used to transfer music. The website was shut down after a lawsuit and was later reformatted into a music store. Why might this lawsuit have occurred?
(A) Napster was unable to regulate the transfers to ensure that they did not allow for music piracy.
(B) Napster’s communications were peer to peer, which are inherently illegal.
(C) Napster’s communications were not run through a government server that ensured a lack of malicious activity.
(D) Napster was created before music streaming was considered legal.
20. Which of the following is an ethical concern of software and content licensing?
(A) A license might unfairly damage a buyer’s ability to exercise his or her rights regarding ownership.
(B) A license typically forbids copying the software or content for nonpersonal use.
(C) A license might forbid the use of the software for illegal purposes such as the creation of malware.
(D) None of the above.
21. Suppose that a web browser on a mobile device collects information about login information and geolocation. Is this a security concern?
(A) Yes, because both of these could be used for malicious purposes such as identity theft.
(B) Only the login information is a security concern because geolocation is meaningless on the internet.
(C) Only the geolocation is a security concern because login information is unrelated to personal information.
(D) No, because neither is particularly tied to a person’s identity.
22. The web browser Puffin advertises complete anonymity on the internet by having all website requests run through Puffin’s servers. How does this enable anonymity?
(A) The servers compress the data leaving the server, which ensures that the data will not be decrypted.
(B) The server does not store any information about the client.
(C) The servers act as a proxy, which means that all interactions within a website are done through Puffin’s servers rather than the user’s devices.
(D) The servers are designed to scan data running through them for viruses, which prevents spyware from reaching the client’s computer.
23. How does technology enable the collection and use of information about individuals and groups?
(A) Algorithms translate human thought into information.
(B) Algorithms are used to translate machine code into English and to collect and store the information.
(C) Computers collect data about the actions performed by groups and individuals, which can be processed into usable information using algorithms.
(D) Algorithms can only use text data that is typed by groups and individuals, which then can be processed into usable information using algorithms.
24. Which of the following is an example of targeted advertising being misused?
(A) Not allowing housing and employment advertisements to be shown to certain minorities, which violates two civil rights laws
(B) Sending ads designed to scare a viewer to frighten him or her
(C) Allowing advertisements that deliberately lie to be viewed on the platform
(D) Determining advertisements for a specific person based on information that was obtained through a privacy policy violation
25. The following email was sent to a user of the new social media site Instatok.
Seth, not wanting his Instatok account used by a hacker, confirmed his identity by typing his password, phone number, and social security number on the linked page. Shortly after confirming his account, Seth’s Instatok was taken over by a malicious hacker and new credit cards were opened using his name. What type of cyber attack was most likely used?
(A) Key logger
(B) DDos
(C) TCP
(D) Phishing
26. Ciphers hide the meaning of a message by changing the order of letters. For example, a column cipher writes the message into rows of a matrix. In this case the message “The battle is not lost” is put in a four-column matrix to be encrypted.
The key 2-4-1-3 is used to scramble each row.
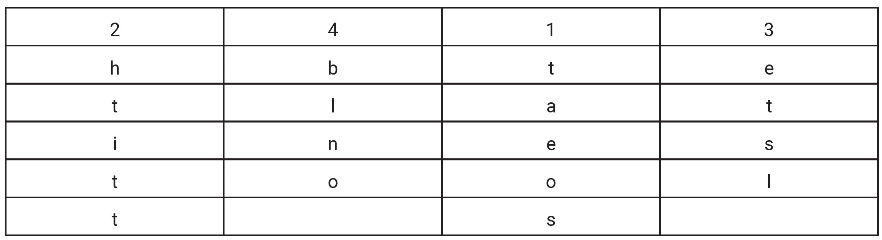
Displaying the letters in the scrambled row major order would result in the following scrambled
message. . .
Result . . . . Hbtetlatinestoolts
To decrypt the message the encrypted message back into a four-column matrix and using the same key to decipher the message would result back to the original message.
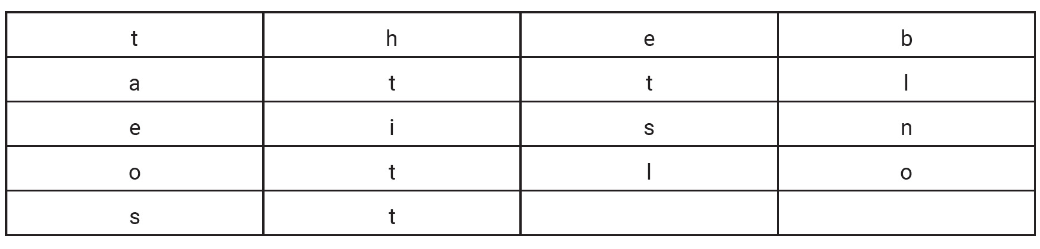
Result . . . . “The battle is not lost”
What type of encryption is demonstrated above?
(A) Public key encryption
(B) Symmetric key encryption
(C) Asymmetric key encryption
(D) Brute-force encryption
27. Which of the following is NOT a consequence of the disparity in online access?
(A) Rural areas are less likely to receive internet access because of the high cost of laying a connection.
(B) Companies that are not listed online may have a harder time gaining a consumer base.
(C) People who live in poorer regions are less able to communicate because they do not have access to some methods of communication.
(D) Political supporters who are too poor to access the internet are less able to communicate with each other and their representatives.
28. How has the rise of mobile and wireless networking impacted innovation?
(A) Devices can be controlled remotely.
(B) Finished innovations can be distributed to any customer instantaneously.
(C) An innovation that typically requires the use of a wire can be redesigned to be wireless with little effort.
(D) Innovations can be used by more devices in more locations.
29. Which of the following is NOT an issue raised by the global distribution of computing resources?
(A) How would a developing computer market be affected if it had less powerful computers than the rest of the world?
(B) What impact does the lack of internet in some areas have on their well-being?
(C) If a country suddenly gains a large amount of computing-related resources, how will that affect the balance of world power?
(D) If a new type of hardware can be created with any computing resources, how will that affect the price of the hardware?
30. Which of the following is an effect that the digital divide has on the given group?
(A) Teachers without computers are unable to grade work at all.
(B) Students without computers have a harder time accessing resources and programs for schoolwork.
(C) Mathematicians without computers cannot evaluate calculus expressions such as integrals.
(D) Taxi and carpool drivers without computers cannot find efficient routes.
31. Which of the following is a method of search refinement that is based on Boolean logic?
(A) Excluding the results of a genre
(B) Filtering results by decade published
(C) Including only results with specific data values
(D) All of the above require Boolean logic
32. Which of the following are ways that technology has affected plagiarism? Select two answers.
(A) Copying information verbatim is much easier since it can be done using cut-and- paste commands.
(B) It is easier to plagiarize out of sloth since computers cannot expedite the process of citation.
(C) It is easier to detect plagiarism through the use of services that automatically check text against the web.
(D) Copying information verbatim is much harder due to the use of web scripts that prevent the copying of website material.
33. Which of the following is an example of cybersecurity being implemented through hardware?
(A) To protect against phishing links, an email filter warns users that the email was sent from a suspicious address.
(B) To protect against the Meltdown and Spectre vulnerabilities, Intel redesigned their processors to better separate processes and privilege levels.
(C) To protect against the Heartbleed vulnerability, the cryptography toolkit OpenSSL was redesigned to ignore data requests that would result in a buffer overflow.
(D) To protect against malicious programs, all files downloaded to a computer are scanned for viruses by an antivirus program.
34. Which of the following is an example of the effects that cyber attacks can have on the world at large?
(A) Theft of personal information such as financial information
(B) Interruption of essential governmental services
(C) Loss or theft of confidential business work
(D) All of the above
35. A common way that DDoS attacks are propagated is via botnets. These are networks created by infected machines that secretly perform commands for the malicious purpose without informing their users. Why might using botnets be preferred by cyber criminals to implement a DDoS attack? Select two answers.
(A) A botnet is the only way to ensure that the attack comes from many different IP addresses.
(B) Botnets do not require the attacker to be revealed since computers in a botnet do not communicate with a centralized server.
(C) Since botnets can contain many different computers, DDoS attacks can be made much more powerful.
(D) It is easier to program attacks with botnets as opposed to without them.
36. Which of the following is NOT an example of a human component within a cyber attack?
(A) An advertisement tells users to download a certain antivirus program, which is really a virus or piece of spyware.
(B) A website, which has been hacked, utilizes backdoor protocols in the browser or operating system to download and run a virus secretly.
(C) A user is sent an email containing a link to an “interesting article,” which is a website that utilizes backdoor protocols in the browser or operating system to download and run malware secretly.
(D) A user is sent an email with an attached “PDF file,” which is really an executable file that installs and runs malware.
37. How is math utilized in cryptography?
(A) The length of a string determines whether it should be encrypted.
(B) Individual bits are given new values that are randomly generated using mathematical principles.
(C) Bits and group of bits (e.g., characters) are modified by using mathematical and algebraic principles.
(D) Math is not used; cryptographic algorithms are purely logic based.
38. How do open standards ensure the security of encrypted data?
(A) Open standards have their flaws publicly documented, which means there are more people that can repair or mitigate those flaws.
(B) Open standards are always backed by large corporations that can ensure the security through resources.
(C) It is illegal to crack open standards, so security is guaranteed.
(D) It is impossible to crack open standards because the specifications are private.
39. Suppose that a certain encryption program works by replacing every letter in a message with a letter n places after it. Numbers follow a similar pattern, but other characters such as spaces are unaffected. Thus, “ab d7 %” would become “bc e8 %” if n = 1. (If the calculated place number is too high, it rolls over to the beginning.) Could this be decrypted using symmetric encryption? If so, what would be the encryption key?
(A) Yes, the key would be equal to n* 1.5.
(B) Yes, the key would be equal to n.
(C) Yes, the key would be equal to the numeric value of the first encrypted character.
(D) No.
40. What is the advantage of using public key encryption for encrypted communications?
(A) A message cannot be decrypted without permission from the receiver.
(B) Anyone can encrypt and decrypt a message, but he or she needs a key from the receiver.
(C) A message can be encrypted only by someone who knows the receiver, regardless of whether he or she has a key.
(D) Anyone can encrypt a message to the receiver without having to know how to decrypt it.



.png)
.png)
.png)
.png)


