Diagnostic Test - AP Computer Science Principles Premium 2024
Diagnostic Test
TIME: 120 MINUTE
70 QUESTIONS

1. Consider the following code segment, which uses the variables a and c.
a ← 3
a ← a + 5
c ← 3
a ← c + a
DISPLAY(a)
DISPLAY(c)
What is displayed when running the code segment?
(A) 3 3
(B) 3 8
(C) 11 3
(D) 3 11
2. When writing a program, what is true about program documentation?
I. Program documentation is useful while writing the program.
II. Program documentation is useful after the program is written.
III. Program documentation is not useful when run speed is a factor.
(A) I only
(B) I and II only
(C) II only
(D) I, II, and III
3. An image stored on a computer contains pixels that represent how bright the red, green, and blue values are. The most common format for pixels is to represent the red, green, and blue, using 8 bits, which vary from 0 to 255. If the current red value is 10011101, what would be the new value in binary if the red value is increased by 4 in decimal?
(A) 157BIN
(B) 0100BIN
(C) 10011111BIN
(D) 10100001BIN
4. A programmer is writing software for a diverse set of users. While the program runs, the programmer wants to meet the needs of all her customers and reduce potential bias in her algorithms. What would be the benefit of collaborating with colleagues?
(A) When collaborating, too many people try to lead the group and not enough members are willing to take a backseat, which will delay the release of the program.
(B) Conflicts in the working styles within the group will decrease staff morale.
(C) With multiple people looking over code, errors can be quickly fixed.
(D) Multiple people with different life experiences can see the code and give perspective on the ways the original programmer can decrease bias.
5. Which of the following examples LEAST likely indicates a phishing attack?
(A) An email indicates that a password is expiring and asks you to click a link to renew your password.
(B) An email from a familiar company, which has the exact look of previous emails from this company, reports that the current credit card information on file has expired and has a link for you to reenter credit card information.
(C) An email from the IRS contains the correct IRS logo and asks you to submit your social security number so the IRS can mail an additional tax refund. Additionally, the email contains a warning that if this information is not filled out within 30 days, the refund will be lost.
(D) An email from your credit card company with the correct bank logo indicates that there has been unusual activity on your credit card and to call the number on your card to confirm the purchase.
6. With the lowering of the digital divide and more products using the internet, the world is running out of IP addresses. The current plan is to switch from IPv4, which holds 32 bits, to IPv6, which holds 128 bits.
With the increase from 32 bits to 128 bits, what is the resulting increase in possible IP addresses?
(A) 2 × 96
(B) 296
(C) 962
(D) 96
7. What type of error will the following procedure cause?
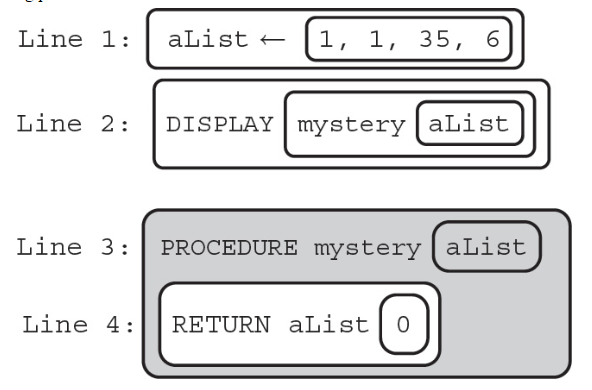
(A) Logic error on line 1
(B) Syntax error on line 4
(C) Runtime error on line 4
(D) Overflow error on line 1
8. What will the following code display?
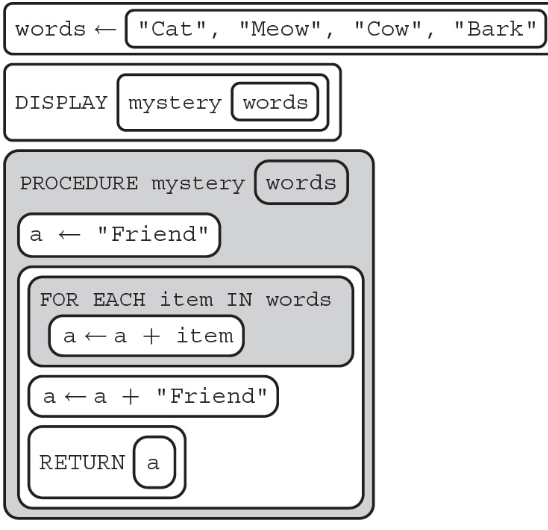
(A) Friend
(B) FriendFriend
(C) FriendCatMeowCowBarkFriend
(D) a
9. A computer can use 6 bits to store non-negative numbers. Which of the following will NOT give an overflow error?
I. 54
II. 63
III. 64
IV. 89
(A) All of the above
(B) I, II, and IV only
(C) I and III only
(D) I and II only
Questions 10–14 refer to the information below.
A restaurant uses phones to take reservations and to place to-go orders. The restaurant is planning to update its system to provide more options to customers while decreasing the ordering time. Customers will now interact with a website instead of an actual person.
The upgraded system (but not the original system) stores all information from the web interactions for future references. This includes food items ordered, address, telephone number, and credit card info.
The original system and the upgraded system are described in the following flowcharts. Each flowchart uses the following blocks.
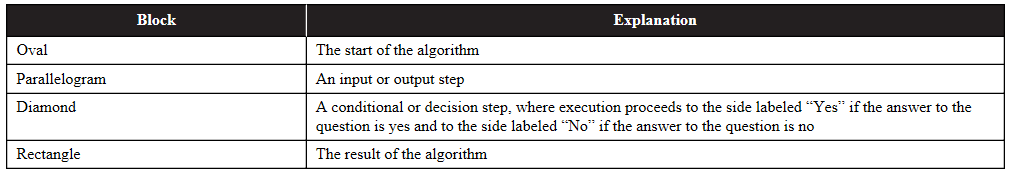
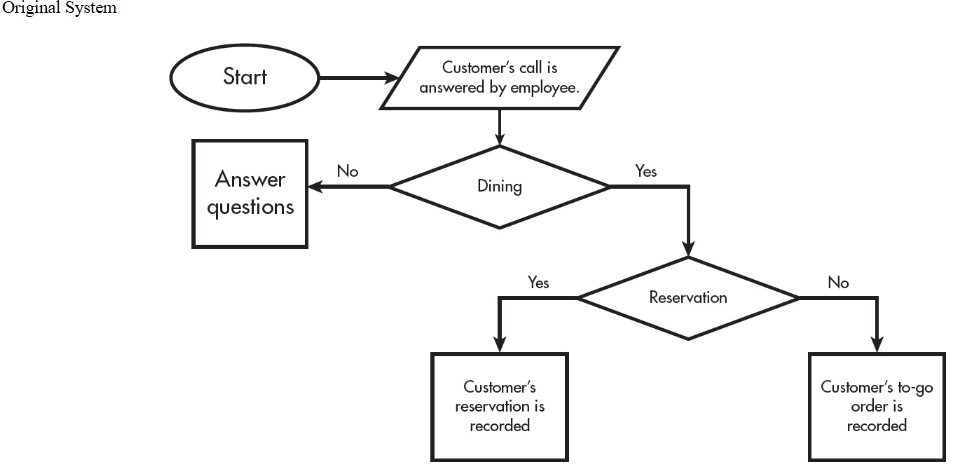
Upgraded System
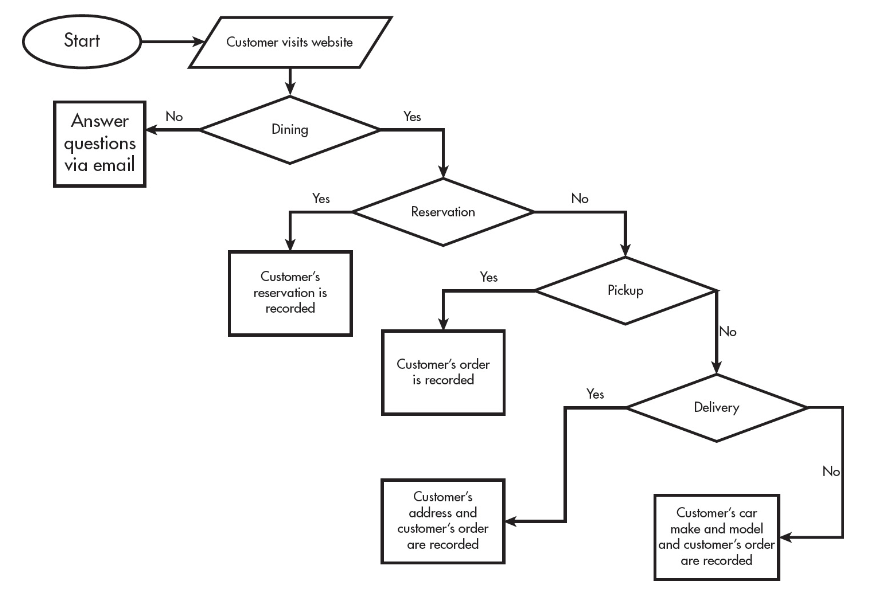
10. Which of the following input data is needed by the upgraded system but was NOT needed by the original system?
(A) Name
(B) Order
(C) Time of pickup or reservation
(D) Customer’s car make and model
11. The upgraded system uses data not supplied by the customer. The new site is supposed to increase sales by suggesting products based on the order (would you like fries with that?) and decreasing processing time. Which of the following data is LEAST likely to be included in the web-based ordering system?
(A) IP address of the customer
(B) Previous list of food orders
(C) A list of popular items frequently added to orders
(D) Time to prepare order
12. Which of the following is MOST likely a data privacy concern of the upgraded system?
(A) Storing credit card information can provide the user with a better experience by auto filling in data to speed up ordering.
(B) Customers are more likely to make reservations.
(C) Storing customer information will increase the likelihood of a phishing attack by rogue hackers.
(D) Customers’ personal data can be compromised if hackers gain access into the ordering system.
13. Of the following potential benefits, which is LEAST likely to be provided by the upgraded system?
(A) Customers being more likely to order to-go orders
(B) An increase in food per order
(C) An increase in awareness of the restaurant
(D) A decrease in incorrect orders and delivery addresses
14. Which of the following may be an unintended effect of the upgraded system?
(A) Reservations for the restaurant will increase.
(B) Customers giving the suggested tips will increase income for the staff.
(C) Reservations will be primarily made by customers who can afford internet access.
(D) Repeat business will increase.
______________________________________________________________________
(A) Phishing attack
(B) Keylogging
(C) Rogue access point
(D) Packet metadata
16. What can replace to complete the last column of the table?
.png)
(A) A AND B
(B) A OR B
(C) NOT(A OR B)
(D) A AND NOT(B)
17. The diagram below shows a circuit composed of logic gates. Each gate takes two inputs and produces a single output. What will the algorithm produce?
.png)
(A) TRUE when both A and B are TRUE only.
(B) TRUE when A is TRUE and B is FALSE.
(C) Always TRUE regardless of the values of A and B.
(D) Always FALSE regardless of the values of A and B.
18. Consider the following procedure called mystery, which is intended to display the number of times a number target appears in a list.
Which of the following best describes the behavior of the procedure?
.png)
Select two answers.
(A) The program correctly displays the count if the target is not in the list.
(B) The program never correctly displays the correct value for count.
(C) The program correctly displays the count if the target appears once in the list and also at the end of the list.
(D) The program always correctly displays the correct value for count.
19. Two lists, list1 and list2, contain unique eight-number student IDs for Lake Brantley High School. An administrator for the school wants to create one list so the one list can be searched using a binary search.
The following abstractions are available to create the new searchable list.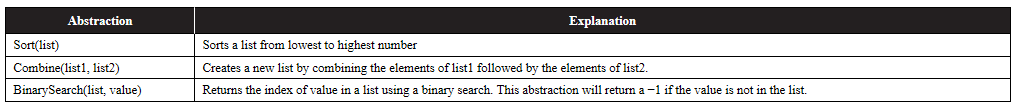
Which of the following code segments will correctly search for a value using a binary search?
(A) list1 ← Sort(list1)
list2 ← Sort(list2)
resultList ← combine(list1, list2)
BinarySearch(resultList, value)
(B) resultList ← combine(list1, list2)
BinarySearch(resultList, value)
(C) resultList ← combine(list1, list2)
resultList ← Sort(resultList)
BinarySearch(resultList, value)
(D) BinarySearch(list1, value)
BinarySearch(list2, value)
20. The question below uses a robot in a grid of squares. The robot is represented as a triangle, which is initially facing toward the top of the grid.
.png)
Which of the following codes would move the robot one square forward 1% of the time?
Select two answers.
(A) IF(RANDOM(1, 100) = 4)
MOVE_FORWARD()
(B) IF(RANDOM(0, 100) = 4)
MOVE_FORWARD()
(C) IF(RANDOM(1, 100) < 2)
MOVE_FORWARD()
(D) IF(RANDOM(1, 100) ≤ 2)
MOVE_FORWARD()
21. At one of the lowest levels of abstraction, digital data are represented in binary that is a combination of digital zeros and ones.
The number “1001001” in binary is equivalent to what number when converted to base 10 (DEC)?
(A) 37
(B) 45
(C) 73
(D) 86
22. Using a binary search, how many iterations would it take to find the letter w? str ← [a, b, c, d, e, f, g, h, i, j, k, l, m, n, o, p, q, r, s, t, u, v, w, x, y, z]
(A) 2
(B) 3
(C) 23
(D) 24
23. Using a linear search, how many iterations would it take to find the letter x? str ← [a, b, c, d, e, f, g, h, i, j, k, l, m, n, o, p, q, r, s, t, u, v, w, x, y, z]
(A) 3
(B) 4
(C) 23
(D) 24
24. A flowchart is a way to visually represent an algorithm. The flowchart below uses the following building blocks.
.png) What will the below algorithm display?
What will the below algorithm display?
.png)
(A) 6
(B) 8
(C) 10
(D) No numbers due to an infinite loop
25. Sequencing, selection, and iteration are building blocks of algorithms. Which of the following is considered selection?
(A) The application of each step of an algorithm in the order in which the statements are given
(B) Using a Boolean condition to determine which part of an algorithm is used
(C) The repetition of part of an algorithm until a condition is met or for a specified number of times
(D) The decision to use a high-level computing language to evaluate an algorithm
26. If your algorithm needs to search through a list of unsorted words, what type of search would you use?
(A) Linear search
(B) Binary search
(C) Bubble sort
(D) Insertion sort
27. The code segment below is a test program intended to diagnose the disease held by a young child based on a user’s entry of fatigue_present and has_cough.
.png)
If all variables have the value TRUE, what is displayed as a result of running the segments as shown?
(A) Flu
(B) Cold
(C) Flu Healthy
(D) Flu Cold Healthy
28. Which of the following trade-offs is true when representing information as digital data?
I. An analog signal must be sampled and turned into numbers that are then stored digitally as bits.
II. Reading data and updating data have different storage requirements.
III. Lossy data compression reduces the number of bits stored or transmitted at the cost of being able to reconstruct only an approximation of the original.
(A) I and II only
(B) II and III only
(C) I and III only
(D) I, II, and III
29. What is a possible value that can be displayed after this code segment is run?
.png)
(A) −11
(B) −5
(C) 5
(D) 20
30. This is a web of devices connected through the fault-tolerant redundant internet.
.png)
What is the minimum number of other devices that device C must connect with to communicate with D?
(A) 1
(B) 2
(C) 3
(D) 4
31. What will the following code segment display?
.png)
(A) 1 4 7 10 13
(B) 35
(C) 13 10 7 4 1
(D) 1 4 7 1 4 7
32. What will the following code segment display?
.png)
(A) Nothing will be displayed due to an error.
(B) 3
(C) 6
(D) 11
33. What is displayed after running the following algorithm?
.png)
(A) −98
(B) −4
(C) 0
(D) 76
34. What is displayed after running the following algorithm?
.png)
(A) −98
(B) −76
(C) −1
(D) 0
35. What is displayed after running the following algorithm?
.png)
(A) −98
(B) −76
(C) −1
(D) 0
36. The procedure getTotalEven is intended to display the sum of all the even numbers in the list. Which of the following procedures will correctly display the total of the even numbers in the list?
(A)
.png)
(B)
.png)
(C)
.png)
(D)
.png)
37. What is the percentage chance that the robot lands on the star?
.png)
.png)
(A) 0%
(B) 25%
(C) 50%
(D) 100%
38. What is displayed after running the following algorithm?
.png)
(A) 35
(B) 43
(C) 68
(D) 73
39. The following question uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the bottom-left square and facing right.
Which of the following code segments places the robot in the gray goal?
.png)
.png)
(A) MoveForward(4)
TurnRight(1)
MoveForward(4)
TurnRight(1)
MoveForward(1)
TurnRight(1)
MoveForward(1)
(B) MoveForward(4)
TurnRight(3)
MoveForward(4)
TurnRight(1)
MoveForward(1)
TurnRight(3)
MoveForward(1)
(C) MoveForward(3)
TurnRight(3)
MoveForward(3)
TurnRight(1)
MoveForward(1)
TurnRight(3)
MoveForward(1)
(D) MoveForward(3)
TurnRight(3)
MoveForward(3)
TurnRight(3)
MoveForward(1)
TurnRight(3)
MoveForward(1)
40. A smartphone stores the following data for each picture taken using the phone:
The location where the photo was taken
The number of photos taken at the location
The date and time the photo was taken
The filename of the photo
Which of the following can be determined using the metadata described above?
I. How many photos were taken at Walt Disney World
II. The name of the person who took the most recent photo
III. Whether people tend to take more photos on the weekend than during the week
(A) I only
(B) III only
(C) I and III only
(D) I, II, and III
41. How many lines need to be cut to completely isolate A?
.png)
(A) 1 line
(B) 3 lines
(C) 4 lines
(D) 5 lines
42. The following algorithm is run with two data structures.
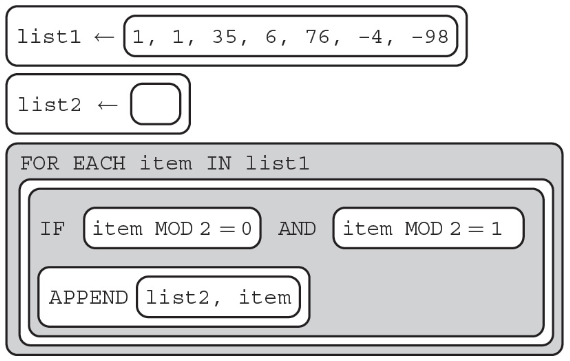
What elements does list2 contain after the algorithm is run?
(A) [ ]
(B) [−4, −98]
(C) [1, 35, 6, 76, −4, −98]
(D) [6, 4, 98]
43. A certain computer has a single central processing unit (CPU). The following table indicates the amount of time the computer takes to execute processes using a single CPU. Assume none of the processes are dependent on any other process.

Which of the following best approximates the minimum possible time to run all three processes in series?
(A) 2 seconds
(B) 6 seconds
(C) 8 seconds
(D) 16 seconds
44. A small team of butterfly researchers are working on a project that monitors the success rate of the caterpillars to butterfly transition. Which of the following best explains why citizen science is considered useful for this project?
Select two answers.
(A) Distributed individuals are more likely able to count a larger number of caterpillars and butterflies over a larger area than a small team of researchers.
(B) The reach of social media can be used to allow interested individuals from different locations to contribute to this project.
(C) The general public are more likely to accurately identify the type of caterpillar.
(D) Counting caterpillars and butterflies is inherently too complex for citizen scientists.
45. In a centralized internet, what is the minimum number of nodes needed to disable the internet?
(A) 1
(B) 7
(C) 11,356
(D) 12,587
46. A certain computer has two identical processors that can run in parallel. Each processor can run only one process at a time, and each process must be executed on a single processor. In this problem, processes four and five must be run sequentially while processes one, two, and three can all run in parallel. The following table indicates the amount of time each process takes to execute on a single processor.
 Which of the following best approximates the minimum possible time to run the five processes?
Which of the following best approximates the minimum possible time to run the five processes?
(A) 5 seconds
(B) 9 seconds
(C) 13 seconds
(D) 18 seconds
47. Errors in Microsoft Windows are often displayed with binary error codes. If this number is converted into a decimal, it can be used by certain utilities to diagnose the problem with the computer.
If a stop error (i.e., a “Blue Screen of Death”) returns the error code 10001111, what is the error? (Ignore the “0x” at the start; this is a signal that the number is in hexadecimal.)
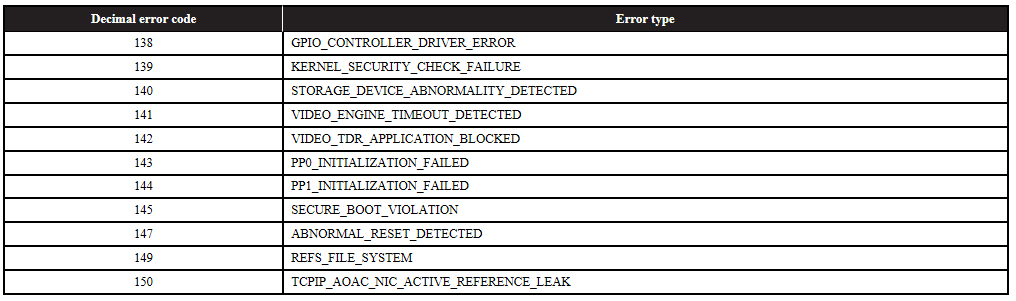
(A) TCPIP_AOAC_NIC_ACTIVE_REFERENCE_LEAK
(B) PP1_INITIALIZATION_FAILED
(C) PP0_INITIALIZATION_FAILED
(D) VIDEO_TDR_APPLICATION_BLOCKED
48. How is the word “Mississippi” stored in a computer’s memory?
(A) As a group of decimal numbers representing each letter.
(B) As a group of binary numbers representing each letter.
(C) As a single binary number representing the word as a whole.
(D) As a group of characters that cannot be broken down any further.
49. What error has occurred if the phrase “Error” is displayed?
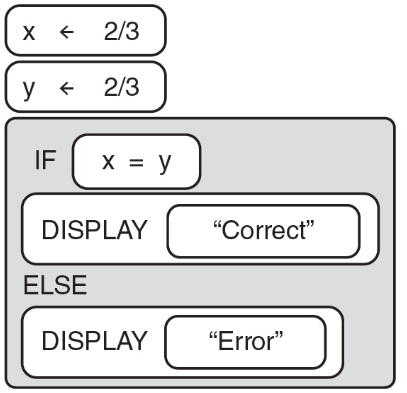
(A) Roundoff error
(B) Overflow error
(C) Logical error
(D) 2/3 will always equal 2/3
50. A programmer is planning to make a program that allows a company to organize its employees by name, ID number, and salary. Suppose the programmer is making a procedure called newEntry that takes in this data to create a new entry.
Which of the following would be a good header for the procedure?
(A) newEntry(name, idNo, salary)
(B) newEntry(n, i, s)
(C) newEntry(id, n, s, n)
(D) newEntry(name, idNo)
51. Why is it best to use an iterative and incremental process of program development?
(A) It is easier to find errors because any error-causing code is usually in the last change.
(B) It is faster because it requires less testing.
(C) It always produces the desired output regardless of the point in the development cycle.
(D) It requires less processor time at all stages of development.
52. How many times does the inner loop iterate in the following?
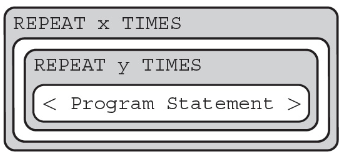
(A) 2xy
(B) y × (x −1)
(C) 2x
(D) x × y
53. The figure below uses a robot in a grid of squares. The robot is represented as a triangle, which is initially in the bottom-left square and facing right. Which of the following algorithms will place the robot into the gray square?
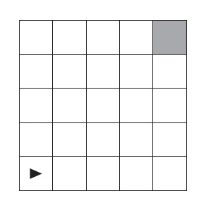
(A)
ROTATE_LEFT()
MOVE_FORWARD()
MOVE_FORWARD()
MOVE_FORWARD()
MOVE_FORWARD()
ROTATE_LEFT()
MOVE_FORWARD()
MOVE_FORWARD()
MOVE_FORWARD()
MOVE_FORWARD()
(B)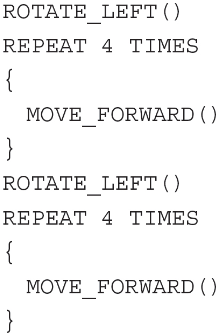
(C)
(D)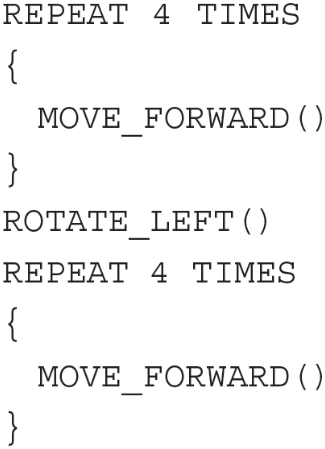
54. What percentage of the time will the following program display an even number? DISPLAY(RANDOM(1,10))
(A) 0%
(B) 10%
(C) 40%
(D) 50%
55. Which of the following codes performs the following?
Step 1: A user enters a number.
Step 2: If the number is between 0 and 10 inclusive, write the word Waffles.
Step 3: If the number is between 11 and 20 inclusive, write the word Novack.
Step 4: If it is any other number, write the word Benji.
(A) num ← input()
IF(num > 0 and num < 10)
DISPLAY(“Waffles”)
IF(num > 10 and num < 20)
DISPLAY(“Novack”)
ELSE
DISPLAY(“Benji”)
(B) num ← input()
IF(num ≥ 0 and num ≤ 10)
DISPLAY(“Waffles”)
IF(num ≥ 11 and num ≤ 20)
DISPLAY(“Novack”)
ELSE
DISPLAY(“Benji”)
(C) num ← input()
IF(num ≥ 0 and num ≤ 10)
DISPLAY(“Waffles”)
ELSE(num ≥ 11 and num ≤ 20)
DISPLAY(“Novack”)
DISPLAY(“Benji”)
(D) num ← input()
IF(num ≥ 0 and num ≤ 10)
DISPLAY(“Waffles”)
IF(num ≥ 11 and num ≤ 20)
DISPLAY(“Novack”)
IF(num > 20)
DISPLAY(“Benji”)
56. In general, which of the following are NOT advantages of using computer simulations?
Select two answers.
(A) Simulations are more expensive to use and harder to make changes to.
(B) The parameters of a simulation can be altered easily to test varying circumstances.
(C) Simulations can run faster than real-time experiments and thus save time.
(D) Information gathered by simulations is more accurate than that gathered by real-world experiments.
57. Which of the following describes a lossy transformation of digital data?
I. Compressing an image file into a smaller resolution image so the image can easily be emailed
II. Inverting the colors of an image by subtracting each RGB value from 255
III. Converting an image by averaging its RGB values and assigning the new value to a shade of gray ranging from white to black
(A) I only
(B) II only
(C) I and II only
(D) I and III only
58. Which of the expressions are equivalent to the Boolean expression NOT(num < 13)?
(A) num > 13 OR num = 13
(B) num > 13
(C) num < 13 AND num = 13
(D) num > 13 AND num = 13
59. The following are steps data take as the data travel across the internet.
I. Data are chopped into chunks called packets.
II. Packets are reassembled into a coherent message.
III. Packets are routed throughout the internet.
IV. Packets go through internet service providers (ISPs) to access the internet.
Which of the following is the correct path data take when the data travel from one device to another device through the internet?
(A) IV → II → I → III
(B) I → III → IV → II
(C) I → IV → II → III
(D) I → IV → III → II
60. An algorithm has n number of steps. Which of the following would NOT be considered a reasonable number of steps?
(A) n
(B) 4n + 8n2
(C) 100n4
(D) 3n
61. A social media company maintains a database of information that contains the following information about their users.
■ Username
■ Average time per day spent on the application
■ Age of user
■ Gender of user
■ What area of the application the user spent the most time in
Which of the following additional pieces of information would NOT be most useful in determining if current events determine the preferences of the users?
(A) Most viewed pages
(B) Date of use
(C) Email address
(D) Location of user
62. Which of the following are benefits to having information be easy to access?
I. Information can be easily found by researchers, which can improve experimental and investigational findings.
II. Information can be easily found by students, who can use it to improve their understanding of a topic.
III. Information can be easily checked by third parties, which ensures that it is always correct and up-to-date.
(A) I only
(B) I and II
(C) II only
(D) I, II, and III
63. Most coding languages enable programmers to include a source file in the form of abstractions. For example, in C++, the command #in-clude <isotream> grants the program access to basic input/output commands. Why would such a feature be useful in a language?
(A) It enables programmers to increase the level of complexity of the program and just focus on the current program.
(B) It ensures programmers can modify the language’s functions.
(C) It enables features to be used in multiple programs, which reduces the complexity of the code by allowing for reuse.
(D) It is a useful reminder to copy the entire source file at a later time.
64. Why would a heuristic analysis be useful in an antivirus program?
(A) Heuristic solutions are used when an exact solutions is not needed. By not checking every file and instead just investigating the most likely infected programs, it will decrease the run time of antivirus programs.
(B) A heuristic solution will fully guarantee that the entire computer will be virus free.
(C) It is able to pick out viruses without selecting false positives and without requiring a full file scan at all.
(D) It is more capable of separating dangerous viruses from simple adware.
65. “Boids” is a flocking algorithm that is used to determine the direction of objects in a moving population. It is built on three principles:
I. Separation: steer to keep local flock mates at a certain distance
II. Alignment: steer toward the average heading
III. Cohesion: steer toward the center of the flock
Suppose that a programmer is creating a method called findBoidHeading that calculates the heading of an individual boid in the flock. findBoidHeading takes in a data structure of the other boids in the program.
The following commands are used on Boid objects. Assume that the name is representative of the function. Which might be useful in findBoidHeading?
Select two answers.
(A) getVelocity
(B) getDate
(C) getShape
(D) getHeading
66. A simulation for a coin flip should result in 50% heads and 50% tails. Select two answers that could replace the missing condition.
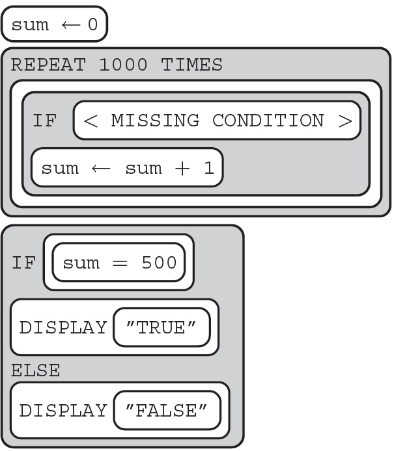
Select two answers.
(A) RANDOM(1,5) < 2
(B) RANDOM(1,10) < 6
(C) RANDOM(1,2) = 2
(D) RANDOM(6,10) < 6
67. A program for children is designed to display a math problem and let the user input what he or she believes to be the answer. What data transformations are undergone at the most basic level of the program?
Select two answers.
(A) The keyboard number entry is converted from number to machine code.
(B) The keyboard entry is converted from text to number to hexadecimal.
(C) The problem is converted from decimal to text.
(D) The solution is converted from machine code to decimal.
68. Why is it more effective to use abstractions in a program than to repeat code?
Select two answers.
(A) Abstractions make it harder to edit because every extraction is saved on a distinct file.
(B) Abstractions simplify editing by requiring only one edit to the abstraction rather than to every instance of the code.
(C) Using abstractions takes up less space than repeating code, which makes the program easier to read.
(D) Abstractions are guaranteed to work in every instance, and if they work once, they are used.
69. Which of the following is NOT a possible answer?
Select two answers.
DISPLAY (RANDOM(1, 4) + RANDOM(2, 5))
(A) 1
(B) 5
(C) 6
(D) 10
70. The algorithm below displays TRUE 60% of time.
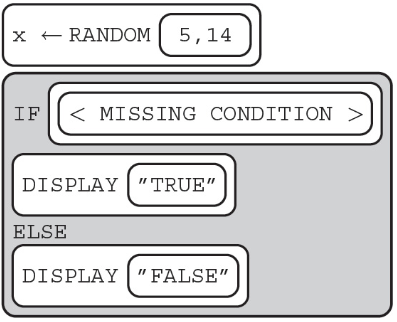
What can replace so that the algorithm works as intended?
Select two answers.
(A) x > 8
(B) x <= 10
(C) x > 10
(D) x >= 10




